How to plan a successful IoT deployment
Effective IoT deployment enables data-driven insights but requires careful planning, strong infrastructure and strategies to overcome key challenges.
The internet of things (IoT) has revolutionized business strategy, operations, forecasting and crisis management. Real-world data collected from IoT deployments – once it's thoroughly analyzed – provides detailed insights and startlingly accurate predictions that were impossible just a few years ago.
But IoT deployments are complex undertakings that often involve millions of individual devices, each connected to a TCP/IP network and requiring constant management. Collectively, these IoT devices deliver enormous amounts of quality data that must be stored, analyzed and even acted upon in real time.
Consequently, IoT deployment is the process of designing, procuring, installing and maintaining a functional IoT system. Effective deployment is crucial to any gainful IoT program – and perhaps the long-term fate of the entire enterprise. Indeed, successful IoT deployment requires copious planning and preparation at the project's outset, joined by best practices and careful management to overcome common deployment hurdles.
Why is IoT deployment important?
The old 5Ps principle, "Proper planning prevents poor performance," perfectly suits modern IoT environments. At a glance, an IoT deployment seems straightforward:
- Power an IoT device.
- Connect it to a network.
- Receive and store its data.
- Process and analyze the data using available compute resources.
That's the fundamental idea.
But today's sprawling IoT environments typically present a much greater challenge to IT infrastructures than a single device. Consider these common implications of IoT environments:
- There can be thousands – even millions – of devices involved in an IoT deployment. All must be installed, powered, connected, configured, managed and maintained.
- IoT devices require consistent IoT connectivity to send real-time data to the network – and often each other. Network connectivity is vital for data quality and ongoing device monitoring and management too.
- The IoT network must offer adequate bandwidth and latency to support real-time data streams from the entire IoT environment.
- The IoT network must be reliable and robust enough to minimize data loss from factors including network disruptions or physical interference. Reliability ensures data quality, especially important for mission-critical applications such as health monitoring.
- The vast volume of IoT data arriving from the IoT environment must be stored, protected and secured – sometimes demanding the use of full-featured data warehouse technologies. Data security and retention policies must meet regulatory compliance obligations.
- IoT data must be processed and analyzed at the edge, demanding extensive computing resources. In turn, this often places enormous demands on a local data center and typically requires highly scalable computing environments such as a public cloud.
Proper design and deployment planning are foundational to any organization's IoT investment. They ensure the project is executed in a timely and cost-effective manner, performs as required and ultimately delivers the benefits that justified the project in the first place.
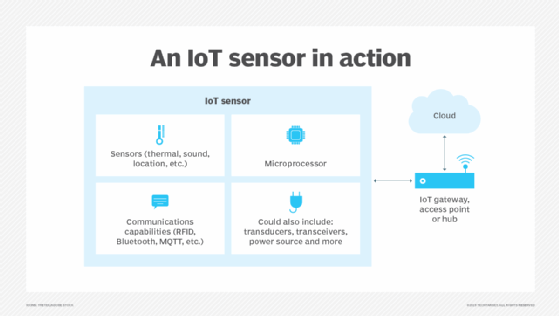
Best practices when planning an IoT deployment
There is no single methodology for designing or deploying an IoT project. Architectures, device selections and plans for use vary as dramatically as business needs, project scope, staff skills and available budget. However, common best practices for IoT design and deployment frequently include:
- Define objectives. A solid project plan starts with a clear definition of its intended scope, business goals and projected outcomes. What is the IoT project's reach? What does the IoT project bring to the business? How exactly does the business benefit from the IoT deployment?
- Assess feasibility. Determine the required infrastructure elements and their costs, including devices, networks, storage, computing and staffing, as well as data protection and regulatory compliance needs. After this review, some IoT projects are scaled back or scrapped due to high costs, inadequate staff expertise or technical concerns such as poor 5G connectivity in remote areas.
- Establish measures of success. Clear business objectives enable leaders to define IoT success and how it's measured. Key performance indicators are frequently used to assess and track a company's progress in reaching its stated goals. For example, a project intended to reduce downtime makes calculations after an IoT deployment, objectively reporting lost time, associated costs and other relevant information.
