What is biometric authentication?
Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify their identity. Instead of relying on personal identification numbers (PINs) or passwords, biometric authentication systems compare physical or behavioral traits to stored, confirmed, authentic data in a database. If both samples of the biometric data match, authentication is confirmed. Typically, biometric authentication is used to manage access to physical and digital resources, such as buildings, rooms and computing devices.
Biometric identification uses biometrics, such as fingerprints, facial recognition and retina scans, to identify a person, whereas biometric authentication is the use of biometrics to verify that people are who they claim to be.
Types of biometric authentication methods
The following examples of biometric technology built using computer vision algorithms. These technologies can be used to digitally identify people or permit them to access a system:
- Chemical biometric devices
-
- DNA (deoxyribonucleic acid) matching uses genetic material to identify a person.
- Visual biometric devices
-
- Retina scans identify subjects by analyzing the unique pattern of blood vessels at the back of their eyes.
- Iris recognition uses a picture of the iris to identify people in an iris scan.
- Fingerprint scanners identify people based on their fingerprints.
- Hand geometry recognition verifies identity or authorizes transactions using a mathematical representation of the unique characteristics of people's hands. This is done by measuring the distances between various parts of the hand, including finger length, finger breadth and the shape of the valleys between the knuckles.
- Facial recognition relies on the unique characteristics and patterns of people's faces to confirm their identity. A facial recognition system identifies 80 nodal points on a human face, which make up numeric codes called faceprints.
- Ear authentication verifies identity based on users' unique ear shape.
- Signature recognition uses pattern recognition to identify individuals based on their handwritten signature.
- Vein or vascular recognition uses scanners to detect and map the unique arrangement of veins beneath the skin using infrared light.
- Finger vein recognition identifies individuals based on the vein patterns in their finger.
- Behavioral biometrics
-
- Gait analysis examines the way people walk.
- Typing recognition establishes people's identity based on their unique typing characteristics, including their typing speed.
- Mouse and touchscreen recognition identify how someone moves a pointer or swipes when using desktop and mobile apps.
- Auditory biometric devices
-
- Voice ID identifies individuals with voice recognition and relies on characteristics created by the shape of the mouth and throat.
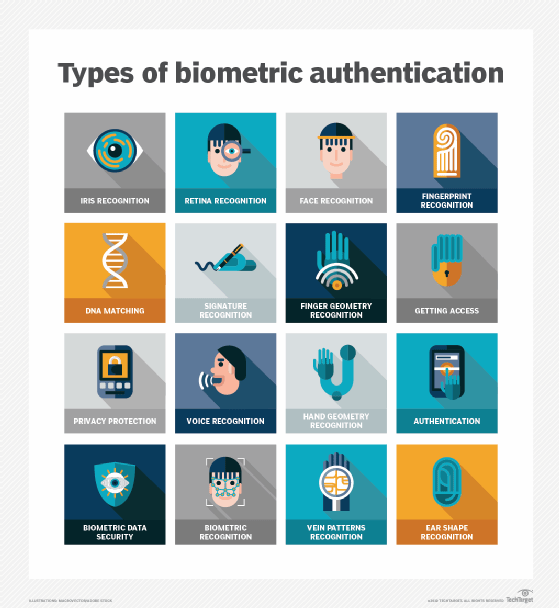
What are the components of biometric authentication devices?
A biometric device includes three components: a reader or scanning device, technology used to convert and compare collected biometric data, and a database for storage.
A sensor is a device that measures and captures biometric data. For example, it could be a fingerprint reader, voice analyzer or retina scanner. These devices collect data to compare to the stored information for a match. The software processes the biometric data and compares it to match points in the stored data.
Most biometric data is stored in a database that's tied to a central server on which all data is housed. However, another method of storing biometric data is cryptographically hashing it to enable the authentication process to be completed without direct access to the data.
What is multimodal biometric authentication?
Many advanced systems use multimodal biometrics, combining two or more biometric methods, such as fingerprint and facial recognition, to enhance security and accuracy, making it significantly harder for unauthorized individuals to gain access. Multimodal biometric authentication adds layers to an authentication process by requiring multiple identifiers, which are read simultaneously during the process.
Multimodal biometrics can be considered a form of multifactor authentication (MFA). However, it differs significantly from the more commonly understood form of MFA, where users typically input sensitive information, such as a password and a one-time code, into a mobile or desktop device.
Multimodal biometric authentication is often used in high-security environments such as data centers, government facilities, banking systems or any place where the cost of identity compromise is high.
Increased security without the need for key cards, access cards, passwords or PINs is among the advantages for organizations that choose to adopt this approach. Additionally, malicious actors who attempt to hack or fake their way through an authentication system have a harder time faking two or more unique characteristics of an individual than if they were to try faking only one.
