What is phishing? Understanding enterprise phishing threats
Phishing is a fraudulent practice in which an attacker masquerades as a reputable entity or person to trick users into revealing sensitive information. Attackers commonly use phishing emails or other forms of communication to distribute malicious links or attachments that can extract login credentials, account numbers and other personal information from victims. Deceptive phishing is a popular cybercrime, because it's easier to trick someone into clicking on a malicious link in a seemingly legitimate phishing email than to break through a computer's defenses. Learning more about phishing is important to help users detect and prevent it.
How does phishing work?
Phishing is a type of social engineering and cybersecurity attack where the attacker impersonates someone else via email or other electronic communication methods, including social networks and Short Message Service (SMS) text messages, to reveal sensitive information.
Phishers can use public sources of information, such as LinkedIn, Facebook, and X (formerly Twitter), to gather the victim's personal details, work history, interests and activities. These resources are often used to uncover information such as names, job titles and email addresses of potential victims. An attacker can then use the information to craft a believable phishing email.
Typically, a victim receives a message that appears to have been sent by a known contact or organization. The attack is then carried out either when the victim clicks on a malicious file attachment or clicks on a hyperlink connecting them to a malicious website. In either case, the attacker's objective is to install malware on the user's device or direct them to a fake website. Fake websites are set up to trick victims into divulging personal and financial information, such as passwords, account IDs or credit card details.
Although many phishing emails are poorly written and clearly fake, cybercriminals are using artificial intelligence (AI) tools such as chatbots to make phishing attacks look more real.

Other phishing attempts can be made via phone, where the attacker poses as an employee phishing for personal information. These messages can use an AI-generated voice of the victim's manager or other authority for the attacker to further deceive the victim.
How do phishing scams trick users?
Phishing scams primarily trick users through social engineering tactics, exploiting human psychology rather than technical vulnerabilities. They often create a sense of urgency, fear, curiosity or a desire for gain. Common tactics include the following:
- Impersonation. Attackers pretend to be trusted entities, such as banks, government agencies or colleagues. They use fake logos, similar-looking domain names and familiar language to appear authentic.
- Urgency. The message often creates a sense of urgency or warns of an immediate problem, prompting the victim to act quickly to avoid negative consequences. For example, a phishing message might claim, "Your account has been compromised," "Your payment is overdue," or "Suspicious activity detected."
- Curiosity. The subject lines or content are designed to pique curiosity, leading users to click on malicious links or attachments.
- Fear. The phishing message can also include threats, such as account suspension notices or reports of unauthorized activity, to induce panic and prompt immediate action.
Why do hackers send phishing scams?
Cybercriminals deploy phishing attacks for various malicious purposes, including the following:
- Financial gain. One of the primary motives behind phishing scams is financial gain, often through stealing credit card details, bank account information or initiating fraudulent transactions.
- Identity theft. Attackers carry out phishing scams to steal personal data such as Social Security numbers and addresses to commit fraud or open unauthorized accounts.
- Malware distribution. Attackers use phishing scams to carry out data breaches or system compromises by installing malware or ransomware to infiltrate networks.
- Credential harvesting. Phishing is commonly used to collect usernames and passwords to gain unauthorized access to secure systems or services. Credential harvesting typically happens when victims click on a malicious link that leads them to a fake login page. When the victim enters their login credentials, attackers capture the information and use it to gain access to systems or accounts.
- Ransomware. Email scammers deceive individuals into downloading malware and installing software that lets attackers access and lock their files. The hackers then demand payment as ransom in exchange for unlocking the data.
- Launching further attacks. Attackers sometimes use compromised accounts or systems as a launching pad for more sophisticated attacks against other individuals or organizations.
Who are the targets of phishing?
While phishing attacks can target anyone, certain groups are more frequently targeted, such as the following:
- Individuals. Phishers target a broad range of internet users, particularly those less familiar with cybersecurity practices. Anyone with an email address, phone number or social media account can be vulnerable to indiscriminate phishing campaigns, which often involve fake lottery winnings, deceptive bank alerts or fraudulent account notifications.
