What is IMAP (Internet Message Access Protocol)?
IMAP (Internet Message Access Protocol) is a standard retrieval protocol for receiving email. It stores email messages on a mail server, enabling the recipient to view and manipulate them from any device.
IMAP enables users to organize messages into folders, flag messages for urgency or follow-up, and save draft messages on the server. Users can also have multiple email client applications that sync with the email server to show which messages have been read or are still unread.
How does IMAP work?
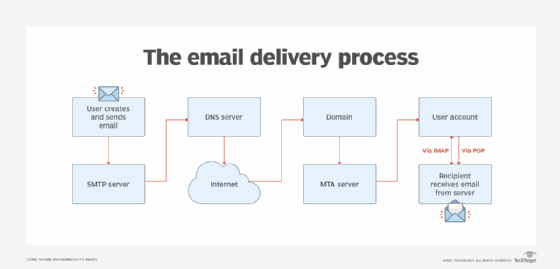
As an incoming email protocol, IMAP is the intermediary between the email server and the client. When users read an email using IMAP, they read them off the server. They don't download or store the email on their local devices. This means the email is not tied to a particular device, and users can access it from any location in the world using different devices, such as PCs, laptops, smartphones and tablets.
The following key points describe an IMAP operation:
- When a user signs in to an email client, like Microsoft Outlook, it uses IMAP to establish a connection to the email server using a designated port number.
- Once the user's username and password are verified, IMAP downloads messages to the client when the user selects a folder such as Inbox. Attachments are not automatically downloaded.
- Users can check their messages from different devices, automatically synchronizing changes across those devices.
- Email messages remain on the server until the user explicitly deletes them.
An IMAP server listens on port number 143, while IMAP over Secure Sockets Layer (SSL)/Transport Layer Security (TLS) is assigned port number 993.
IMAP, TCP and HTTP
Most modern client-server protocols operate between a web browser and a server or an app and an application programming interface. APIs are implemented on top of the base protocol, HTTP. HTTP is implemented on top of TCP, which ensures that data packets are delivered to their intended destination.
Like HTTP, IMAP is also implemented on top of TCP/IP. It works based on different types of requests, known as IMAP commands. A command in IMAP is similar to a request in HTTP. It either tells the server to do something or asks the server for some information.
An IMAP command generally looks like the following:
<tag> <command> [<arg1><arg2>…]
In the early 1990s, when network connections had low bandwidth, HTTP was necessary for retrieving email messages through IMAP, as it relied on efficient data transfer over slow internet connections.
Adding email accounts to IMAP
When an email account is added to an email app or IMAP client, it usually attempts to set it up with IMAP access. In that case, user inputs aren't required. But, if the account is already set up for Post Office Protocol 3 (POP3), the client might have difficulty adding it to IMAP.
If users still need to configure their accounts with IMAP, they must get the names of the POP3 and Simple Mail Transfer Protocol (SMTP) -- outgoing mail -- server from the email provider and then enter the following information into the client:
- IMAP server: imap.<name of service>.com
- POP3 server: pop.<name of service>.com
- SMTP server: smtp.<name of service>.com
How does sending and reading messages work with IMAP?
When a user opens their email client, it connects over the internet with an IMAP server through a specially designated port -- port 143 -- for standard messages or port 993 for encrypted messages. The IMAP server sends the user a list of email headers that display senders, subjects and other summary information about each message.
For each email message the user clicks to open, their email service downloads the message from the IMAP server. However, even after download, the message remains on the server. Since all email messages remain on the server unless the user deletes them, they can be accessed again from any device.
Changes made to emails, such as deleting or moving them, are synchronized by the IMAP server so that they appear on the server and on all devices used to access email. If the user deletes an email, that deletion is also synchronized by IMAP at all points. The email is deleted from all the user's devices and the IMAP server.
Differences between IMAP and POP3
Like IMAP, POP3 is a client-server email retrieval protocol. It is primarily used by internet service providers that offer email services. However, there are distinct differences between IMAP and POP3.
POP3 begins by contacting the user's email service so it can download all new email messages onto their device. However, POP3 limits the user to only accessing messages from that device. Once downloaded, POP3 automatically deletes all new messages from the server. Therefore, other than accessing that device, there is no way to get these messages back.
In contrast, IMAP stores all email on a remote server, which makes the email continuously retrievable from the server and any device. IMAP only opens an email when the user clicks on it. IMAP's popularity is growing due to the proliferation of mobile devices, like smartphones and tablets. IMAP is ideal for those who need to access their email on the go or use different devices.
Advantages of IMAP
IMAP offers users the following benefits:
- Supports multiple logins. Most implementations of IMAP support multiple logins. This enables users to connect to the email server simultaneously from different devices. For example, users could simultaneously access their email with an Outlook app on an iPhone and an Outlook desktop app.
- Provides accessibility. IMAP provides greater access for users who travel or need to check their email from different devices or locations. The protocol doesn't specify how to handle multiple connections; the details are left to the mail client developers.
- Enables mailbox sharing. The email service's shared mailboxes feature enables users to access and manage multiple emails within the same inbox. This is useful for team mailboxes or shared accounts where users view and respond to emails from a single email address.
- Supports multiple email functions. Users can organize emails on the server by creating folders and subfolders. They can also search and sort emails from the server, not just their device.
- Enables push mail. The IMAP server supports IDLE extensions or push mail, so the email is displayed in the inbox as unread, eliminating the need to set up a polling interval or require users to first click on Receive.
Limitations of IMAP
IMAP also has the following limitations:
- Resource usage. Because email messages remain on IMAP servers and are not automatically deleted upon transfer, IMAP uses more server resources, such as storage and processing.
- Speed. It takes more time to receive IMAP messages than with POP3. That's because IMAP continuously uses synchronization with email accounts in real time. This can slow down email delivery.
- Internet connection requirement. Since POP3 email is downloaded to the user's device, they can view these messages offline. However, since IMAP keeps all email messages on a server, the user can only view email with an internet connection.
- Complicated setup. IMAP is more complex than POP3. Although a user can configure an entire IMAP mail server, configuration errors can be easy to make. Email management with IMAP can also be complicated.
Security considerations for IMAP
Even though IMAP has an authentication mechanism, the authentication process can easily be circumvented by anyone who knows how to steal a password using a protocol analyzer because the client's username and password are transmitted as cleartext.
Administrators can work around this security flaw in an Exchange Server environment using SSL/TLS encryption for IMAP. Enabling multifactor authentication can also help add an extra layer of protection.
IMAP has additional security vulnerabilities because email messages remain on an IMAP server and internet access must be used to send and retrieve messages. In the process, internet traffic can be intercepted by bad actors, who can infiltrate the server and infect it with malware.
Organizations can use preventive techniques, such as implementing the IMAP email server on a zero-trust network using stringent firewall rules. They can also segment and secure networks at the segment level if it becomes necessary to restrict server access to a limited subset of users.
IMAP server configuration and maintenance are highly complex and subject to error. When installing or upgrading an IMAP server, users can create security vulnerabilities through oversights, which bad actors can discover and exploit.
Email continues to be a significant security vulnerability for many organizations. To contain these risks, they must follow security best practices.