However, this approach also comes with a few disadvantages. High costs can be incurred when assembling and implementing the tools needed, such as scanners, computing power and storage space for biometric data. Also, use of this technology can intensify public perception that an organization is collecting and storing personal information unnecessarily, which can then be used to surveil people with or without their consent.
Biometric authentication use cases
Examples of areas where biometric authentication is used include the following:
Law enforcement
Law enforcement and state and federal agencies use different kinds of biometric data for identification purposes. These include fingerprints, facial features, iris patterns, voice samples and DNA.
For example, the Automated Fingerprint Identification System (AFIS) is a database that is used to identify fingerprints. It was first used in the early 1970s as a way for police departments to automate their otherwise manual fingerprint identification process, making it quicker and more effective. In the past, a trained human examiner had to compare a fingerprint image to the prints on file. If there was a match, the examiner would double-check the two prints to verify the match.
Today, AFIS can match a fingerprint against a database of millions of prints in a matter of minutes.
Travel
An electronic passport or e-passport is the same size as a conventional passport and contains a microchip that stores the same biometric information as a conventional passport, including a digital photograph of the holder. A chip stores a digital image of the passport holder's photo, which is linked to the owner's name and other personally identifiable information.
The e-passport is issued electronically by a country's issuing authority, which checks the identity of the applicant. They use fingerprints or other biometric information to confirm that the data in the chip matches the information provided by the applicant before issuing the passport.
Healthcare
Hospitals use biometrics to more accurately track patients and prevent mix-ups. Clinics and doctors' offices use it to keep patients' information secure. Using biometric data, hospitals can create digital identities of patients that help them store and access those patients' medical histories. This information can be used to ensure the right patient gets the right care, whether that means faster identification in emergencies or preventing medical errors.
Identity and access management systems
An identity and access management (IAM) system is a combination of policies and technology tools that collectively form a centralized means of controlling user access to important information a business has stored.
IAM systems use methods such as single sign-on, two-factor authentication and MFA. They also use sophisticated tools, including biometrics, analysis of behavioral characteristics, AI and machine learning, as part of their overall strategy to make authentication more rigorous and secure.
Payments
The use of biometric authentication in payments and credit card processing is nascent and slowly expanding. The idea is to add more security to payments without added complexities or frustrations. Examples of biometric payments have consumers using cards to pay for goods, but those transactions are only authorized after they scan their fingerprint, eye or face.
There's more than one way to scan as well, since cards can have built-in sensors to scan fingerprints, while a register or kiosk might have scanners readily available.
Education
Biometric authentication plays a growing role in the education sector, offering enhanced security and streamlined operations. For example, it's used for student identification, ensuring accurate attendance tracking and providing secure access to school facilities.
Biometric authentication also helps prevent impersonation during exams by verifying that the test-taker is the enrolled student. It can also enable secure library access and contactless checkout of resources for students.
Smart homes and vehicles
Biometric authentication is becoming increasingly integrated into everyday living through smart home systems and connected vehicles. In modern homes, facial or voice recognition can be used to unlock doors, disarm security systems, adjust lighting and climate settings, and interact with digital assistants. This adds convenience and an extra layer of security by ensuring that only authorized users can control key functions.
In the automotive industry, several manufacturers are incorporating biometrics into vehicles. For example, a fingerprint or facial recognition is used to start the car, unlock doors and personalize driver settings, such as seat position, mirror angles and infotainment preferences.
Physical access control
Biometric authentication significantly enhances physical access control, securing premises and ensuring only authorized individuals can enter restricted areas. This is achieved through various methods, such as fingerprints, facial recognition, or iris scans to grant entry to buildings, sensitive server rooms, or specific zones within a larger facility.
Additionally, it streamlines time and attendance tracking by enabling employees to clock in and out with their unique biometrics, helping prevent time theft and ensuring accurate payroll records.
What are the advantages and disadvantages of biometric authentication?
Biometric authentication offers both advantages and disadvantages.
Advantages of biometric authentication
In the United States alone, business use of biometric authentication has drastically increased in recent years as more business leaders are becoming confident in its capabilities. Here are the key advantages of biometric authentication:
- Enhanced security. Since biometric authentication uses unique characteristics for verification, these features are difficult to replicate. Traditional methods, such as usernames, passwords and ID cards, aren't as secure because they can be stolen or guessed easily.
- Convenience and speed. Biometric authentication eliminates the need to remember complex passwords or carry physical tokens, streamlining the login process. It also makes unlocking devices and accessing accounts significantly faster and more convenient.
- Nontransferable. Unlike passwords that can be shared or stolen, biometric traits are physically linked to the individual, making unauthorized sharing impossible.
- Reduced human error. Biometric authentication minimizes the potential for human errors associated with traditional methods, such as forgetting passwords, typing mistakes or accidentally sharing credentials.
