Terraform
What is HashiCorp Terraform?
HashiCorp Terraform is an infrastructure as code (IaC) software tool that allows DevOps teams to automate infrastructure provisioning using reusable, shareable, human-readable configuration files. The tool can automate infrastructure provisioning in both on-premises and cloud environments.
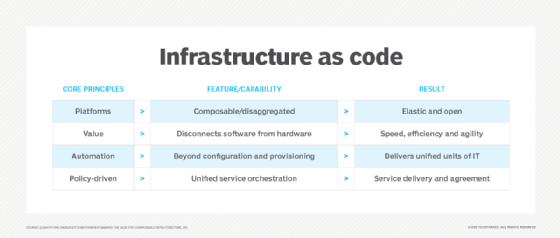
Infrastructure as code and Terraform
Infrastructure as code is the practice of provisioning and managing IT infrastructure through programming. In contrast to manual infrastructure management where each required resource is manually configured by a human, IaC allows DevOps teams to programmatically and automatically manage, monitor and provision the resources they need.
Using Terraform, teams can describe and provision all the components of the infrastructure in the form of code. The code resides in configuration (config) files that can be easily shared, reused and versioned. The files help create a consistent workflow to manage the entire cloud or data center infrastructure and its resources throughout their lifecycle.
Terraform's config files are declarative, that is, they describe the infrastructure's end state. The tool itself handles the underlying logic eliminating the need to write step-by-step instructions -- a cumbersome and time-consuming process -- to create the required infrastructure resources.
The files codify the application programming interfaces (APIs) for cloud platforms and other services, making it easy for DevOps teams to do the following:
- Provision resources from any cloud provider.
- Implement security and compliance guardrails to standardize the infrastructure.
- Utilize standardized and reliable workflows for consistent infrastructure provisioning, collaboration and reuse.
- Integrate the self-service infrastructure with VCS, ITSM and CI/CD.
Terraform can manage infrastructure components, including compute, storage and networking resources, and high-level components like DNS entries. It can also be used to automate the provisioning of firewall policies, databases and servers. A Cloud Development Kit for Terraform (CDKTF) is available to help teams manage infrastructure with their preferred programming language, including TypeScript, Python, Go, C# and Java.
How Terraform works
Terraform uses APIs to automatically create and manage infrastructure resources. All major cloud providers provide accessible APIs that work with Terraform and enable the tool to create declarative configuration files. These providers are listed in the Terraform Registry. The Registry also lists the modules, policy libraries and tasks that teams can use to quickly deploy common infrastructure configurations and automatically manage them via code.
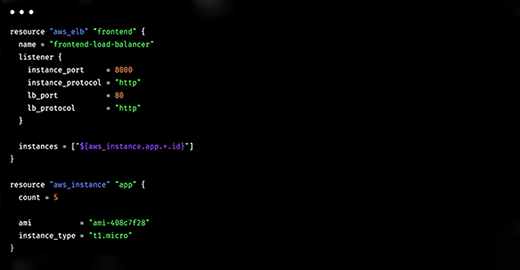
Terraform's workflow occurs in three stages. In stage 1 (write), a user defines the required resources in configuration files. These resources may be across multiple on-premises or cloud environments, and multiple providers and services. Once the user reviews and confirms the required stages, the next stage (plan) begins. Here Terraform creates an execution plan describing the actions it will take to create or update the infrastructure.
The user must approve the plan before Terraform will make changes to the infrastructure. After approval, Terraform performs the proposed operations in the given order (stage 3 – apply). It will always check resource dependencies before making changes. For instance, if a user changes the number of VMs in a VPC (virtual private cloud), Terraform will first recreate the VPC and then scale up the VMs.
Benefits of Terraform
Terraform makes it easy to automate infrastructure provisioning on any cloud or data center. It also tracks all changes in a state file. The file can be committed to a version control system (VCS) and acts as a source of truth for the infrastructure. It thus provides more transparency and prevents unauthorized changes.
Also, Terraform handles the underlying logic when resources are created, removing the need for human input or effort. It also determines resource dependencies with a resource graph and can create or modify nondependent resources in parallel. All of this ensures that resources are provisioned properly, efficiently and in the correct order.
Teams can collaborate and manage Terraform workflows using Terraform Cloud. They can run Terraform in a consistent environment and securely access shared state and secret data. Additionally, they can implement role-based access controls (RBACs) to standardize and secure the infrastructure, and use a private registry to share modules and providers.

Common use cases for Terraform
The most common use case for Terraform is IaC. The infrastructure deployments created with Terraform can be easily integrated with existing CI/CD workflows. The tool is also useful in other ways. For example, teams can use Terraform to automatically update load balancing member pools and other key networking tasks.
Terraform is also useful for multi-cloud provisioning. With Terraform, development teams can deploy serverless functions in AWS, manage Active Directory (AD) resources in Microsoft Azure, and provision load balancers in Google Cloud. They can also use Terraform (with HCP Packer) to create and manage multi-cloud golden image pipelines and deploy and manage multiple virtual machine (VM) images.
Some other use cases for Terraform include the following:
- Manage Kubernetes clusters on any public cloud (AWS, Azure, Google).
- Enforce policy-as-code before infrastructure components are created and provisioned.
- Automate the use of secrets and credentials in Terraform configurations.
- Codify existing infrastructure by importing it into an empty Terraform workspace.
- Migrate state to Terraform to secure it and easily share it with authorized collaborators.
Terraform editions
Terraform is available in three versions: Open Source, Cloud and Enterprise:
Terraform Open Source
Terraform Open Source is a free tool to adopt IaC and provision infrastructure on any cloud provider. The tool automatically manages configuration, plugins and state, and adds all config files into a VCS to safely manage and track changes. It also includes templates called modules to speed up infrastructure deployment and group it into logically related components.
Terraform Cloud
Terraform Cloud is a SaaS tool that runs in a stable, remote environment and securely stores state and secrets. It provides a rich user interface, RBACs, a private registry and an API to integrate it into existing workflows. Teams can publish their configuration modules (that define approved infrastructure patterns) in the private registry. They can also enforce security rules with the Sentinel embedded policy-as-code framework. The tool connects to common VCS like GitHub, GitLab and Bitbucket. It can be integrated with the Terraform CLI.
Terraform Enterprise
Terraform Enterprise is suitable for teams looking to set up a self-hosted distribution of Terraform Cloud and for organizations with strict security and compliance requirements. This version supports air gapped and active-active architectures and allows private networking. HashiCorp provides dedicated support to set up a private instance of Terraform using Terraform Enterprise.
Explore the differences between Ansible versus Terraform versus Vagrant infrastructure as code automation platforms. Learn how to manage multiple environments with Terraform workspaces. Check out this Terraform Registry tutorial to build and share modules.







