What is third-party risk management (TPRM)?
Third-party risk management (TPRM) is a comprehensive framework for identifying, assessing and mitigating risks associated with using external vendors, suppliers, partners and service providers. In today's interconnected business environment, organizations increasingly rely on third parties, which can introduce financial, operational, regulatory, cybersecurity and reputational risks.
TPRM is a specialized subset of broader risk management, which covers all potential threats to an organization. While general risk management focuses on internal risks, TPRM addresses the challenges external entities pose, ensuring organizations safeguard their operations, maintain regulatory compliance and mitigate risks associated with vendor relationships.
TPRM is crucial for businesses for all the reasons mentioned above: safeguarding operations, ensuring compliance, and protecting against financial and reputational damage. Many modern organizations depend on third parties for operational efficiency. When these vendors or suppliers fail to deliver their services, organizations can suffer severe and lasting consequences. For instance, take an organization that relies on a service provider for hosting its website or cloud application. If the provider experiences downtime, the organization's digital presence becomes inaccessible.
Types of third-party risk
Third-party risks can be categorized into key areas, each affecting an organization's operations, security and compliance. The following are some of the most critical types:
- Operational risk. An operational risk occurs when disruptions in a vendor's ability to deliver goods or services result in downtime or failures in business operations.
- Cybersecurity risk. This risk often comes from data breaches, ransomware attacks, or other security vulnerabilities stemming from third-party vendors.
- Regulatory and compliance risk. This risk arises when vendors fail to adhere to industry regulations, potentially resulting in legal penalties.
- Financial risk. Financial risk happens when vendors face financial instability, bankruptcy or fraudulent activities, potentially disrupting service continuity.
- Reputational risk. Negative publicity or unethical behavior by third-party providers that damage an organization's brand raise this risk.
- Fourth-party risk. This risk stems from a vendor's subcontractors, often caused by limited visibility into extended supply chains.
- Geopolitical risk. These threats come from instability and issues affecting international vendors, such as trade restrictions, sanctions or political upheaval.
- Strategic risk. This risk arises when vendors fail to align with an organization's long-term goals, leading to inefficiencies and missed opportunities.
Types of third-party vendors
Third-party vendors provide a complex network of external relationships. They require careful management because each vendor category introduces unique risks. Businesses that typically manage a diverse ecosystem of third-party vendors include the following:
- Software providers who deliver critical applications and platforms.
- Hardware suppliers who provide physical infrastructure and equipment.
- Cloud service providers (CSPs) offering hosting, storage and computing resources.
- Professional service firms including consultants, auditors and legal advisors.
- Contractors who handle specialized or temporary work.
- Outsourced service providers managing functions such as customer support, human resourses and accounting.
- Data processors who handle sensitive information.
- Marketing and advertising agencies.
- Facilities management vendors.
- Supply chain partners for raw materials or components.
Key reasons to adopt TPRM
Here are key reasons why it's important for organizations to adopt a third-party risk management strategy:
- Risk mitigation. Businesses rely on vendors and external partners for essential services. If a third party experiences a data breach, financial failure or operational disruption, it can directly affect the outsourcing organization's business. TPRM helps identify and address these risks before they become a problem.
- Regulatory compliance. Many industries have regulations that require businesses to ensure their third-party vendors comply with security, privacy and ethical standards. A resilient TPRM framework helps companies adhere to these rules, and avoid legal penalties and maintain trust.
- Financial protection. Disruptions in the supply chain, cybersecurity incidents or unethical practices by third parties can result in financial losses. Proactive third-party risk management helps mitigate these financial risks and protects long-term profitability.
- Reputation management. A company's reputation is jeopardized if a third party mishandles sensitive data or engages in unethical behavior. Businesses that adopt TPRM practices are less likely to suffer reputational harm.
- Operational resilience. Companies that rely on third parties for essential functions, such as cloud services, logistics or customer support, must ensure business continuity. TPRM helps organizations build resilience against external disruptions in these functions and services.
- Quick recovery. Operational disruptions caused by third parties can lead to downtime and financial setbacks for organizations. However, a resilient TPRM program integrates contingency strategies that help businesses recover quickly from losses and downtime.
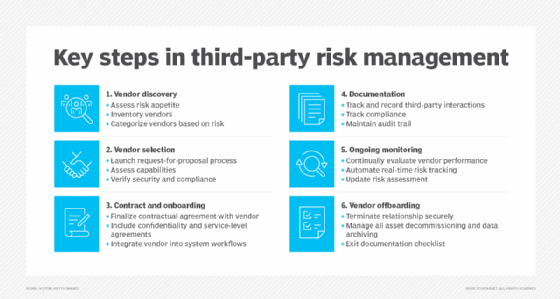
6 key steps to third-party risk management
The third-party risk management lifecycle consists of several stages that help organizations effectively assess, manage and mitigate risks associated with external vendors and partners. The six key steps involved in third-party risk management include the following:
- Vendor discovery. This initial stage involves defining the organization's risk appetite and identifying all third parties connected to the organization. It includes compiling a comprehensive inventory of vendors, suppliers and partners and categorizing them based on the level of inherent risk they present to the organization. By doing so, businesses create a structured approach to assessing and mitigating potential risks from external entities.