- Scalability. Biometric systems can be easily scaled to accommodate many users, making them suitable for large organizations and public services.
- Long-term stability. Physiological biometrics generally remain stable throughout a person's lifetime. This reduces the need for frequent updates or changes to authentication methods.
- Reduced costs. Biometric authentication helps reduce costs related to password resets, customer support and fraud prevention. By enabling real-time, automated identity verification, it also speeds up processes such as customer onboarding and access control, improving overall operational efficiency.
Disadvantages of biometric authentication
While biometrics offers many advantages for particular industries, there are controversies surrounding its usage. Here are the key issues related to biometric authentication:
- Data interception. If bad actors capture biometric data when it's being transmitted to a central database, they can fraudulently replicate that data to perform another transaction. For example, by capturing an individual's fingerprint and using it to access a fingerprint-secured device, hackers or other bad actors could access sensitive data, such as private messages or financial information.
- Risk of privacy invasion. Another potential issue with biometric authentication is that once a security system has been implemented, an organization might be tempted to use the system for functions beyond its original intention, which is known as function creep. For example, a company might find the technology useful for employee monitoring and management.
- Irreplaceability of compromised data. Once a biometric trait, such as a fingerprint template, is compromised or stolen, it's nearly impossible to change or revoke, potentially leaving the individual exposed.
- Accuracy challenges. Despite their overall accuracy, biometric systems aren't infallible and can experience errors, such as False Acceptance Rate (FAR) and False Rejection Rate (FRR). FAR occurs when unauthorized individuals are mistakenly granted access, posing a security risk. FRR happens when legitimate users are wrongly denied access, causing frustration. These issues can result from factors such as sensor quality, environmental conditions, changes in appearance and biases in the training data, affecting both security and user experience.
- High initial costs. Setting up biometric authentication systems can involve significant initial investments in specialized hardware, software and infrastructure upgrades. This can make it costly for smaller organizations.
- Sensing limitations. External factors, such as dirt, moisture, lighting conditions or even minor injuries to the biometric trait, can affect the performance of biometric sensors.
- Limited device compatibility. Biometric devices might not work with other systems and applications, limiting its use.
- Single point of failure. If a single biometric modality is compromised or malfunctions, the entire authentication process can be affected. However, multimodal systems aim to mitigate this risk.
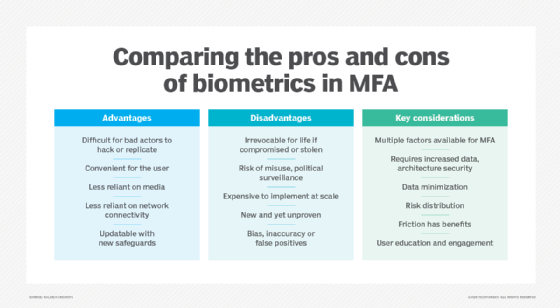
Biometric authentication vs. passwords
Biometric authentication and passwords are both methods of proving identity, but they work in different ways, each with its strengths and trade-offs. The following is a comparison of various aspects of both methods:
Identification
Biometric authentication uses unique physical or behavioral traits, such as fingerprints, face or voice, to verify a person's identity. On the other hand, passwords are secret words or phrases that users input to confirm their identity.
Security
Biometric authentication typically offers stronger protection than traditional passwords because the traits used for identification are inherently difficult to replicate, guess or phish. It also resists brute-force attacks that commonly target passwords. However, biometric systems aren't foolproof and can be spoofed using techniques such as fake fingerprints, high-resolution photo masks, or 3D-printed replicas.
Whereas the security of passwords largely depends on their complexity and uniqueness. Weak or reused passwords are especially vulnerable to security breaches and are linked to poor password practices. Passwords are also easily compromised through phishing, brute-force attacks or even physical methods such as thermal or smudge analysis.
Flexibility
Once compromised, biometric data can't be reset, posing a significant challenge. Additionally, environmental factors or physical changes can affect the accuracy of biometric systems. However, passwords can be changed immediately if compromised, unlike biometric data. The flexibility of passwords enables users to quickly mitigate security risks.
Usability
Biometric authentication is quick and effortless, requiring only a simple presentation of a finger or face, with no need to type anything. This streamlined process enhances user convenience and helps eliminate password fatigue that comes from managing numerous credentials across different platforms.
Passwords remain a familiar and universally accepted method of authentication, requiring no specialized hardware to set up. However, they can be frustrating for users to manage, as they're often difficult to remember and frequently forgotten, especially when strong, unique passwords are used for multiple accounts.
Implementation costs
Biometric authentication requires specialized hardware and software, leading to higher initial setup costs. Ongoing maintenance and system updates also add to the expenses. Additionally, organizations must ensure compliance with data protection regulations when handling biometric data.
