What is the future of cybersecurity?
As cyberthreats grow more sophisticated, enterprises face mounting challenges. What does the future of cybersecurity hold, and how can organizations stay ahead?
Cybersecurity concerns continue to dominate corporate agendas, as a multitude of challenges, including generative AI-enabled attacks, ransomware extortion, supply chain risks, chronic talent shortages and security staff burnout, compound the difficulty of protecting enterprises from malicious threats.
Below are five cybersecurity trends enterprises must understand and address as they move forward.
Trend 1: AI is a double-edged sword in cybersecurity
AI technologies are already having both positive and negative effects on cybersecurity:
- Negative effects. Cybercriminals have been using artificial intelligence and machine learning technologies for years to help them craft increasingly sophisticated, highly customized phishing attacks, deepfake video and audio, and ransomware attacks. AI-generated attacks are much more difficult for security technologies to detect than previous attacks were. These attacks are also more likely to succeed because the use of AI can make them seem legitimate and believable.
- Positive effects. Although cybercriminals have a head start on defenders, organizations are starting to catch up by expanding their use of AI technologies in support of cybersecurity. Many of today's security measures employ AI to improve their capabilities, such as strengthening authentication mechanisms and access controls, detecting and analyzing cyberthreats and anomalies more quickly and accurately, and automating responses to security incidents so incidents are stopped faster, reducing damage and lessening recovery time.
Organizations should act swiftly to ensure that their technology workforces are brought fully up to speed on the capabilities of AI technologies and how they can be leveraged for positive and negative purposes. Most importantly, employees need to be trained on two things: how to identify potentially malicious uses of AI technologies against the organization, and how to effectively and safely use AI technologies in support of the organization's cybersecurity objectives, including an emphasis on the importance of human oversight and validation of AI outputs. The workforce's understanding of AI should be maintained through frequent training updates as AI technologies rapidly evolve.
Trend 2: Addressing the cybersecurity skills gap
Some pundits are declaring that the cybersecurity workforce is in decline, anticipating rapid replacement of skilled workers by AI technologies and other forms of security automation. It remains to be seen how much of this is hype and how much the security workforce will actually decline in the future, if at all. Today, it's obvious that most cybersecurity skills and tasks can't yet be performed competently by technologies instead of people.
However, it's also obvious that there's currently a significant cybersecurity skills gap. A few decades ago, the discipline of cybersecurity was small enough that a single person could understand just about all of it: hardening OSes, configuring firewalls to reduce network attack surfaces, deploying a VPN for secure access for remote employees and using badge readers to restrict access to the data center. Today, the field of cybersecurity has become incredibly vast, with countless specialties, technologies and standards. Even the greatest cybersecurity experts can't credibly claim to be well versed in all of its niches.
Organizations should develop a plan for addressing their cybersecurity skills gap. For many organizations, employing a combination of strategies will provide the best results. Here are some examples:
- Use AI and other security automation technologies to reduce the workload on people in those cases where the technologies perform as well or better than people would.
- Outsource some cybersecurity functions to third parties. This might be particularly beneficial for skills that an organization needs only occasionally, like forensic analysis.
- Offer a variety of skills-building opportunities to the cybersecurity workforce, such as standard training courses and short refresher courses, team exercises, and job shadowing and rotation.
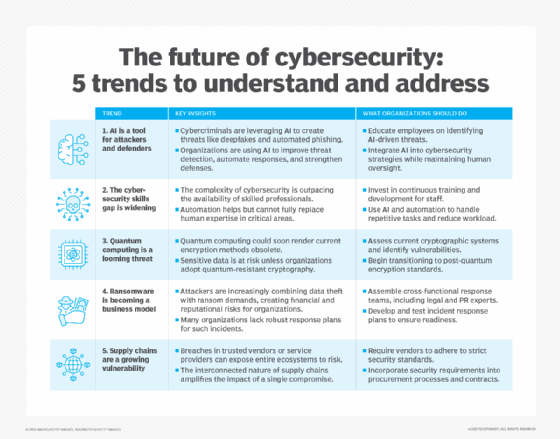
Trend 3: Quantum computing and post-quantum cryptography
Researchers around the world continue to push the boundaries of quantum computing technologies. We don’t know when these technologies will become powerful enough to thwart today's encryption technologies, but experts expect us to pass that threshold in the coming years. At that time, all organizations with quantum computers will be able to access all of the data currently protected by cryptographic algorithms, effectively creating the world's largest data breach.
Organizations should start preparing now for what's called post-quantum cryptography (PQC), which means using cryptographic algorithms that won't be vulnerable to quantum computing. Several post-quantum algorithms have been finalized and standardized recently, and various technologies are adding support for them.
Organizations should inventory their current cryptographic usage, plan how to migrate all of those technologies to their post-quantum counterparts, and then start executing on that plan. Waiting is dangerous because, once quantum computing becomes sufficiently advanced, data that was encrypted months and years ago using today's algorithms will all be accessible. It will be far too late to protect it.
For more information on the latest developments in post-quantum cryptography, see the PQC website hosted by NIST.
Trend 4: Improving response capabilities
It's become painfully obvious that most organizations need to improve their response capabilities. Attacking organizations through ransomware has become an actual business, with attackers effectively locking users out of their systems and data, then demanding -- and receiving -- large ransoms to restore access. At the same time, these attackers are conducting large data breaches, collecting enormous amounts of sensitive data and demanding ransoms to prevent its release or sale.
Organizations need to be prepared to respond to large-scale ransomware incidents, and that means incident responders working closely with not just security experts but also system administrators, legal counsel, public affairs and others to ensure the response goes smoothly and services are restored quickly. Prepare to handle ransom demands before they're made.
Trend 5: Recognizing the risks from supply chains
We typically trust what our vendors and service providers give us. The SolarWinds incident illustrated just how risky that trust in our supply chains is. A single company can be successfully infiltrated by a nation-state, and that company might then provide compromised technology products or services to thousands of other companies. Those companies, in turn, might not only be compromised themselves; they could also expose their own customers' data to the original attackers or provide compromised services to their customers. Thus, what started with a single infiltrated company could expand to millions of organizations and individuals being compromised.
There's no easy answer to addressing this. Organizations could improve many aspects of their security strategy and technology, but what's most important at this time is for organizations to recognize and acknowledge the risks from supply chains and to demand increased vigilance from everyone. Whether that means holding vendors accountable for poor security practices that lead to compromises, requiring more transparency into vendors' security practices before renewing contracts or adding requirements to new procurements, individual organizations can raise awareness of these issues and put pressure on vendors and service providers to do better.
Editor's note: This article was updated by the author in June 2025 to reflect the latest trends in cybersecurity.
Karen Scarfone is a general cybersecurity expert who helps organizations communicate their technical information through written content. She co-authored the Cybersecurity Framework (CSF) 2.0 and was formerly a senior computer scientist for NIST.