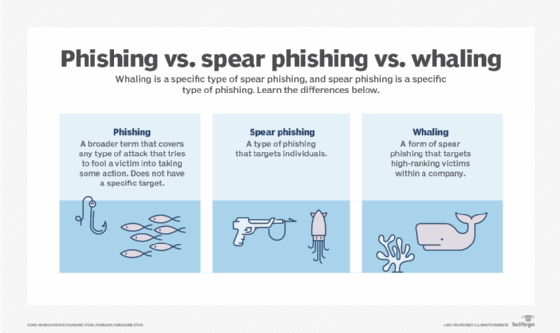
- Employees. Businesses are frequently targeted, with attackers aiming to gain access to corporate networks, financial systems or confidential information. This often involves spear phishing and whaling attacks.
- High-value individuals. Executives, celebrities or government individuals with access to financial resources or sensitive information are often the focus of customized and sophisticated phishing attempts.
- Customers of specific services. Users of popular online services, banks, e-commerce sites or social media platforms are common targets, as attackers impersonate these services to steal credentials.
- Elderly individuals. Older adults might be more vulnerable to phishing attacks if they have limited technological experience, as seen in cases where scammers impersonate acquaintances to solicit funds for a made-up crisis.
Why are phishing attacks so effective?
Several factors contribute to the high success rate of phishing attacks, such as the following:
- Lack of awareness. Many individuals and organizations lack proper training to recognize phishing attempts, making them more susceptible.
- Advanced techniques. Phishing techniques are constantly evolving. Scammers use increasingly convincing fake websites, legitimate-looking email templates and even real company branding. Also, spear phishing and whaling attacks are highly personalized, making them harder to detect.
- Volume and automation. Attackers can launch millions of phishing emails or messages with ease, relying on a small percentage of victims to make the effort worthwhile.
- Emotional manipulation. Attackers exploit human tendencies such as curiosity, fear, urgency, trust and the desire for quick gains. Even tech-savvy individuals can fall victim when distracted or under pressure.
- Weak security practices. Inadequate security measures, such as poor security and password hygiene and outdated software, provide easier entry points for attackers.
- Mobile device usage. On mobile devices, it can be harder to inspect email headers, full URLs or sender details, making it easy to miss red flags.
- Credential reuse. If a user falls for a phishing scam and reuses the same password across multiple accounts, the attacker gains access to several services.
How to recognize a phishing attack email
Successful phishing messages are difficult to distinguish from real messages. Usually, they're represented as being from a well-known company, and include corporate logos and other identifying data. However, several clues can indicate a message is a phishing attempt:
- The message often uses generic salutations such as "Dear Customer" or "Dear User" instead of addressing a person by their name.
- The message uses subdomains, misspelled URLs -- also known as typosquatting -- or otherwise suspicious URLs.
- The recipient uses a Gmail or other public email address rather than a corporate email address.
- The message is written to invoke fear or a sense of urgency.
- The message includes a request to verify personal information, such as financial details or a password.
- The message is poorly written and has spelling or grammatical errors.
The message comes with suspicious links that can be checked by hovering over the link without clicking on it to see the actual URL. If the link doesn't match the legitimate website's address or uses a suspicious domain, it's likely a phishing attempt.
The message or email often promises unbelievable offers, such as winning a prize or receiving a large sum of money, to entice users into clicking on links or providing personal information.
What are the different types of phishing attacks?
Cybercriminals continue to hone their existing phishing skills and create new types of phishing scams. Common types of phishing attacks include the following:
- Spear phishing attacks. They are directed at specific individuals or companies. Attackers usually use information about the victim to more successfully represent the message as being authentic. Spear phishing emails use the victim's name, location and other personal information. They might include references to co-workers and executives at the victim's organization.
- Whaling attacks. This is a type of spear phishing attack that targets senior executives within an organization with the objective of stealing large sums of money or sensitive data. Attackers research their victims in detail to create a more genuine message. Because a typical whaling attack targets an employee who can authorize payments, the phishing message often appears to be a command from an executive to authorize a large payment to a vendor when, in fact, the payment would be made to the attackers.
- Pharming. This is a type of phishing attack that uses domain name system cache poisoning to redirect users from a legitimate website to a fraudulent one. Pharming attempts to trick users into logging in to the fake website using their personal credentials.
