network protocol
What is a network protocol?
A network protocol is a set of established rules that specify how to format, send and receive data so that computer network endpoints, including computers, servers, routers and virtual machines, can communicate despite differences in their underlying infrastructures, designs or standards.
To successfully send and receive information, devices on both sides of a communication exchange must accept and follow protocol conventions. In networking, support for protocols can be built into the software, hardware or both.
Without network protocols, computers and other devices would not know how to engage with each other. As a result, except for specialty networks built around a specific architecture, few networks would be able to function, and the internet as we know it wouldn't exist. Virtually all network end users rely on network protocols for connectivity.
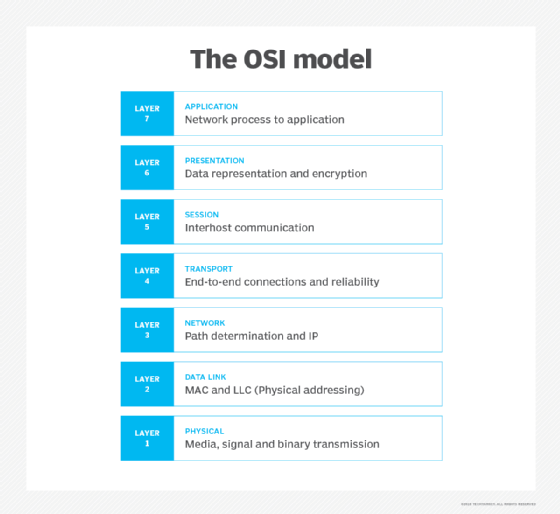
How network protocols work: The OSI model
Network protocols break larger processes into discrete, narrowly defined functions and tasks across every level of the network. In the standard model, known as the Open Systems Interconnection (OSI) model, one or more network protocols govern activities at each layer in the telecommunication exchange. Lower layers deal with data transport, while the upper layers in the OSI model deal with software and applications.
To understand how network protocols function, it's crucial to understand the workings of the seven layers of the OSI model:
- Physical layer. The physical layer is the initial layer that physically connects two interoperable systems. It controls simplex or duplex modem transmissions and transfers data in bits. Additionally, it oversees the hardware that connects the network interface card (NIC) to the network, including the wiring, cable terminators, topography and voltage levels.
- Data-link layer. The data-link layer is responsible for the error-free delivery of data from one node to another over the physical layer. It's also the firmware layer of the NIC. It puts datagrams together into frames and gives each frame the start and stop flags. Additionally, it fixes issues brought on by broken, misplaced or duplicate frames.
- Network layer. The network layer is concerned with information flow regulation, switching and routing between workstations. Additionally, it divides up datagrams from the transport layer into error-free and smaller datagrams.
- Transport layer. The transport layer transfers services from the network layer to the application layer and breaks down data into data frames for error checking at the network segment level. This also ensures that a fast host on a network doesn't overtake a slower one. Essentially, the transport layer ensures that the entire message is delivered from beginning to end. It also confirms a successful data transmission and retransmitting of the data if an error is discovered.
- Session layer. The session layer establishes a connection between two workstations that need to communicate. In addition to ensuring security, this layer oversees connection establishment, session maintenance and authentication.
- Presentation layer. The presentation layer is also known as the translation layer because it retrieves the data from the application layer and formats it for transmission over the network. It addresses the proper representation of data, including the syntax and semantics of information. The presentation layer is also in charge of managing file-level security and transforming data to network standards.
- Application layer. The application layer, which is the top layer of the network, oversees relaying user application requests to lower levels. File transfer, email, remote login, data entry and other common applications take place at this layer.
Every packet transmitted and received over a network contains binary data. Most computing protocols add a header at the beginning of each network packet to store information about the sender and the message's intended destination. Some protocols may also include a footer at the end with additional information. Network protocols process these headers and footers as part of the data moving among devices in order to identify messages of their own kind.
Network protocols are often outlined in an industry standard -- developed, defined and published by groups such as the following:
The TCP/IP model
A set of cooperating network protocols is called a protocol suite. The Transmission Control Protocol/Internet Protocol (TCP/IP) suite, which is typically used in client-server models, includes numerous protocols across layers, such as the data, network, transport and application layers, working together to enable internet connectivity.
These include the following:
- TCP uses a set of rules to exchange messages with other internet points at the information packet level.
- User Datagram Protocol, or UDP, acts as an alternative communication protocol to TCP and is used to establish low-latency and loss-tolerating connections between applications and the internet.
- IP uses a set of rules to send and receive messages at the level of IP addresses.
Additional network protocols, including Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP), have defined sets of rules to exchange and display information. Unlike the OSI model, the TCP/IP suite consists of four layers, each with its protocols. The four layers of the TCP/IP model are the following:
- Application layer. This is the topmost layer of the TCP/IP model and is responsible for providing users with access to network resources. Some of the protocols included in this layer are HTTP, Simple Mail Transfer Protocol (SMTP) and FTP.
- Transport layer. This layer ensures that segments are transmitted correctly via the communication channel. The network link between the source and destination systems is also established at this layer.
