virtualization-based security (VBS)
What is virtualization-based security (VBS)?
Virtualization-based security (VBS) is a technology that abstracts computer processes from the underlying operating system (OS) and, in some cases, hardware. It isolates these processes from one another, with the goal of protecting the operating system and device against malware and other attacks.
VBS is the idea of creating an isolated virtual environment and enforcing certain restrictions in order to protect system resources and security solutions (like user login credentials) from vulnerabilities in the OS and exploits like malware. The isolated environment is a section of the main memory that is separated from the rest of the OS. It is also the "root of trust" of the OS.
VBS relies on the Windows hypervisor to create the isolated environment. The hypervisor assumes that Windows could be compromised, say, by malicious code. Based on this assumption, it aims to protect key system resources. To do this, it enables hardware virtualization, and creates virtual machines (VMs) that host system processes and store their data, instead of running those processes directly on the computer's operating system. The premise of VBS is that if an isolated process or application is attacked, the attack cannot spread outside of the VM. An attacker cannot exploit a vulnerability in one process to steal data from another application or seize the whole computer with ransomware, for example.
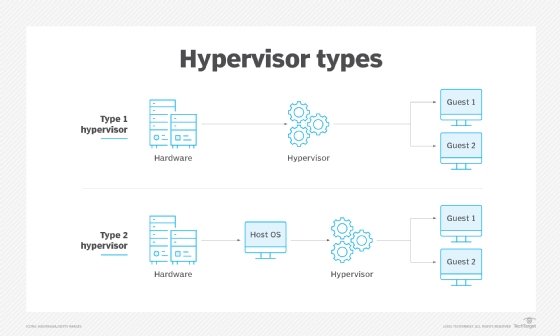
What is virtualization-based security in Windows?
Microsoft first included virtualization-based security in Windows 10 with the introduction of its Windows Defender Device Guard and Credential Guard features. Device Guard and Credential Guard utilize Virtual Secure Mode (VSM), a specific feature of virtualization-based security in Windows 10. VSM uses the Microsoft Hyper-V hypervisor, installed directly on the computer's hardware, to run specific processes and store their data independently of the operating system.
Device Guard is a set of three features -- Configurable Code Integrity, VSM Protected Code Integrity and Platform and UEFI Secure Boot -- that prevent untrusted code from running on a Windows 10 machine. These features ensure that only trusted code and signed, verified firmware can run on the computer, and they allow IT administrators to isolate specific processes for an added layer of protection. Credential Guard uses VSM to isolate and secure user logins, passwords and other authentication data, to prevent unauthorized access to the machine and other systems.
VBS is supported on all versions of Windows beginning with Windows 10 and Windows Server 2016. Windows 11 also supports VBS. In Windows 11, VBS and its key security features like memory integrity are on by default. As with Windows 10, VBS in Windows 11 creates an isolated section of memory where various security solutions can be securely stored. In doing so, the environment acts as the root of trust for the OS. VBS ensures that only those resources residing inside this environment are trusted.
Resources and security solutions protected by VBS
VBS and the Windows hypervisor aim to protect several system and OS resources and security solutions. One such resource is model-specific registers (MSRs). MSRs are control registers in the processor that are commonly used for debugging, performance monitoring and for controlling certain aspects of the processor's behavior.
The compromise of MSRs and altering the settings they control could compromise the entire system. When this happens, the system's behavior may change in undesirable ways or a threat actor may gain unauthorized access to the system or its security assets.
To prevent such issues, the hypervisor uses VBS. With VBS, the hypervisor protects MSRs from malicious kernel mode code and prevents their misuse by doing the following:
- Monitoring and controlling access to all MSRs.
- Allowing the kernel mode code to access only those MSRs that are known to be safe.
- Blocking access to unknown (to the hypervisor) MSRs.
- Flagging instances of attempted access to blocked MSRs by logging an event to the Windows System log in Event Viewer.
VBS also protects authenticated user credentials and the code responsible for Windows security by placing them in the secure virtual environment.
Virtualization-based security and memory integrity
Memory integrity is a VBS feature in Windows OS. Once the hypervisor creates the isolated virtual environment, memory integrity runs kernel mode code integrity within this environment to prevent untrusted drivers or system files from being loaded into system memory. Consequently, it protects the OS and prevents malware from compromising the Windows kernel.
Memory integrity also ensures that kernel memory pages execute only after passing code integrity checks inside the secure runtime environment. Additionally, it prevents the executable code pages from being modified and the modified memory from being executed. This is how it restricts kernel memory allocations and prevents the system from being compromised.
Requirements to run VBS in Windows
To enable and run VBS in Windows, certain components must be properly configured. The most important is the Windows hypervisor. Also, the processor must support virtualization with second-level address translation.
Further, all DMA-capable I/O devices must be behind an Input-Output Memory Management Unit and all system firmware must harden System Management Mode code as per the Windows SMM Security Mitigation Table (WMST). All Unified Extensible Firmware Interface firmware must segregate and report EFI runtime memory ranges for code and data, and also include EFI page protections (for example, executable UEFI memory must be read only and writable memory must not be executable).
Another important requirement is that all system drivers must be tested to ensure compatibility with memory integrity. Also, Secure Memory Overwrite Request revision 2 must be implemented to guard the system against advanced memory attacks.
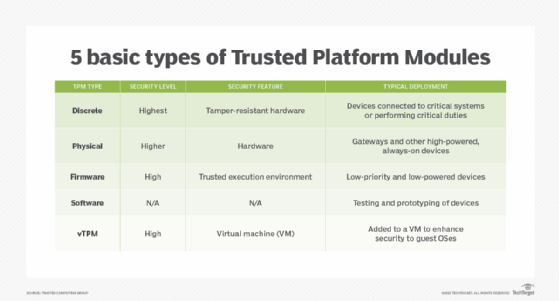
Finally, Microsoft recommends (but does not mandate) implementing a Trusted Platform Module to provide hardware-based security.
How to check if VBS is enabled in Windows 10 or 11
In Windows 10 and 11, VBS is usually turned on by default. However, admins can confirm if it is enabled by following this process:
- Search for the System Information app in Windows search.
- Open the app.
- Scroll down to the "Virtualization-based security" row.
- If it says "running," VBS is enabled.
How to disable VBS/HVCI in Windows 10 or 11
Its security benefits notwithstanding, enabling VBS in Windows 10 and 11 can slow down system performance. Disabling the feature can improve performance -- albeit at the cost of exposing security solutions to vulnerabilities and exploits.
Here is the process to disable VBS/HVCI in Windows 10 and 11:
- Search for "Core Isolation" in Windows search or open it from System Settings.
- Turn off Memory Integrity (if it was on).
- Restart the system.
- Open the System Information app.
- Scroll down to the "Virtualization-based security" row.
- If it says "not enabled," VBS is disabled.
If VBS is still enabled, it must be disabled from the system registry (admin access plus experience may be required) by following these steps:
- Open and run regedit to open the registry editor.
- Navigate to the folder Computer\HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\DeviceGuard.
- Open the file named EnableVirtualizationBasedSecurity and set its value to 0.
- Close regedit.
- Restart the PC.
- Confirm in the System Information app that VBS is disabled.
Learn more about Windows virtualization-based security features and see what to keep in mind when securing virtual environments. Explore how to enable Windows Defender Device Guard and compare endpoint detection and response tools for Windows Server.