- Clone phishing attacks. Attackers use previously delivered but legitimate emails that contain either a link or an attachment. They make a copy -- or clone -- of the legitimate email and replace links or attached files with malicious ones. Victims are tricked into clicking on the malicious link or opening the malicious attachment. Attackers often use this technique after they've taken control of another victim's system. In this case, the attackers use their control of one system in an organization to email messages from a trusted sender who is known to the victims.
- Evil twin attacks. These phishing attacks occur when hackers try to trick users into connecting to a fake Wi-Fi network that looks like a legitimate access point. The attackers create a duplicate hotspot that sends out its own radio signal and uses the same name as the real network. When the victim connects to the evil twin network, attackers gain access to all transmissions to or from the victim's devices, including user IDs and passwords. Attackers can also use this vector to target victim devices with their own fraudulent prompts.
- Voice phishing. This is a form of phishing that occurs over voice-based media, including voice over IP, which is also called vishing, or plain old telephone service. This type of scam uses speech synthesis software to leave voicemails notifying the victim of suspicious activity in a bank account or credit account. The call solicits the victim to respond to verify their identity, thus compromising their account credentials.
- SMS phishing. Also called smishing, this is a mobile device-oriented phishing attack that uses text messaging to convince victims to disclose account credentials or install malware. The victim is usually asked to click on a link, call a phone number or send an email. The attacker then asks the victim to provide private data. This attack is more difficult to identify, as attached links can be shortened on mobile devices.
- Calendar phishing. Attackers attempt to fool victims by sending false calendar invites that can be added to calendars automatically. This type of phishing attack attempts to appear as a common event request and includes a malicious link.
- Page hijack attacks. Page hijacking occurs when the victim is redirected to a compromised website that's the duplicate of the page they intended to visit. The attacker uses a cross-site scripting attack to insert malware on the duplicate website and redirects the victim to that site.
- Angler phishing. This attack is carried out by cybercriminals creating fake customer service accounts on social media platforms. They monitor for users seeking assistance and then impersonate the company to steal login credentials or distribute malware.
- Watering hole phishing. This is a type of phishing where attackers identify websites frequently visited by a specific group and infect them with malware. When members of the targeted group visit the compromised site, their devices become infected, leading to potential data breaches.
Phishing techniques
Phishing attacks depend on more than simply sending an email to victims and hoping they click on a malicious link or open a malicious attachment. Attackers can use the following techniques to entrap their victims:
- URL spoofing. Attackers use JavaScript to place a picture of a legitimate URL over a browser's address bar. Normally, when a user hovers their mouse over an embedded link on a webpage, the browser's status bar displays the actual URL the link points to. This is often recommended as a basic method for verifying the legitimacy of a link before clicking. However, hovering isn't always a reliable way to detect an attack because a sophisticated attacker using JavaScript to spoof the visible URL in the address bar can also manipulate the URL that appears on hover.
- Link manipulation. Often referred to as URL hiding, this technique is used in many common types of phishing. Attackers create a malicious URL that's displayed as if it were linking to a legitimate site or webpage, but the actual link points to a malicious web resource.
- Link shortening. Attackers can use link shortening services, such as Bitly, to hide the link destination. Victims have no way of knowing if the shortened URL points to a legitimate website or to a malicious website.
- Homograph spoofing. This type of spoofing attack depends on URLs that were created using different characters to read exactly like a trusted domain name. For example, attackers can register domains that use slightly different character sets that are close enough to established, well-known domains.
- Graphical rendering. Rendering all or part of a message as a graphical image sometimes lets attackers bypass phishing defenses. Some security software products scan emails for particular phrases or terms common in phishing emails. Rendering the message as an image bypasses this.
- Covert redirect. Attackers trick victims into providing personal information by redirecting them to a supposed trusted source that asks them for authorization to connect to another website. The redirected URL is an intermediate, malicious page that solicits authentication information from the victim. This happens before forwarding the victim's browser to the legitimate site.
- Chatbots. Attackers use AI-enabled chatbots to remove obvious grammatical and spelling errors that commonly appear in phishing emails. Phishing emails using an AI chatbot might make the phishing message sound more complex and real, making it harder to detect.