- Vendor selection. In this phase, organizations assess potential or existing third parties to ensure they meet the organization's needs. This process involves reviewing request-for-proposal responses and comparing vendor capabilities with business requirements. Critical factors include the vendor's reliability, alignment with operational objectives, and adherence to security and regulatory standards.
- Contract negotiation and onboarding. Once a vendor is selected, companies discuss contractual agreements that outline compliance requirements, security protocols and contingency plans to address possible risks. The outsourcing organization must ensure the contract incorporates confidentiality clauses, nondisclosure agreements, data protection commitments and service-level agreements. The onboarding process then integrates vendors into the organization's systems and workflows.
- Reporting and documentation. Organizations document all third-party interactions and risk management efforts, using TPRM software for structured, auditable recordkeeping that enhances reporting and compliance.
- Ongoing monitoring and compliance. Since risks evolve regularly, it's crucial for organizations to continuously monitor third-party vendors and their systems. This involves continuously evaluating their performance and compliance, using automated tools for real-time risk monitoring and updating risk assessments as new threats or changes emerge.
- Vendor offboarding. The final stage focuses on securely ending vendor relationships when they are no longer needed. Organizations must properly manage data and assets while keeping detailed offboarding records for compliance. A checklist helps ensure all critical steps are completed.
Common challenges in third-party risk management
Organizations face several challenges with TPRM. Some common obstacles include the following:
- Lack of visibility and data management. Managing vendor data is increasingly complex, with organizations struggling to collect, validate and maintain accurate information across multiple systems. Tracking fourth-party risks and relationships adds another layer of difficulty, as they often remain hidden despite their effect on risk exposure. Data silos, inconsistent formats and real-time updates also make it challenging to achieve a comprehensive vendor risk overview.
- Resource constraints. Organizations often face resource constraints in their TPRM programs, with limited staff managing expanding vendor portfolios. Budget restrictions hinder investments in technology and tools that could streamline processes, while the time-consuming nature of vendor assessments competes with other organizational priorities. As a result, businesses struggle to maintain a balance between thoroughness and efficiency, leading to reactive rather than proactive risk management.
- Technology integration complications. The technological landscape of TPRM presents major integration challenges, as legacy systems might not integrate smoothly with modern risk management tools. Automating assessments can run into compatibility issues, while poor system communication can hinder continuous monitoring. These gaps lead to data silos, the need for manual workarounds, and inefficiencies that drive up costs and risk exposure.
- Scalability challenges. As organizations grow and their vendor networks expand, scaling TPRM programs becomes increasingly challenging. Managing larger vendor populations while maintaining assessment quality requires significant resources and sophisticated processes. Organizations need to find the right balance between depth and breadth of assessments, often facing difficult decisions about resource allocation and risk prioritization.
- Vendor cooperation issues. Securing timely and meaningful vendor cooperation is a persistent challenge for organizations. Assessment responses are often delayed, incomplete or inaccurate, while some vendors resist adopting required security measures or disclosing information about their controls. Communication barriers, such as language differences and time zone challenges, can further complicate the process.
- Supply chains complexity. As organizations expand their supplier networks, TPRM becomes more challenging. A complex supply chain makes risk identification, assessment and mitigation harder. This makes it difficult to pinpoint the origin of threats. Suppliers across different regions and industries create compliance and oversight difficulties, emphasizing the need for strong monitoring strategies.
Best practices for an effective TPRM program
Adopting TPRM best practices is essential for businesses to protect themselves from various types of risk factors. The following are some of the most effective TPRM strategies:
- Establish goals and roles. An organization must establish risk management objectives, policies and procedures that align with its industry and regulatory landscape. It should define distinct roles and responsibilities across departments to ensure effective management of third-party risks.
- Get stakeholder buy-in. Executive leadership and stakeholders must be engaged early on when setting up the third-party risk management process. The stakeholders and leaders should actively support the program to maintain accountability. Organization's risk-management program should integrate input from all departments to promote collaboration and risk management.
- Use automation whenever possible. Organizations should adopt automated tools to streamline routine operations as they transform TPRM. Automation can expedite processes that traditionally demand substantial manual intervention. For example, automated systems handle repetitive tasks, such as vendor onboarding procedures, risk evaluation processes, and performance monitoring with increased speed and precision. By reducing manual intervention, organizations not only minimize the potential for human errors but also achieve greater operational efficiency.
- Extend risk management beyond cybersecurity. Organizations must address a broad spectrum of potential threats. For instance, an effective TPRM program considers reputational, geographical, geopolitical, strategic, financial, operational, ethical and environmental risks. By understanding and mitigating these diverse risks, businesses can enhance resilience and maintain operational stability.
