What is cybercrime and how can you prevent it?
What is cybercrime?
Cybercrime is any criminal activity that involves a computer, network or networked device.
While most cybercriminals use cybercrimes to generate a profit, some cybercrimes are carried out against computers or devices to directly damage or disable them. Others use computers or networks to spread malware, illegal information, images or other materials. Some cybercrimes do both -- i.e., target computers to infect them with a computer virus, which is then spread to other machines and, sometimes, entire networks.
A primary effect of cybercrime is financial. Cybercrime can include many different types of profit-driven criminal activity, including ransomware attacks, email and internet fraud, and identity fraud, as well as attempts to steal financial account, credit card or other payment card information.
As cybercriminals might target an individual's private information or corporate data for theft and resale, it's especially important to protect backup data.
The U.S. Department of Justice (DOJ) divides cybercrime into the following three categories:
- Crimes in which the computing device is the target -- for example, to gain network access.
- Crimes in which the computer is used as a weapon -- for example, to launch a denial-of-service (DoS) attack.
- Crimes in which the computer is used as an accessory to a crime -- for example, using a computer to store illegally obtained data.
The Council of Europe Convention on Cybercrime, to which the U.S. is a signatory, defines cybercrime as a wide range of malicious activities, including the illegal interception of data, system interferences that compromise network integrity, and availability and copyright infringements.
The necessity of internet connectivity has enabled an increase in the volume and pace of cybercrime activities because criminals no longer need to be physically present when committing a crime. The internet's speed, convenience, anonymity and lack of borders make computer-based variations of financial crimes -- such as ransomware, fraud and money laundering, as well as crimes such as stalking and bullying -- easier to carry out.
Cybercriminal activity can be carried out by individuals or groups with relatively little technical skill or by highly organized global criminal groups that could include skilled developers and others with relevant expertise. To further reduce the chances of detection and prosecution, cybercriminals often choose to operate in countries with weak or nonexistent cybercrime laws.
How cybercrime works
Cybercrime attacks can begin wherever there is digital data, opportunity and motive. Cybercriminals include everyone from the lone user engaged in cyberbullying to state-sponsored actors, such as China's intelligence services.
Cybercrimes generally do not occur in a vacuum; they are, in many ways, distributed in nature. That is, cybercriminals typically rely on other actors to complete the crime. This is whether it's the creator of malware using the dark web to sell code, the distributor of illegal pharmaceuticals using cryptocurrency brokers to hold virtual money in escrow or state threat actors relying on technology subcontractors to steal intellectual property.
Cybercriminals use various attack vectors to carry out cyberattacks and are constantly seeking new methods and techniques to achieve their goals, while avoiding detection and arrest.
Cybercriminals often conduct activities using malware and other types of software, but social engineering is usually an important component of executing most types of cybercrime. Phishing emails are another important component to many types of cybercrime but especially for targeted attacks, such as business email compromise, in which an attacker attempts to impersonate, via email, a business owner to convince employees to pay out bogus invoices.
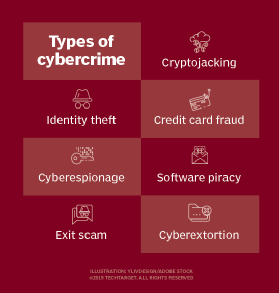
Types of cybercrime
Cybercriminals have a plethora of cybercrime types to conduct malicious attacks. Most attackers carry out cybercrimes with the expectation of financial gain, though the ways cybercriminals get paid can vary. Specific types of cybercrimes include the following:
Cyberextortion
This crime involves an attack or threat of an attack coupled with a demand for money to stop the attack. One form of cyberextortion is a ransomware attack. Here, the attacker gains access to an organization's systems and encrypts its documents and files -- anything of potential value -- making the data inaccessible until a ransom is paid. Usually, payment is in some form of cryptocurrency, such as bitcoin.
Cryptojacking
This attack uses scripts to mine cryptocurrencies within browsers without the user's consent. Cryptojacking attacks can involve loading cryptocurrency mining software to the victim's system. Many attacks depend on JavaScript code that does in-browser mining if the user's browser has a tab or window open on the malicious site. No malware needs to be installed as loading the affected page executes the in-browser mining code.