Passwords don't require specialized hardware for implementation, making them cost-effective and easy to deploy. However, managing passwords across multiple platforms can be cumbersome and prone to human error.
To address the limitations of both methods, many modern security systems integrate biometric authentication with passwords, such as using a fingerprint to unlock a password manager. This hybrid approach uses the strengths of both methods, offering a more secure and user-friendly authentication experience.
Can you hack or bypass biometric authentication?
While biometric authentication systems are generally more secure than traditional passwords, they aren't immune to sophisticated attacks. However, no technology is entirely hacker-proof. The following is a breakdown of how biometric authentication can be hacked or bypassed:
- Fingerprint spoofing. In this method, attackers create fake fingerprints using materials such as gelatin, silicone or 3D printing. These replicas can deceive fingerprint scanners, especially if the system lacks advanced liveness detection, a security feature that verifies whether the biometric input comes from a real, live person rather than a spoof.
- Facial recognition manipulation. Facial recognition systems can be deceived using several sophisticated methods. Attackers might use high-resolution photos or videos of the target to bypass some systems. Additionally, life-like 3D masks that closely mimic a person's facial features can fool the system into granting access. More advanced techniques involve deepfakes, which are AI-generated videos that convincingly replicate a person's facial movements and expressions, making it increasingly challenging for facial recognition technology to distinguish between real and fake identities.
- Voice imitation. Advanced AI tools can synthesize a person's voice, enabling attackers to pass voice authentication systems.
- Iris spoofing. This is more challenging but has been demonstrated using high-resolution printed images of an iris with a contact lens placed over it to simulate depth and texture, or by reconstructing an iris from compromised binary data.
- Skimming. Similar to credit card skimming, devices can be used to surreptitiously capture biometric data, such as fingerprints, from scanners or surfaces the user interacts with.
- Social engineering. Attackers might use phishing or other social engineering tactics to trick users into providing their biometric data directly or performing actions that enable its capture.
- System vulnerabilities. Weaknesses in the biometric system's software, algorithms or hardware implementation can create entry points for attackers. This includes bugs, misconfigurations or insufficient liveness detection capabilities.
Future of biometric authentication
The future of biometric authentication is expected to be characterized by increasing sophistication, deeper integration into daily life, and a continuous push towards enhanced security and user convenience. Several key trends and advancements that are shaping this evolution include the following:
AI and machine learning integration
AI and machine learning are playing an increasingly central role in advancing biometric authentication systems. These technologies enhance accuracy, adapt to changing user traits and help defend against sophisticated spoofing attempts, such as deepfakes. They do this by analyzing micro-expressions, voice intonation and behavioral patterns. For example, modern facial recognition systems now use deep learning to detect subtle facial movements and 3D depth, making them more resilient to photo or mask-based spoofing.
According to a Gartner press release, by 2026, 30% of enterprises will consider identity verification and authentication tools unreliable when used in isolation, due to the growing threat of AI-generated deepfakes. This highlights the growing need for layered security approaches and technologies such as liveness detection.
Voice authentication with AI is also becoming stronger. For example, AI models can analyze pitch, cadence and even unnatural pauses in speech to detect deepfake audio with increasing precision.
Multimodal and contactless biometric authentication
The future of biometric authentication is rapidly advancing toward multimodal systems that integrate two or more distinct biometric modalities, such as facial recognition, fingerprint scanning and voice authentication. This layered approach enhances security, making it much more difficult for attackers to spoof multiple traits at once. It also improves reliability and accessibility by offering users multiple options for identity verification.
There is also a strong shift toward contactless biometrics, driven by growing demands for convenience and heightened hygiene concerns, especially in the wake of recent global health events. Innovations in this area include advanced facial recognition, precise iris scanning and hover-based technologies for palm or fingerprint authentication, all designed to eliminate the need for physical contact during the verification process.
Behavioral biometrics for continuous authentication
Beyond physical traits, behavioral biometrics, such as typing rhythm, mouse movements, gait and voice patterns, are seeing increased adoption. These systems work passively and continuously, verifying a user's identity in the background as they interact with a device or system. This enables real-time identity assurance by detecting anomalies that might signal session hijacking or insider threats, enabling adaptive security responses based on deviations from the user's typical behavior.
Edge computing and decentralized identity
Biometric data is increasingly being processed locally on edge devices, such as smartphones and smartcards, reducing the need to transmit sensitive data to the cloud. This enhances both speed and privacy, especially in areas with limited connectivity.
At the same time, technologies such as blockchain are being explored as a way to store immutable, verifiable biometric credentials. This could give individuals greater control over their data, enabling them to share it securely without relying on centralized third-party systems.
Explore the most common digital authentication methods and discover how they play a vital role in enhancing cybersecurity for both organizations and users.





