What is the principle of least privilege (POLP)?
The principle of least privilege (POLP) is a concept in computer security that limits users' access rights to only what's strictly required to do their jobs. POLP can also restrict access rights for applications, systems and processes to only those who are authorized. This principle is also known as the access control principle or the principle of minimal privilege.
POLP is considered a cybersecurity best practice, as it restricts access to high-value data and assets. In addition, organizations that use POLP can improve their security posture by reducing their attack surface. It's also used in zero-trust network access (ZTNA).
Depending on the system, some privileges might be based on attributes contingent on the user's role within the organization. For example, some corporate access systems grant the appropriate level of access based on factors such as location, seniority or time of day. An organization can specify which users can access what in the system, and the system can be configured so that the access controls recognize only the administrators' roles and parameters.
Why is POLP important?
As a security measure, the principle of least privilege limits user and administrator access to nonessential information. This reduces an organization's attack surface. By enforcing POLP on user devices, any device that becomes infected with malware can't access elevated privileges that might increase access to further information, saving an organization from further potential damage. Likewise, the principle stops employees from intentionally or unintentionally damaging critical systems.
From a business risk perspective, POLP's ability to reduce the enterprise's attack surface is advantageous. By strictly limiting user and administrator access to only the information and resources essential for their job functions, POLP minimizes the potential blast radius of a security incident. If a user account or an endpoint device is compromised, the attacker is constrained from moving laterally across the network, escalating privileges or exfiltrating sensitive data.
As a cybersecurity best practice, POLP is also an integral part of ZTNA. ZTNA implements the zero-trust concept and controls access to enterprise resources at a network level. It uses identity-based authentication to establish trust and provide access. In the ZTNA framework, POLP provides the ability to accurately identify applications and application functions across a port or protocol.
PLOP also provides a tangible return on investment for enterprises. By preventing the widespread propagation of malware and containing the effects of security incidents, organizations can reduce costs associated with incident response, forensic investigations, system recovery and potential regulatory fines or legal actions. POLP also minimizes disruptions to critical business operations that can result from accidental or intentional misuse of elevated privileges by employees, safeguarding productivity and preventing costly errors.
At the board level, the POLP sends a powerful signal of strong governance and accountability. By enforcing strict role-based access control (RBAC), organizations demonstrate a proactive security posture that directly aligns with investor expectations and regulatory mandates. This not only reduces exposure to breaches but also supports compliance with SEC cybersecurity disclosure rules, which increasingly demand transparent oversight and board engagement in cybersecurity.
How does POLP work?
The principle of least privilege grants users permission to read, write or execute only the files or resources necessary to do their jobs. Time-limited privileges can also be enabled to ensure users have access to critical data for just the amount of time needed to perform a specific task. Without this principle, an organization could create overprivileged users, which could increase their chances of data breaches and malicious actions.
In practice, organizations implement POLP by first identifying the minimum set of permissions each role requires, then configuring systems to grant only those specific privileges. When a user or system needs to perform a task, authentication and authorization mechanisms verify their identity and check if they have appropriate permissions before granting access.
Privileges are regularly reviewed and adjusted as roles change. Temporary elevated access is granted only when necessary and revoked immediately afterward.
How to implement POLP in your organization
Organizations should adopt POLP as a default security measure to ensure that no employee has access to critical information they don't need. Likewise, the number of privileged accounts should be kept at a minimum.
For example, system administrators are typically privileged accounts, as they help other employees with their software and hardware. Some system administrators might be given unlimited privileges, making them a bigger target for attackers. As such, minimal privileges should also be placed on system administrators, limiting the total number of users they have access to.
When configuring new systems or applications, all unnecessary services, applications and data should be disabled. This includes any applications that might be enabled by default.
Organizations should also log authentication and authorizations to critical systems. This way, they can keep track of failed login attempts and access control changes. These can be a sign of threat actors. Organizations also should review accounts and privileges at regular intervals to ensure there are no overprivileged users.
Applying POLP concepts can be as simple as eliminating end-user access to devices, such as removing USB drives to prevent the exfiltration of classified information, or more involved operations, such as conducting regular privilege audits.
Organizations can take the following steps to implement POLP:
- Conduct privilege audits. All existing processes, programs and accounts should be reviewed to ensure there's no privilege creep, where people end up with more access than they need.
- Start with least privilege. All accounts should begin with the least privilege. Additional privileges should be added according to the access required.
- Ensure separation of privileges. It's important to distinguish between higher-level privilege accounts and lower-level privilege accounts.
- Assign just-in-time least privileges. This should be done by providing lower-level privilege accounts with limited access to complete the necessary task.
- Track and trace individual actions. All actions conducted by one-time-use credentials should be tracked to avoid potential damage.
- Train employees. All employees need to understand the importance of POLP and how their access is tied to security.
Effective adoption of POLP is supported by security tools and frameworks such as RBAC and privileged access management (PAM). RBAC helps define specific roles with finely tuned permissions, aligning access with job responsibilities.
PAM tools complement this by controlling and monitoring high-risk accounts, enforcing strict access protocols, enabling session monitoring and maintaining detailed audit trails. Together, these tools make it easier for organizations to enforce POLP while maintaining operational efficiency and compliance.
Benefits of using principle of least privilege
POLP can provide organizations with the following benefits:
- Prevents the spread of malware. By imposing POLP restrictions on computer systems, malware attacks can't use higher-privilege or administrator accounts to install malware or damage the system.