Identity theft
This type of attack occurs when an individual accesses a computer to steal a user's personal information, which is then used to steal that person's identity or access their valuable accounts, such as banking and credit cards. Cybercriminals buy and sell identity information on darknet markets, offering financial accounts and other types of accounts, such as video streaming services, webmail, video and audio streaming, online auctions and more. Personal health information is another frequent target for identity thieves.
Credit card fraud
This is an attack that occurs when malicious hackers infiltrate retailers' systems to get their customers' credit card or banking information. Stolen payment cards can be bought and sold in bulk on darknet markets, where hacking groups that have stolen mass quantities of credit cards profit by selling to lower-level cybercriminals who profit through credit card fraud against individual accounts.
Cyberespionage
This crime involves cybercriminals hacking into systems or networks to gain access to confidential information held by a government or other organization. Attacks are motivated by profit or ideology. Cyberespionage activities include cyberattacks that gather, modify or destroy data, as well as using network-connected devices, such as webcams or closed-circuit TV cameras, to spy on a targeted individual or groups and monitoring communications, including emails, text messages and instant messages.
Software piracy
This attack involves the unlawful copying, distribution and use of software programs with the intention of commercial or personal use. Trademark violations, copyright infringements and patent violations are often associated with software piracy.
Exit scam
The dark web has given rise to the digital version of an old crime known as the exit scam. In today's form, dark web administrators divert virtual currency held in marketplace escrow accounts to their own accounts -- essentially, criminals stealing from other criminals.
Common examples of cybercrime
Commonly seen cybercrime attacks include:
- Distributed DoS (DDoS) attacks, which use a network's own communications protocol against it by overwhelming its ability to respond to connection requests. DDoS attacks are sometimes carried out for malicious reasons or as part of a cyberextortion scheme, but they can also be used to distract the victim organization from some other attack or exploit carried out at the same time.
- Malware is another common cybercrime that can damage systems, software or data stored on a system. Ransomware attacks are a type of malware that encrypts or shuts down victim systems until a ransom is paid.
- Phishing campaigns help attackers infiltrate corporate networks. Phishing includes sending fraudulent emails to users in an organization, enticing them to download malicious attachments or click on malicious links that then spread the malware across the network.
- In credential attacks, a cybercriminal aims to steal or guess victims' usernames and passwords. These attacks can use of brute-force -- for example, by installing keylogger software -- or by exploiting software or hardware vulnerabilities that expose the victim's credentials.
- Cybercriminals can also hijack websites to change or delete content or to access or modify databases without authorization. For example, attackers use Structured Query Language injection exploits to insert malicious code into a website, which can then be used to exploit vulnerabilities in the website's database, enabling a malicious hacker to access and tamper with records or gain unauthorized access to sensitive information and data, such as customer passwords, credit card numbers, personally identifiable information, trade secrets and intellectual property.
Other common examples of cybercrime include illegal gambling, the sale of illegal items -- such as weapons, drugs or counterfeit goods -- and the solicitation, production, possession or distribution of child pornography.
Effects of cybercrime on businesses
The true cost of cybercrime is difficult to assess accurately. Cybersecurity Ventures reported that global cybercrime grows by 15% annually, with it expected to reach $10.5 trillion by 2025.
While the financial losses due to cybercrime can be significant, businesses can also suffer other disastrous consequences as a result of criminal cyberattacks, including the following:
- Damage to investor perception after a security breach can cause a drop in the value of a company.
- Businesses could face increased costs for borrowing and greater difficulty in raising more capital as a result of a cyberattack.
- Loss of sensitive customer data can result in fines and penalties for companies that have failed to protect their customers' data. Businesses might also be sued over the data breach.
- Damaged brand identity and loss of reputation after a cyberattack undermine customers' trust in a company and that company's ability to keep their financial data safe. Following a cyberattack, firms could lose current customers and lose the ability to gain new customers.
- Businesses might incur direct costs from a criminal cyberattack, including increased insurance premium costs and the cost of hiring cybersecurity companies for incident response and remediation, as well as public relations and other services related to an attack.
