What is WPA3 (Wi-Fi Protected Access 3)?
WPA3 (Wi-Fi Protected Access 3) is the third iteration of a security certification standard developed by the Wi-Fi Alliance. WPA3 is the latest updated implementation of WPA2, which has been in use since 2004. The Wi-Fi Alliance began certifying WPA3-approved products in 2018.
WPA3 is designed to improve security for wireless networks. It's a major improvement over WPA2, as it provides increased protection of data that moves across personal and enterprise Wi-Fi networks.
Updates to WPA3 include better protection for simple passwords, encryption for open networks, and more secure encryption for enterprise-based networks.
The WPA3 protocol provides new features for personal and enterprise use, such as a harder-to-break 256-bit Galois/Counter Mode Protocol (GCMP-256), 384-bit Hashed-based Message Authentication Code (HMAC) and 256-bit Broadcast/Multicast Integrity Protocol Galois Message Authentication Code (BIP-GMAC-256). The WPA3 protocol also supports security measures such as perfect forward secrecy (PFS), which produces a temporary private key exchange between clients and servers. A unique session key is generated for every individual session a user initiates.
Wi-Fi Easy Connect is another new feature in WPA3 that enables devices to connect quickly, even those without a screen or input method. This is especially useful for internet of things (IoT) devices.
However, WPA3 support isn't automatically added to every device. Users who wish to use WPA3-approved devices must either buy a router that supports WPA3 or hope their device supports the new protocol.
Why is WPA3 important?
WPA3 is a mandatory certification for Wi-Fi-certified devices and remains a standard for wireless security. WPA3 is an overall improvement over its previous iteration, WPA2.
WPA3 is designed to improve Wi-Fi security by enabling better authentication over WPA2, providing expanded cryptographic strength and increasing the resiliency of critical networks.
The newer standard also includes different capabilities for personal and enterprise use, as Wi-Fi networks differ in usage, purpose and security in these settings. For example, WPA3-Personal networks offer increased protection against attempts at password guessing, while WPA3-Enterprise networks provide improved security protocols for networks.
Key features of WPA3 include the following:
- Protected Management Frames (PMF) protects unicast and broadcast management frames and encrypts unicast management frames. This means wireless intrusion detection and wireless intrusion prevention systems now have fewer brute-force ways to enforce client policies.
- Simultaneous Authentication of Equals (SAE) enables the client and access point (AP) to exchange cryptographic keys before the authentication step. This protects the shared key and helps to mitigate brute-force attacks.
- Transition mode is a mixed mode that enables the use of WPA2 to connect clients that don't support WPA3.
WPA3 weaknesses
While WPA3 is a significant improvement over WPA2, it isn't invulnerable. There are no currently active known exploits, but there have been several in the past, which have been patched by most vendors.
The Dragonblood attack could be used to recover the password used to connect to the network. If the network uses enterprise Extensible Authentication Protocol (EAP), this might include corporate username and password. This attack abuses the Dragonfly handshake used in SAE and combines a downgrade attack with side-channel timing attacks.
The more recent FragAttacks vulnerability affected all Wi-Fi security protocols from Wired Equivalent Privacy (WEP) to WPA3. In it, an attacker connected to the network sends carefully crafted packets with injected data that is executed by the victim endpoint.
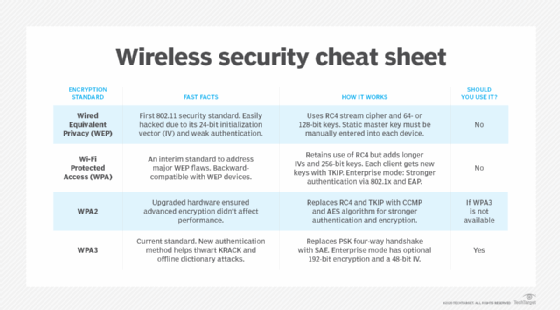
Forms of WPA3 security
WPA3 has three main personal and enterprise modes:
- WPA3-Personal (WPA3-SAE). This mode focuses on improving protection for individual users by providing better security using SAE. SAE increases security over WPA2, even when using a simple password. Personal mode lets users choose easy-to-remember passwords, while still providing increased security using PFS to protect data traffic.
- WPA3-Enterprise. Enterprise mode builds on top of the previous WPA2-Enterprise mode. However, enterprise mode requires the use of PMF on all WPA3 connections. Enterprise mode also has multiple EAP methods for authentication, 128-bit authenticated encryption, and 256-bit key derivation and confirmation, as well as 128-bit PMF.
- Wi-Fi Enhanced Open. This extra mode focuses on increasing privacy in open networks. Enhanced Open mode prevents passive eavesdropping by encrypting traffic even when a password isn't used. This mode uses 256-bit authenticated encryption and 384-bit key derivation and confirmation, as well as 256-bit PMF.
WPA3 vs. WPA2
While WPA2 made improvements over the previous WEP and WPA, WPA3 is even more secure and comprehensive. When compared to the WPA2 standard, WPA3 adds the following notable features:
- SAE protocol. This is used to create a secure handshake, where a network device connects to a wireless AP and both devices communicate to verify authentication and connection. Even if the password is weak, WPA3 provides a more secure handshake than WPA2.
- Session encryption. In WPA2, all devices share the same encryption based on the password, and open networks are not encrypted at all. For example, an attacker at a coffee shop could easily read all the Wi-Fi traffic for all connected devices. In WPA3, each session uses a separate encryption key preventing this.
- Device Provisioning Protocol (DPP). Also known as Easy Connect, DPP enables devices to be quickly connected to a protected network. This lets users allow devices on the network by using near-field communication tags or QR codes. This is especially useful for connecting devices without a screen or with simple interfaces, such as IoT devices. DPP replaces the less secure Wi-Fi Protected Setup connection mechanism.
- Stronger brute-force attack protection. WPA3 protects against offline password guesses by giving users only one guess attempt, making them interact with a Wi-Fi device directly. This means the user must be physically present every time they want to guess the password. WPA2 lacks built-in encryption and privacy in public open networks, making brute-force attacks a major threat.
- PFS. In WPA2, the same encryption is used for all traffic that is protected by the same connection password. PFS means that an attacker can passively record encrypted traffic, and once they obtain the encrypting password, all traffic past and future can be decrypted. WPA3 implements PFS where a unique key is used for every session, so even if one session is compromised, all others are still protected.
- Bigger session keys. WPA3 supports larger session key sizes, up to 192-bit security in enterprise use cases.
- Encryption. WPA2 uses the older Advanced Encryption Standard for encryption, while WPA3 uses the more secure GCMP.
Learn more about the differences among WEP, WPA, WPA2 and WPA3, and see how to improve mobile hotspot security.