- Decreases the chances of a cyberattack. Most cyberattacks occur when a hacker exploits privileged credentials. POLP protects systems by limiting the potential damage that an unauthorized user gaining access to a system can cause.
- Improves user productivity. Only giving users the required access to complete their necessary tasks means higher productivity and less troubleshooting.
- Helps demonstrate compliance. In the event of an audit, an organization can prove its compliance with regulatory requirements by presenting the POLP concepts it has implemented.
- Helps with data classification. POLP concepts enable companies to keep track of who has access to what data in the event of unauthorized access.
- Reduces human error. Users with limited access are less likely to accidentally delete, modify, or misconfigure critical systems. This leads to greater system stability and fewer costly mistakes.

Challenges of POLP and how to overcome them
Implementing the principle of least privilege is a critical security measure, but it comes with various challenges, including the following:
- Complex IT environments. In large, complex organizations with numerous applications, systems and diverse job roles, precisely determining the absolute minimum permissions required for every user and process can be extremely time-consuming and difficult. Legacy systems, poorly documented processes and constantly evolving roles make it even harder to get a granular view of true access requirements.
- Overprovisioning and privilege creep. Privilege creep occurs when users gradually accumulate access rights that they no longer need through role changes, temporary assignments or excessive initial provisioning. Over time, this creates a hidden and growing set of permissions that expose organizations to risk, inflating the attack surface and increasing the likelihood of insider threat or compromise.
- Securing executive buy-in. When implementing the POLP, securing executive buy-in is a significant hurdle. Executives often focus on operational efficiency and might view access restrictions as barriers to productivity. This perception can lead to resistance, driven by concerns over potential effects on business agility and the overall user experience.
- Resistance to change. Implementing POLP often encounters internal resistance, as users accustomed to broad administrative access might perceive new restrictions as obstacles rather than protective measures. This resistance is typically rooted in ingrained habits. Poor communication about the rationale and benefits of access limitations can amplified resistance. insufficient early involvement of key stakeholders in the change process.
- Over-restriction. Over-restricting access through POLP can sometimes backfire. When systems are locked down too tightly, users might feel hindered and frustrated, leading to workarounds and a spike in help-desk requests. In extreme cases, it can trigger the rise of shadow IT, where employees resort to unauthorized tools to complete tasks, unintentionally elevating security and compliance risks.
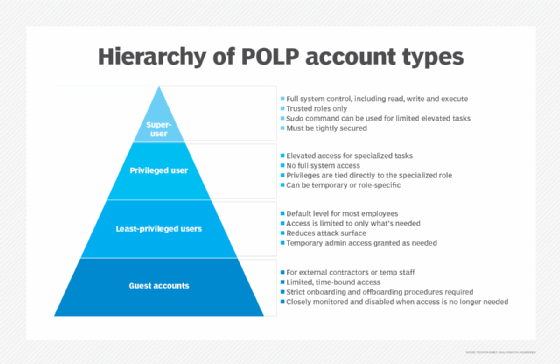
Principle of least privilege account types
The following are the primary account types associated with POLP:
Superuser account
A superuser is an IT staff member who needs unlimited privileges so they have full read, write and execute authority, and can make changes across a network. This includes installing software, modifying settings and files, and deleting data and users. Superuser accounts are the highest level of privilege and are only given to the most trusted individuals, usually system administrators or the equivalent. The superuser account is also known as an administrator account and is often dubbed root.
To prevent their sessions from being hijacked, superusers can type the sudo command into any account, enabling the account to perform a single command with superuser privileges temporarily. Ideally, superuser credentials aren't used for logging in. Since the superuser account has full control of the system, it must be protected from unauthorized access.
Privileged user accounts
Privileged users need temporary or occasional elevated access to perform specific, more specialized tasks within their domain. They don't need full system control. These accounts might include access to manage a specific database, administer a particular application or perform certain network configurations. The privileges are tied directly to the user's specialized role.
Least privileged users
LPUs are accounts with the most limited access and often the lowest level of authority within the company. In an organization, users often have elevated levels of access to the network and the data on it. When an LPU account is set up, that user has limited privileges and can perform only specific tasks, such as surfing the web or reading email. This makes it difficult for a malicious attacker to exploit an LPU account and cause harm.
Another way to control user access is by implementing a concept called privilege bracketing. This approach permits users access to administrator accounts for the shortest time necessary to complete the specific task. This function can be administered through special automated software to ensure that access is granted only for the specified amount of time.
Guest accounts
Designed for external users, such as contractors or temporary staff, these accounts provide limited and time-bound access to specific resources and have even fewer privileges than LPUs. These accounts should be closely monitored and disabled promptly once the need for access has ended.
For guest accounts, organizations must also follow strict onboarding and offboarding procedures to prevent lingering access or compliance gaps. Some organizations also use service accounts for automated processes and just-in-time accounts, which grant temporary elevated privileges only when needed.
What is privilege creep?
Privilege creep refers to the tendency of software developers to gradually add more access rights beyond what individuals need to do their jobs. This commonly happens when a user is given access that isn't revoked later.
For example, employees who are promoted might still need temporary access rights to certain systems for their old jobs. But, once they're settled in their new position, more access rights are added, and existing privileges often aren't revoked. This unnecessary accumulation of rights could cause major cybersecurity risks and result in data loss or theft.
Learn how to implement least privilege access in the cloud to control and manage cloud policies.






