project management
What is project management?
Project management is the discipline of using established principles, procedures and policies to guide a project from conception through completion.
Project management applies these best practices to ensure that a project is completed in a way that meets all articulated outcomes, from spending limits to end-goal objectives.
The effort often begins with a project charter, a short formal document that provides project managers with written authority to begin work and outlines the goals, objectives, resource requirements, stakeholders and potential challenges. The project plan scopes out these elements in detail and informs the management of all aspects of the project, including roadblocks or surprises that might arise.
Project management commonly involves overseeing people from multiple parts of a company, sometimes from multiple organizations, who must work together for part or all of the project's duration to reach the common goal. Project managers, thus, need to communicate effectively across many disciplines and inspire people to work in concert to deliver a successful project.
What is a project?
To fully appreciate the value of project management, it's important to understand what a project is.
A project is an undertaking with specific start and end parameters designed to produce a defined outcome, such as implementing a new computer system. Moreover, it is a temporary endeavor and, as such, is different from ongoing processes, such as a governance program or an asset management program.
Of course, projects have existed throughout history, and people have been managing projects for millennia. However, it wasn't until the mid-20th century that the art and science of shepherding a project from beginning to end became a formal management discipline.
Professional organizations codify project management
Several key events in the second half of the 20th century helped formalize project management. The International Management Systems Association, a federation of dozens of existing PM associations from around the world -- later renamed the International Project Management Association -- was founded in 1965 to promote project management as a profession.
The Project Management Institute, or PMI, was founded soon after in 1969, with the goal of promoting, professionalizing and standardizing project management. PMI's certification program began in 1984. Its highly influential and periodically updated A Guide to the Project Management Body of Knowledge (PMBOK) debuted in 1996. The Association for Project Management, founded in 1972, is British professional certification organization for project and program management.
Various project management frameworks arose in conjunction with the establishment of these professional organizations. In addition to the traditional waterfall approach, which breaks projects into sequential steps, the late 20th century also saw the establishment of the agile project management and Critical Chain Project Management.
Elements of project management
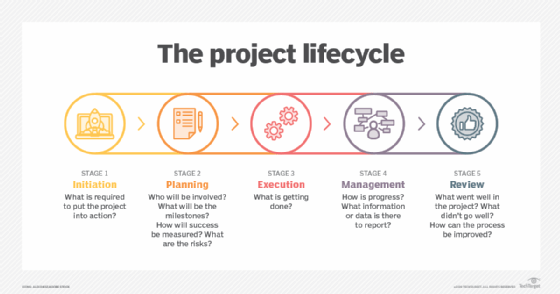
PMBOK divides project management into five processes or phases:
- Initiating
- Planning
- Executing
- Monitoring and controlling
- Closing
Additionally, project management professionals identify multiple discreet areas they must manage as part of their roles and responsibilities. The following areas commonly make the list:
- Integration
- Scope
- Time
- Cost
- Quality
- Procurement
- Human resources
- Communications
- Risk
- Stakeholder
Benefits of project management
Project management brings a repeatable process to organizing, executing and governing projects. Each project's objective is clearly articulated, workers' roles and responsibilities are identified, timelines for finishing tasks are set, and the reporting mechanism to measure and convey progress toward achieving incremental goals and the overall objective is established.
Through these fundamental elements, project management produces multiple benefits:
- Higher likelihood of success. In PM, the project's objective is clear, as are the steps required to achieve the objective.
- Efficiency. The advanced planning required in PM minimizes guess work and false starts. In addition, project management brings repeatable processes to bear, so there's no need to reinvent the wheel each time a new project starts.
- Lower costs and higher productivity. These benefits stem in large part from the higher rates of success and increased efficiency in running projects using PM principles.
- Great visibility into progress and problems. Project teams and project managers as well as executive sponsors know what work should be done when and, thanks to reporting, whether those milestones are being met.
- Improved communication. Project team members, managers and executive sponsors, and other key participants all have the same information about what work should be done, when it should be done and for what reasons.
- Greater alignment among all stakeholders. The detailed project plans, the increased visibility and improved communication mean everyone is more likely to know where they fit into a project workflow.
- Better levels of collaboration. In project management, work is timed to ensure that teams that must work together are all available when they need to be.
- More accountability. Worker roles and responsibilities are accurately defined, and expected milestones are clearly articulated in advance.
- Better risk monitoring and mitigation. Project managers are expected to identify risks in advance of a project and implement mitigations, so they're more apt to monitor for those risks and know how to respond if problems arise.
- Continuous improvement. Project managers take lessons learned and apply them to their subsequent endeavors.
Project management examples
Organizations use project management to run projects in nearly every functional area. For example, the project management discipline can be used to ensure the following are done effectively, efficiently and successfully:
- the implementation of an enterprise software system, such as a customer relationship management (CRM) platform;
- the development and release of a new product or service;
- the opening of a new office or store;
- the creation and launch of a marketing campaign; and
- the construction of a new building or structure.
What is a project manager?
A project manager is a professional who specializes in the project management discipline and understands how to effectively bring project management principles and practices to bear during the planning and execution of a project.