- Classify third parties into risk tiers. Effective vendor risk management uses a tiered classification system based on risk exposure levels. This approach evaluates vendors based on their access to sensitive information, critical services and the potential for failure. By categorizing vendors according to risk levels, organizations can allocate resources and ensure comprehensive risk management across all third-party relationships.
Common TPRM job titles and responsibilities
Third-party risk governance requires collaboration throughout the organizational hierarchy, spanning from frontline teams that interact with vendors to executive leadership who set strategic direction and determine risk tolerance frameworks.
While TPRM roles vary across organizations, they generally fall into key categories based on responsibility levels. Common job titles and their responsibilities include the following:
Chief risk officer
A CRO is responsible for overseeing the organization's entire risk management strategy, including third-party risk. They ensure compliance with regulatory requirements and industry standards while providing strategic direction for vendor risk management programs. Their role is essential in maintaining a comprehensive and proactive risk framework that aligns with the organization's broader objectives.
Director of TPRM
This role is responsible for developing and introducing risk management frameworks to ensure effective oversight of vendor relationships. They lead risk assessments and mitigation strategies, proactively addressing potential vulnerabilities. They also collaborate closely with compliance and procurement teams to strengthen vendor governance and ensure adherence to regulatory and organizational standards.
Third-party risk manager
A third-party risk manager conducts risk assessments on vendors and subcontractors to identify potential vulnerabilities. They actively monitor vendor performance and ensure compliance with contractual obligations. They also collaborate with cybersecurity and legal teams to address vendor-related risks, strengthening third-party risk governance.
Vendor risk analyst
A vendor risk analyst evaluates vendor risk profiles and conducts due diligence to ensure secure and reliable partnerships. They assess financial, operational and cybersecurity risks associated with third-party vendors, identifying potential vulnerabilities that could affect the organization. They also support reporting and documentation efforts, providing insights into vendor risk findings as part of overall risk management strategies.
Compliance and risk specialist
This role ensures third-party vendors adhere to regulatory and compliance requirements. These specialists conduct audits and assessments to verify vendor compliance and identify gaps or risks. Compliance and risk specialists also collaborate with legal teams to identify and address contractual risk concerns. This helps safeguard against regulatory violations and liability issues.
Cybersecurity risk analyst
This analyst evaluates cybersecurity risks associated with third-party vendors, identifying potential vulnerabilities that could compromise organizational security. They monitor vendor security practices to ensure compliance with security frameworks and industry standards. They also collaborate with IT teams to proactively mitigate third-party cyberthreats, strengthening cybersecurity resilience across the vendor ecosystem.
Future TPRM trends
TPRM is evolving rapidly as businesses face increasing supply chain vulnerabilities, cybersecurity threats and regulatory scrutiny. Gartner reports that third-party networks are expanding in size and complexity, with 40% of compliance executives saying between 11% and 40% of their third-party relationships pose a high level of risk.
Some key trends shaping the future of TPRM include the following:
- AI-driven risk assessments. As third-party ecosystems grow more complex, AI-driven options are becoming essential for transforming risk management into a dynamic, data-driven strategy that quickly responds to emerging threats. AI plays a crucial role in automating risk assessments, detecting anomalies and predicting potential threats before they escalate. By analyzing large data sets in real time, AI enhances risk detection and decision-making.
- Stricter regulatory compliance. Governments and regulatory bodies are tightening TPRM requirements, particularly in areas such as data privacy, operational resilience, and environmental, social and governance (ESG). Businesses must enhance due diligence and compliance efforts to meet evolving standards.
- Integration of TPRM into enterprise culture. Third-party risk management is no longer confined to IT or compliance teams because organizations rely on a range of vendors and suppliers, each with unique risks. Instead, TPRM is becoming a shared responsibility across departments, including procurement, finance and operations.
- Continuous vendor monitoring. Traditional point-in-time risk assessments are becoming obsolete because they offer only a snapshot of a vendor's risk profile at a single moment, and fail to capture evolving threats and vulnerabilities. As cyber-risks, regulatory requirements and operational dependencies shift, organizations require continuous monitoring to detect security breaches, compliance lapses and financial instability in real-time. Organizations are shifting toward real-time vendor risk monitoring, using automated tools to track supplier performance, security postures and compliance adherence.
- Geopolitical risk considerations. Political instability and global crises are driving businesses to closely monitor third-party relationships. As a result, companies are reassessing vendor dependencies, especially in regions vulnerable to economic downturns or geopolitical risks. To maintain stability and compliance, organizations are conducting thorough evaluations of vendor locations, ownership structures, and regional risks, enabling them to anticipate challenges and mitigate disruptions while avoiding sanctions.
- Sustainability and ethical sourcing. Sustainability and ethical sourcing are becoming central to TPRM as organizations face increasing regulatory pressure and stakeholder expectations. Businesses must now evaluate vendors based on ESG, ensuring responsible sourcing, ethical labor practices and reduced carbon footprints.
Managing third-party risk in the cloud is crucial, as CSPs pose vulnerabilities within the supply chain. Explore key strategies to strengthen cloud security, ensure compliance and enhance organizational resilience.







