wireless intrusion prevention system (WIPS)
What is a wireless intrusion prevention system (WIPS)?
A wireless intrusion prevention system (WIPS) is a dedicated security device or integrated software application that monitors a wireless local area network (WLAN) or Wi-Fi network's radio spectrum for rogue access points (APs) and other wireless threats. It thus helps to protect the network and ensure its operational continuity and integrity.
What is the purpose of a WIPS?
The main purpose of a WIPS device or software is to monitor a wireless network's airspace to detect unexpected, unauthorized or rogue activities and frequencies. If any malicious or misconfigured device is operating or trying to operate on the network, the WIPS can detect it and automatically shut it down. In doing so, the WIPS can prevent the device from executing malicious attacks against the network and its users.
Advanced WIPS devices can also detect and classify known wireless devices and identify their unique signal patterns to determine whether those devices could compromise the security of the wireless network.
In addition to providing a layer of security for WLANs, WIPS devices and software monitor network usage and performance, and discover APs with configuration errors. In doing so, a WIPS helps to maintain the network's security, uptime, availability and overall health.
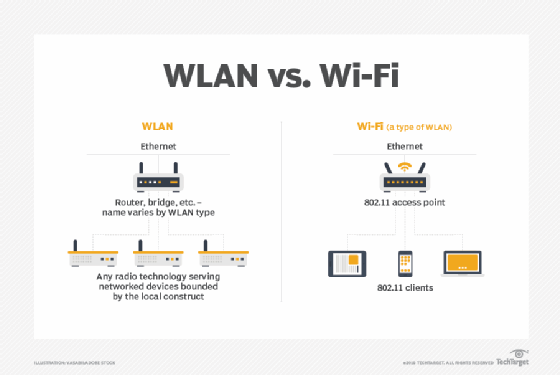
How does a WIPS work?
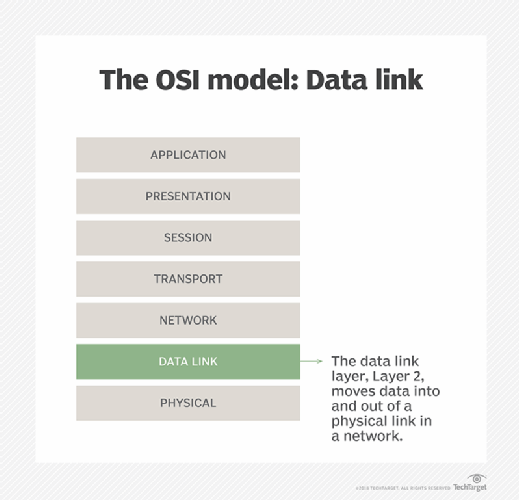
The Open Systems Interconnection model divides network communications functions into seven layers. A WIPS operates at Layer 2 -- the data link layer -- to detect and mitigate the threats to a wireless network at Layers 1 through 3.
A WIPS compares the media access control addresses of all wireless access points on a network against the known signatures of preauthorized, known wireless APs and sounds an alert when a discrepancy is found. To circumvent MAC address spoofing, some higher-end WIPS devices are able to analyze the unique radio frequency signatures that wireless devices generate and block unknown radio fingerprints.
How WIPS devices are deployed
There are three basic ways to deploy a WIPS.
The first, primarily found at the lower end of the market, is known as time slicing or time sharing. In this type of deployment, the wireless access point does double duty, providing network traffic with wireless connectivity while periodically scanning for rogue APs.
In the second approach, which is known as integrated WIPS, a sensor built into the authorized access point continually scans radio frequencies, looking for unauthorized access points. This method ensures always-on wireless intrusion monitoring and prevention, providing continued protection for the entire airspace from a host of threats.
In the third approach, known as WIPS overlay, sensors are deployed throughout a building to monitor radio frequencies. The sensors forward the data they collect to a centralized server for further analysis, action and log archiving.
WIPS overlay hardware resembles a rack server, and the associated sensors resemble Wi-Fi APs. Most WIPS overlay systems share the same fundamental components:
- Sensors, which monitor the radio spectrum and forward logs back to a central management server.
- Management server, which receives information captured by the sensors and takes appropriate defense actions based on this information.
- Database server, which stores and organizes the information captured by the sensors.
- Console, which provides an interface for administrators to set up and manage the WIPS.
While WIPS overlays provide many valuable features and protections, especially to large enterprises that capture customer data, they can be quite costly due to the requirement for dedicated hardware. With hardware, applications, subscriptions and training all factored in, an enterprise with 250 access points might spend as much as $100,000 on a WIPS.
What threats can a WIPS defend against?
Wi-Fi networks are vulnerable to numerous threats that can potentially compromise users' security and sensitive data. These include the following:
Man-in-the-middle attacks
A MitM attack refers to hackers attempting to eavesdrop on communications between two devices on a Wi-Fi network, usually to steal information or inject malware into the network.
Rogue access points
A rogue AP is a fake AP plugged into a legitimate Wi-Fi network. It creates a backdoor that allows the attacker to intercept the communications and data traveling over the network.
Evil twin access points
An evil twin AP is a clone of a legitimate AP and looks like its convincing replica. If a user inadvertently connects to the evil twin, they might not realize that they are not connected to the legitimate network. If they happen to transfer sensitive data over this clone network, such as credit card numbers or passwords, the hacker might be able to steal that data. Cybercriminals also leverage evil twin APs to install malware on user devices.
Password attacks
Cybercriminals commonly try to gain access to a Wi-Fi network through password attacks. In these attacks, the attacker tries to guess or crack the network's password, either with an automated brute-force tool or by using a list of credentials leaked during a data breach. Simple passwords are easy to guess and therefore particularly useful to cybercriminals for compromising Wi-Fi networks.
Packet sniffing
In a packet sniffing attack, hackers attempt to intercept, or "sniff," and analyze the data packets sent over a Wi-Fi network. The goal is to find the packets containing sensitive information that the attacker can then exploit -- say, for use in another attack -- or sell, usually over the dark web.
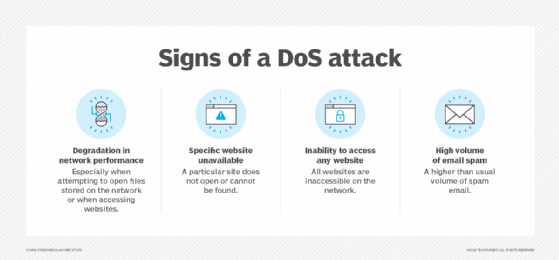
Denial-of-service attacks and wireless jamming
In a DoS attack, hackers flood the Wi-Fi network with fake traffic so that it becomes inaccessible to legitimate users. A wireless jamming attack has a similar goal, albeit by sending a signal on the same frequency as the network. In both cases, the network gets disrupted, affecting its speed and availability.
A robust and properly configured WIPS can protect a wireless network from all these threats and vulnerabilities.
WIPS deployments and regulatory compliance
A WIPS is crucial to maintain the security of a wireless network. The right WIPS can help organizations maintain compliance with internal security policies and external regulations.
Some regulations recommend implementing a WIPS to boost wireless security. The Payment Card Industry Security Standards Council, which develops and drives the PCI Data Security Standard, recommends the use of a WIPS to do the following:
- Monitor network traffic.
- Analyze possible violations, such as DoS attacks or intrusion attempts.
- Stop possible incidents.
- Contain rogue wireless devices.
- Detect unsafe activities and configurations.
Learn about types of wireless network attacks and how to prevent them. Follow these wireless network security best practices to ensure your company's WLAN remains protected against threats and vulnerabilities.