Effects of cybercrime on national defense
Cybercrimes can have public health and national security implications, making computer crime one of DOJ's top priorities. In the U.S., at the federal level, the Federal Bureau of Investigation's (FBI) Cyber Division is the agency within DOJ charged with combating cybercrime. The Department of Homeland Security (DHS) sees strengthening the security and resilience of cyberspace as an important homeland security mission. Cybersecurity and Infrastructure Security Agency (CISA), a division of DHS, aims to improve the resilience and security of cyber and physical infrastructure. Other agencies, such as the U.S. Secret Service (USSS) and U.S. Immigration and Customs Enforcement (ICE), have special divisions dedicated to combating cybercrime.
USSS' Electronic Crimes Task Force, for example, investigates cases that involve electronic crimes, particularly attacks on the nation's financial and critical infrastructures. USSS also runs the National Computer Forensics Institute, which provides state and local law enforcement, judges and prosecutors with computer forensics training.
The Internet Crime Complaint Center, a partnership among the FBI, National White Collar Crime Center and Bureau of Justice Assistance, accepts online complaints from victims of internet crimes or interested third parties.
How to prevent cybercrime
While it isn't possible to completely eradicate cybercrime and ensure complete internet security, businesses can reduce their exposure to it by maintaining an effective cybersecurity strategy using a defense-in-depth approach to securing systems, networks and data.
Organizations can reduce cybercrime risks with the following:
- Develop clear policies and procedures for the business and employees.
- Create cybersecurity incident response plans to support these policies and procedures.
- Outline the security measures in place about how to protect systems and corporate data.
- Use multifactor authentication (MFA) apps or physical security keys.
- Activate MFA on every online account when possible.
- Verbally verify the authenticity of requests to send money by talking to a financial manager.
- Create intrusion detection system rules that flag emails with extensions similar to company emails.
- Scrutinize all email requests for transfer of funds to determine if the requests are out of the ordinary.
- Train employees on cybersecurity policies and procedures and what to do in the event of a security breach.
- Keep websites, endpoint devices and systems current with all software release updates or patches.
- Back up data and information regularly to reduce the damage in case of a ransomware attack or data breach.
Information security and resistance to cybercrime attacks can also be built by encrypting local hard disks and email platforms, using a virtual private network and using a private, secure domain name system server.
Cybercrime legislation and agencies
Various U.S. government agencies have been established to deal specifically with the monitoring and management of cybercrime attacks. The FBI's Cyber Division is the lead federal agency for dealing with attacks by cybercriminals, terrorists or overseas adversaries. Within DHS, CISA coordinates between private sector and government organizations to protect critical infrastructure.
The Cyber Crimes Center (C3) within ICE provides computer-based technical services that support domestic and international investigations included in the Homeland Security Investigations (HSI) portfolio of immigration and customs authorities. C3 focuses on cybercrimes that involve transborder illegal activities. It is responsible for finding and targeting all cybercrimes within HSI jurisdiction. C3 includes the Cyber Crimes Unit, Child Exploitation Investigations Unit and Computer Forensics Unit.
Various laws and legislation have also been enacted. In 2015, the United Nations Office on Drugs and Crime released a cybercrime repository, a central database that includes legislation, previous findings and case law on cybercrime and electronic evidence. The intention of the cybercrime repository is to assist countries and governments in their attempts to prosecute and stop cybercriminals.
Cybercrime legislation dealing can be applicable to the general public or sector-specific, extending only to certain types of companies. For example, the Gramm-Leach-Bliley Act focuses on financial institutions and regulates the implementation of written policies and procedures to improve the security and confidentiality of customer records, while also protecting private information from threats and unauthorized access and use.
Other legislation has been established to deal with specific cybercrimes, such as cyberbullying and online harassment. A little over half of U.S. states have implemented laws dealing directly with these crimes. For example, Massachusetts law cites that cyber-stalking is a crime punishable with a fine of up to $1,000, a maximum of five years in jail or both. In Tennessee, online harassment and stalking is considered a Class A misdemeanor, and a convicted cybercriminal can face a jail sentence of, at most, 11 months and 29 days, a fine of up to $2,500 or both.
The definition was written by Kate Brush and Michael Cobb in 2021. TechTarget editors revised it in 2024 to improve the reader experience.