- AI voice generators. Attackers use AI voice generator tools to sound like a personal authority or family figure over a phone call. This further personalizes the phishing attempt, increasing its likeliness to work. Attackers just need a voice sample using a small audio clip of the victim's manager or family member.
- Bait creation. Attackers send messages, usually emails, that look authentic and reliable. They achieve this by impersonating familiar entities such as popular companies, government bodies or other organizations to trick recipients.
- Tabnabbing. This is a technique where an inactive tab in a web browser redirects to a fake login page without the user's explicit action, hoping the user will enter credentials without noticing the change.
How to prevent phishing
To help prevent phishing messages from reaching end users, experts recommend layering security controls with the following tools:
- Antivirus software.
- Desktop and network firewalls.
- Antispyware software.
- Antiphishing toolbar installed in web browsers.
- Gateway email filter.
- Web security gateway.
- Spam filter.
- Phishing filters from vendors such as Microsoft.
Preventing phishing requires a combination of awareness, security measures and vigilance. Some key strategies that individuals and enterprises can adopt to protect against phishing attacks include the following:
Enterprise email security
Enterprise mail servers should use at least one email authentication standard for email security to verify inbound emails. This can include the DomainKeys Identified Mail protocol, which lets users block all messages except for those that have been cryptographically signed.
The Domain-based Message Authentication, Reporting and Conformance protocol is another example. DMARC provides a framework for using protocols to block unsolicited emails more effectively.
Sender and link verification
Email users should verify the sender's email address carefully. For example, they should look for misspellings, unusual domain names or discrepancies between the display name and the actual email address. This is especially important if the message requests personal information or urges immediate action.
Before clicking on any links, users should hover over them to preview the destination URL. Caution should be exercised with shortened links or URLs containing subtle misspellings, as these are common phishing tactics. Adopting these practices can help individuals avoid falling victim to fraudulent emails.
Online resources
There are several resources on the internet that provide help to combat phishing. The Anti-Phishing Working Group website and the Federal Trade Commission's Online Privacy and Security web page both provide advice on how to spot, avoid and report phishing attacks.
Interactive security awareness training aids, such as Cofense's PhishMe and Proofpoint Security Awareness Training, can help teach employees how to avoid phishing traps. In addition, sites like FraudWatch International and MillerSmiles.co.uk publish the latest phishing email subject lines that are circulating on the internet.
Employee training
Employees should be educated on phishing techniques and how to identify them. They should also be cautioned to avoid clicking on links and attachments or opening suspicious emails from someone they don't know. Recognizing the signs of phishing can significantly reduce the risk of falling victim.
Strong authentication and passwords
Users should create complex and unique passwords for each of their online accounts. Using a reputable password manager is also recommended to generate and securely store these passwords.
At the organizational level, companies should enforce and enable multifactor authentication wherever possible. MFA adds an extra layer of protection by requiring a second form of verification, such as a one-time code or fingerprint in addition to a password, making it significantly harder for attackers to gain access, even if credentials are compromised.
Phishing simulations
Organizations should conduct simulated phishing campaigns to train employees in recognizing phishing attempts. This typically occurs when an employee unknowingly receives an email that resembles an external phishing attempt, but in reality, is an internal email sent from the company's cybersecurity team.
However, phishing simulations have limitations, as they can't teach users to detect every phishing attempt and might hinder productivity if overemphasized. While not a foolproof method, this hands-on approach can still help identify vulnerabilities and reinforce learning.
Endpoint and network security
Organizations should deploy endpoint detection and response options to identify and respond to malicious activity on user devices. Additionally, using web and domain name system filtering can help block access to known malicious websites even if an employee inadvertently clicks a phishing link.
To further strengthen network security, intrusion detection and intrusion prevention systems should be used to monitor traffic for suspicious patterns and respond to potential threats in real time.
Access controls
Enforcing strong access controls and adhering to the principle of least privilege are critical defenses against phishing attacks. By ensuring that employees only have access to the systems and data necessary for their specific roles, organizations can limit the potential damage if an attacker gains access through compromised credentials.
This approach minimizes the attack surface, reduces lateral movement within the network and helps contain breaches to a limited scope.