- Design the architecture. Skilled IoT architects design the IoT environment, giving careful consideration to devices such as sensors and actuators, network, storage and processing, as well as analytical applications. For example, common IoT architectures employ edge computing to collect, store and prepare data near its origin before relaying that processed data to a centralized location for analysis. Architectural planning such as this mitigates network latency while also addressing future scalability.
- Complete architectural details. Given an overall architectural design, IoT planners then fill in the details, selecting appropriate IoT devices – sensors and actuators – based on design needs – from temperature to pressure sensors. Moreover, selecting advantageous device locations homogenizes device density and minimizes physical interference. Designers choose networks with the desired configuration and connectivity, adding security such as encryption and authentication to protect and manage the IoT devices.
- Scrutinize data management. Determine storage requirements and necessary resources for this valuable IoT data, from backup and security to retention policies, while meeting current regulatory obligations. Also consider computational resources needed to analyze and act upon IoT data. For example, if cloud computing is used for data analytics, examine how that data is stored in or transferred to the public cloud.
- Test before deployment. Testing and validation are vital. Limited proof of concept testing confirms proper design and configuration selections – or identifies and resolves possible problems before full IoT deployment. Testing typically measures device ranges or varied operational conditions, such as altered power settings. Also, testing validates network traffic and even the entire IoT workflow from data collection to analysis.
- Deploy the IoT system. With high confidence in a well-conceived plan, designers delve into specifics such as timelines and deployment phases, considering proper installation and configuration issues for each device.
- Monitor. IoT tools oversee the IoT environment and each device's configuration and performance, pinpointing issues for investigation and correction. Ongoing IoT maintenance also includes battery replacement and device upgrades. Finally, monitoring minimizes the impact of damaged or malfunctioning IoT devices or networks, protecting long-term data quality and stabilizing IoT projects.
Common IoT deployment challenges
IoT deployments, complex as they are, involve more than device choices and network architecture. Designers face a host of potential challenges when building an IoT infrastructure, including:
- Data security and data privacy. Collected IoT data, often sensitive or personal in nature, requires secure, private storage in accordance with prevailing regulatory requirements, from the Health Insurance Portability and Accountability Act for medical monitoring devices in the U.S. to the General Data Protection Regulation for data collected across the EU.
- Data quality. IoT is fundamentally a real-time activity, and data is occasionally lost or corrupted. This reduces data quality, impacting analytical accuracy or outcomes. Include mechanisms to review data quality and address issues such as lost data or outliers during processing or analysis.
- Data analytics. Collect and store data only with a clear view of how that data is analyzed and how that analysis provides meaningful business insights. Understand why the IoT environment exists in the first place and validate any resultant business value. If insufficient, collect different data – or change the parameters of the analysis.
- Vulnerability to attack. Large IoT deployments present an enormous attack surface, risking data snooping and broader unauthorized access. Comprehensive device monitoring and management, such as network intrusion protection systems, reduce these vulnerabilities.
- Connectivity issues. IoT needs stable and consistent network connectivity. Remote, mobile and highly obscured environments present significant connectivity problems that reduce data volumes and quality. Also, connectivity affects the IoT environment's interoperability and scalability.
- Scalability. IoT device infrastructures often grow and extend over time. An IoT environment, while well designed for current goals, sometimes fails to meet changing needs. Review the design and how to support more and different devices for future growth – all while maintaining adequate IoT performance.
- Device maintenance. IoT devices are tiny computers requiring onboard software components such as firmware. Firmware is routinely updated to add device features, fix bugs and address newly uncovered security or performance issues. Unfortunately, limited connectivity and processing power mean extended downtime for firmware updates and other maintenance tasks. On the one hand, overlooked maintenance leaves the entire IoT infrastructure more vulnerable to attack. Regular maintenance also brings undesirable downtime for the IoT environment.
- Power management. Most IoT devices are battery-powered, forcing IoT designs to trade battery life for data volume. For example, IoT designs intended for continuous data transmission and enhanced features, such as encryption, typically use more battery power than other IoT devices. Energy harvesting, including solar panel use to recharge IoT batteries, eases some device and battery replacement concerns.
Stephen J. Bigelow, senior technology editor at TechTarget, has more than 30 years of technical writing experience in the PC and technology industry.