- Internet layer. Also known as the network layer, the internet layer receives and sends packets for the network. This layer comprises IP, Address Resolution Protocol (ARP) and Internet Control Message Protocol (ICMP).
- Network access layer. The network access layer of TCP/IP combines the physical and data-link layers of the OSI model. It deals with Layer 1 concerns, such as energy, bits and the media used to transport them, such as copper, fiber and wireless. Additionally, it deals with Layer 2 difficulties, including bit conversion into protocol units, such as Ethernet packets, media access control (MAC) addresses and NICs.
Types of network protocols
Generally speaking, there are three types of protocols in networking: communication, such as Ethernet; management, such as SMTP; and security, such as Secure Shell, or SSH.
Falling into these three broad categories are thousands of network protocols that uniformly handle an extensive variety of defined tasks, including authentication, automation, correction, compression, error handling, file retrieval, file transfer, link aggregation, routing, semantics, synchronization and syntax.
The following are the three types of protocols used in network communications:
- Network communication protocols. The efficiency of a network is determined by the communication protocols used. The formats and regulations that govern how data is exchanged between networks are formally described by these protocols. This applies to both hardware and software and is a requirement for communicating between computing systems and telecommunication systems. In addition to handling syntax, synchronization and semantic requirements that both analog and digital communications must meet to work, communication protocols also handle authentication and error detection. HTTP, UDP, TCP and Internet Relay Chat are network communication protocols.
- Network management protocols. To ensure steady communication and optimal performance throughout the network, network management protocols help specify the policies and processes needed to monitor, administer and maintain a computer network. They also assist in communicating these demands across the network. Simple Network Management Protocol (SNMP) and ICMP are network management protocols.
- Network security protocols. The primary responsibility of network security protocols is to ensure that the data in transit over the network connections are kept safe and secure. These protocols also specify how the network protects data from any unauthorized efforts to inspect or extract it. This ensures that unauthorized users, services or devices don't have access to the network. Protocols such as Secure Sockets Layer (SSL), Secure FTP and HTTP Secure (HTTPS) operate at this level.
How to employ network protocols
For network protocols to work, they must be coded within software -- either as part of the computer's operating system (OS) or as an application -- or executed within the computer's hardware. Most modern OSes possess built-in software services that are prepared to implement some network protocols. Other applications, such as web browsers, are designed with software libraries that support the protocols necessary for the application to function. In addition, TCP/IP and routing protocol support is implemented in direct hardware for enhanced performance.
Whenever a new protocol is implemented, it is added to the protocol suite. The organization of protocol suites is considered to be monolithic since all protocols are stored in the same address and built on top of one another.
What are the vulnerabilities of network protocols?
Network protocols are not designed for security. Their lack of protection can sometimes enable malicious attacks, such as eavesdropping and cache poisoning, to affect the system. The most common attack on network protocols is the advertisement of false routes, causing traffic to go through compromised hosts instead of the appropriate ones.
Cybercriminals frequently use network protocols in distributed denial-of-service assaults, which is another typical method of exploiting them. For example, in a SYN flood attack, an attacker takes advantage of the way TCP works. They send SYN packets to repeatedly initiate a TCP handshake with a server until the server is unable to provide service to legitimate users because its resources are tied up by all the fake TCP connections.
Network protocol analyzers are tools that protect systems against malicious activity by supplementing firewalls, antivirus programs and antispyware software.
Examples of network protocol uses
Network protocols are what make the modern internet possible since they enable computers to communicate across networks without users having to see or know what background operations are occurring. Some specific examples of network protocols and their uses are the following:
- Post Office Protocol 3, or POP3, is the most recent version of a standard protocol that is used for receiving incoming emails.
- SMTP is used to send and distribute outgoing emails.
- FTP is used to transfer files from one machine to another. The files can be multimedia files, program files, text files and documents.
- Telnet is a collection of rules used to connect one system to another via a remote login. The local computer sends the request for connection, and the remote computer accepts the connection.
- HTTPS is a common protocol used to protect communication between two computers, one of which is using a browser and the other of which is downloading data from a web server.
- Gopher is a set of rules used to search for, get hold of and display documents from remote sites. Gopher operates according to the client-server model.
Other network protocol examples include the following:
- ARP.
- Blocks Extensible Exchange Protocol, or BEEP.
- Border Gateway Protocol, or BGP.
- Binary Synchronous Communications, or BSC.
- Canonical Text Services, or CTS.
- Domain Name System, or DNS.
- Dynamic Host Configuration Protocol, or DHCP.
- Enhanced Interior Gateway Routing Protocol, or EIGRP.
- Human Interface Device, or HID, protocol.
- ICMP.
- Internet Message Access Protocol, or IMAP.
- MAC.
- Network News Transfer Protocol, or NNTP.
- Open Shortest Path First, or OSPF.
- SSL.
- SNMP.
- Thread.
- Transport Layer Security, or TLS.
- Universal Description, Discovery and Integration, or UDDI.
- voice over IP, or VoIP.
- X10.
Network protocols are the backbone of the internet, without which it wouldn't exist. Learn about the 12 most used network protocols, as well as their purposes and use cases.