Project managers are responsible for making sure projects are successfully completed. They are expected to identify the tasks needed to complete the project; create a schedule for performing those tasks; and procure the resources needed to finish the project on time, on budget and to the project's target outcome.
For most projects in a typical organization, project managers oversee teams from multiple functional areas that are expected to work together during the project to reach the desired goal. Project managers must have strong leadership, interpersonal and communication skills.
Project managers are also expected to manage project risks and challenges by implementing appropriate controls and devising ways to overcome roadblocks as they arise. Quickly responding to changes and course-correcting if obstacles arise are also key to being a good project manager.
The project manager role is a specific position within an organization. It is not the same role as a business unit manager or functional manager, even if those managers are stakeholders in a project.
Training
Most project managers have a combination of specialized training in the project management discipline and on-the-job experience that has qualified them for the position. Moreover, many project managers have earned professional certifications. The most common and most widely recognized is the Project Management Professional designation from the PMI. Other certifications -- such as the Google Project Management Certificate -- are also well regarded.
Project managers typically also have a lengthy history of leading project work in addition to or in place of earning a certification. Many start as project coordinators on smaller projects and then work in that role on increasingly complex projects. They may also move directly into project manager positions on small projects. Junior project professionals work under senior PMs to learn on the job.
Project managers often advance in their profession by leading increasingly larger and more complex projects, by becoming program or portfolio managers, or by becoming directors of a project management office.
Many project managers also have at least a working knowledge of one more or business functions, such as technology, operations or marketing. This background helps them more effectively lead projects involving those departments.
Background in methodologies and tools
Project managers also know how to work in the various project management methodologies. They are skilled in knowing which methodology -- or combination of methodologies -- would be best for any given project given the project objectives and available resources.
Similarly, they're skilled in selecting the best project management software and tools to help them shepherd projects from the initial planning phase through execution and post-mortem.
Strong demand for project managers
The U.S. Bureau of Labor Statistics predicted that employment for project management specialists will grow 7% from 2021 to 2031. The BLS estimated an average of about 70,400 openings for project managers each year over the decade. The job site Indeed put the average base salary for a project manager in early 2023 at $84,250. Here are the top questions companies use to interview project managers.
Responsibilities of a project manager
Managing a project involves multiple steps. Although the terminology for these steps varies, they often include the following:
- defining project goals;
- outlining the steps needed to achieve those goals;
- identifying the resources required to accomplish those steps;
- determining the budget and time required for each of the steps, as well as the project as a whole;
- overseeing the actual implementation and execution of the work; and
- delivering the finished outcome.
As part of a strong project management plan, project managers implement controls to assess performance and progress against the established schedule, budget and objectives laid out in the project management plan. This is often referred to as the project scope.
Project management methodologies
There are various methodologies that project managers can employ to deliver a successful project:
- Agile. A methodology used for speed and flexibility, which features short delivery cycles.
- Critical chain project management. An approach that focuses on the use of resources, rather than on timelines.
- Critical path method. A step-by-step PM technique.
- Lean project management. The application of lean manufacturing principles to project management
- Prince2. Originated in the U.K. and still widely used by the U.K. government to manage projects, this approach has also been adopted by private industry internationally.
- Waterfall. A management style that is sequential in nature.
There are other methodologies tailored to certain types of projects. For example, rapid application development is most often used in software development to encourage the quick development of applications while still maintaining high quality. There are also methodologies that emphasize specific values. For example, the Prism methodology focuses on sustainability and integrates that idea into project phases to reduce negative environmental and social effects. Other approaches include joint application development, the fountain model, the spiral model, build and fix, and synchronize-and-stabilize.

Hybrid approaches in project management
Some project managers use a hybrid approaches, incorporating other management frameworks and methodologies into their PM methodologies. For instance, Six Sigma, which was originally developed at Motorola and is designed to eliminate waste and improve processes, can be adopted for PM. Similarly, the Agile methodology employs Scrum, a management process featuring short sprints to get chunks of work done. Lean manufacturing principles are used in lean project management.
A number of charting methods, such as the Gantt chart and PERT chart have been developed as tools to create a graphic representation of a project plan and its current status. Multiple PM software options are available to project managers to aid in monitoring project tasks and project.
Project management vs. operations management
Operations management and project management both involve the effective allocation of resources to deliver outcomes in the most efficient and most effective manner possible and at the highest levels of quality possible given the resources assigned to the endeavors.
Operations management is also focused on delivery of outcomes.
However, operations management differs from project management in its ongoing nature. Operations management focuses on the continual delivery of the same products or services using repeatable processes and the same project teams.
Project management vs. product management
Organizations value project management for its ability to keep projects on task and on budget and for its focus on completing projects to established outcomes.
Organizations in the 21st century increasingly adopted product management as a complementary discipline.
Although both disciplines focus on managing business endeavors, their roles are different. Project managers manage projects -- temporary endeavors that have predetermined start and end points. Product managers, on the other hand, are responsible for an entire product and own its success as well as the maintenance of it through its entire lifecycle.







