What is the Risk Management Framework (RMF)?
The Risk Management Framework (RMF) is a template and guideline organizations use to identify, eliminate and minimize risks. It was originally developed by the National Institute of Standards and Technology (NIST) to help protect the U.S. government's information systems.
The RMF was initially designed for use by federal agencies but can be easily adopted by any type of organization operating in the private sector. Businesses cannot exist without exposing themselves to risks, such as IT problems, litigation and capital loss. While it is impossible to eliminate all risks involved in running a business, they can be minimized.
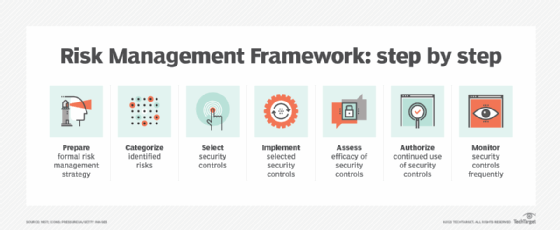
The Risk Management Framework consists of seven core steps: prepare, categorize, select, implement, assess, authorize and monitor. These steps are designed to be standardized and adapted as a continuous approach to identifying, assessing and managing risk in organizations.
What are the 7 steps of the Risk Management Framework?
According to NIST, the following seven steps make up the RMF.
1. Prepare
This stage focuses on preparing the organization to adopt a formal risk management strategy. This might include identifying organizational risks and determining key risk management roles. For example, an IT team looking to improve its security posture by implementing the RMF might gather a team of stakeholders to review current security policies. It also might create a risk register to document different risks, their potential impact, risk owners and other information.
2. Categorize
Organizations begin assessing the identified risks. This can mean assessing the impact of the various risks and prioritizing those that must be addressed. Current security policies would be analyzed to identify any potential security gaps or vulnerabilities and the risks they pose.
3. Select
This stage involves choosing the controls that will be used to protect affected systems and minimize or mitigate the identified risks. These controls will vary widely from one system to the next. They might include anything from implementing risk management tools to shaping policies that will help alleviate concerns. As an example, the IT team might choose to follow the NIST Cybersecurity Framework.
4. Implement
Once the organization has selected the controls it will adopt as part of its risk mitigation strategy, they are documented and implemented to head off potential risks. Using the above example, the IT team begins implementing tools that adhere to the NIST Cybersecurity Framework's core.
5. Assess
This stage seeks to determine whether the selected controls were implemented correctly and if those controls are delivering the desired result. This means making sure any mechanisms that have been implemented are reducing risks in a quantifiable way without accidentally introducing new risks in the process. In this stage, the security analyst or other role tests the new systems, ensuring that everything is working as intended and no new risks are being introduced.
6. Authorize
In some instances, this stage is tied to executive approval of the risk mitigation mechanisms that have been put in place. More often, however, it is an overview by senior members of the organization who want to ensure that risk mitigation strategies are working and adhere to any applicable laws and policies within the organization. As an example, senior IT leadership reviews the IT team's changes and decides whether to approve them for proper use.
7. Monitor
This phase is designed to provide ongoing situational awareness. Organizations should continuously evaluate their risk mitigation strategies to ensure they continue to work as intended. As an example, the IT team would set up automation and continuous monitoring tools to automatically alert them to any unusual behavior that could indicate potential risks.
What are the 5 components of the RMF?
The RMF has five components: identification; measurement and assessment; mitigation; reporting and monitoring; and governance.
1. Identification
The first component in implementing the Risk Management Framework is to identify the risks that the organization faces. These might include strategic, legal, operational and privacy risks.
It is important to note that risk identification is not a one-time process. An organization's risks tend to change over time, so risk assessments will need to be performed on a periodic basis.
2. Measurement and assessment
The goal of the measurement and assessment component is to create a risk profile for each identified risk. Organizations can complete the measurement and assessment phase of the process in several different ways.
In some cases, risk measurement might be based on something as simple as how much capital could potentially be lost because of the risk. However, in other cases, measuring the potential impact of a risk might be far more difficult. In the field of information security, for example, an organization might attempt to quantify the cost of a security breach compared with the cost of implementing a security mechanism that can help to mitigate the risk.
3. Mitigation
Risk mitigation involves examining the risks that have been identified and determining which risks can and should be eliminated, as opposed to the risks that are deemed to be acceptable.
Part of this process involves devising mitigation strategies, such as cyber insurance. For example, if an organization identifies cybersecurity risks that need to be addressed, it might choose to integrate security controls into its development lifecycle. Such an organization would likely also put additional baseline security controls in place.
4. Reporting and monitoring
Risk reporting and risk monitoring essentially mean regularly reexamining the risks to ensure that the organization's risk mitigation strategies are having the desired effect.
5. Governance
Risk governance is the process of making sure that the risk mitigation techniques that have been adopted are put into place and that employees adhere to those policies.
Applications of the Risk Management Framework
The Risk Management Framework can be applied to the following areas of a business:
- Cloud. The RMF helps identify risks associated with cloud-based services and infrastructure.
- Compliance. The RMF helps ensure that an organization's systems and processes meet regulatory or other legal requirements -- such as keeping customer data safe and secure.
- Cybersecurity. The RMF helps identify risks and cybersecurity threats associated with managing an organization's IT infrastructure and securing IT systems from risks such as data breaches.
- Financial. The RMF can help identify and mitigate risks regarding financial systems, reporting, transactions, credit and data integrity.
- Operational. The RMF can improve business operations by identifying and managing risks associated with workflows, resource usage and business continuity.
- Strategic. The RMF supports the decision-making process by ensuring business objectives are also aligned with risk assessments and long-term goals.
What are the business benefits of the RMF?
The RMF was initially intended for use by federal organizations, especially regarding federal information systems. Even so, private sector companies and nonprofit organizations have found the concept of the RMF to be useful. It can provide the following benefits:
- Offers widespread applicability. In addition to being applicable to federal, private sector and nonprofit organizations, the RMF can be implemented by companies across industries of all sizes.
- Aids compliance process. The RMF can help organizations adhere to compliance frameworks such as the Health Insurance Portability and Accountability Act. Implementing compliance in a risk management framework will also aid against legal risks.
- Enhances decision-making. The RMF provides organizations with a more in-depth understanding and insight into applicable risks, enabling them to make better strategic decisions.
- Improves security. A proper RMF system can help organizations identify and mitigate potential security risks.
- Reduces overall risk. The RMF can help an organization to reduce its risks, thereby minimizing legal exposure and helping to maximize profitability.
Organizations can also choose between the RMF and other risk management frameworks. Options include the COSO enterprise risk management framework, ISO 31000 and the IT Infrastructure Library Framework.
Introducing anything new to an organization can also come with introducing new potential risks, even AI. Learn more about the risks posed by AI and AI RMFs.