Maintain regular data backups
Users should keep their operating system, browsers and antivirus software up to date to protect against known vulnerabilities that attackers might exploit. At the enterprise level, organizations should ensure that critical data is backed up regularly. In the event of a successful phishing attack, having up-to-date backups can prevent data loss and reduce downtime.
Examples of phishing scams
Phishing scams come in all shapes and sizes. Knowing about some of the ways scammers have been phishing helps users stay safe, alert and prepared. Some examples of recent phishing attacks include the following:
Digital payment-based scams
These scams occur when major payment applications and websites are used as a ruse to gain sensitive information from phishing victims. In this scam, a phisher masquerades as an online payment service, such as PayPal, Venmo or Wise.
Generally, these attacks are performed through email, where a fake message purporting to come from a trusted payment service asks the user to verify login details and other identifying information. Usually, the attacker claims this information is necessary to resolve an issue with the user's account. Often, these phishing attempts include a link to a fraudulent spoof page.
PayPal is aware of these threats and has released informational materials for its users to reference to stay prepared against phishing attacks. If a user is unsure of how to spot a fraudulent online payment phishing email, there are a few details to look out for. Generally, a phishing email imitating PayPal has been known to include the following:
- They might start with dodgy greeting that doesn't include the victim's name. Official emails from PayPal always address sellers by their name or business title. Phishing attempts in this sector tend to begin with Dear user or use an email address.
- In the case of PayPal and other online payment services, some of these scams alert their potential victims that their accounts will soon be suspended. Others claim that users were accidentally overpaid, and they need to send money back to a fake account.
- PayPal doesn't send its users downloadable attachments. If a user receives an email from PayPal or a similar service that includes an attachment, they shouldn't download it.
If a seller receives one of these emails, they should open their payment page in a separate browser tab or window to see if their account has any alerts. If a seller has been overpaid or is facing suspension, it will say so there. Additionally, PayPal urges users to report any suspicious activity so it can monitor these attempts and prevent its users from getting scammed.
Finance-based phishing attacks
These attacks operate on the assumption that victims will panic and give the scammer personal information. Usually, in these cases, the scammer poses as a bank or other financial institution. In an email or phone call, the scammer informs their potential victim that their security has been compromised. Often, scammers use the threat of identity theft to successfully do just that.
Examples of this scam include the following:
- Suspicious emails about money transfers are designed to confuse the victim. In these phishing attempts, the potential victim receives an email that contains a receipt or rejection email regarding an electronic fund transfer. Often, the victim instantly assumes fraudulent charges have been made to their account and clicks on a malicious link in the message. This leaves their personal data vulnerable to being mined.
- Direct deposit scams are often used on new employees of a company or business. In these scams, the victim is notified that their login information isn't working. Anxious about not getting paid, the victim clicks on a link in the email. This sends them to a spoof website that installs malware on their system. At this point, their banking information is vulnerable to harvesting, leading to fraudulent charges.
Work-related phishing scams
These are especially alarming, as this type of scam can be personalized and hard to spot. In these cases, an attacker purporting to be the recipient's boss, chief executive officer (CEO) or chief financial officer (CFO) contacts the victim and requests a wire transfer or a fake purchase.
One work-related scam that has been popping up around businesses in the last couple of years is a ploy to harvest passwords. This scam targets executive-level employees since they likely aren't considering that an email from their boss could be a scam. The fraudulent email often works because, instead of being alarmist, it simply talks about regular workplace subjects. Usually, it informs the victim that a scheduled meeting needs to be changed. The employee is asked to fill out a poll about when a good time to reschedule would be via a link. That link then brings the victim to a spoof login page for Microsoft Office 365 or Microsoft Outlook. Once the employee enters their login information, the scammers steal their password.
Malicious actors also pose as a manager, CEO or CFO over the phone by using an AI voice generator and then demand a fraudulent transfer of money. While the employee thinks they're making a business transaction, they're actually sending funds to the attacker.
Social media and messaging scams
In these attacks, scammers exploit social media and messaging platforms through impersonation and deception. Fake account verification scams trick users into entering login details on phishing sites by claiming their profiles are at risk. Fraudsters also impersonate influencers or celebrities to lure victims into financial schemes.
On messaging apps such as WhatsApp, attackers use smishing or fraudulent texts impersonating banks or delivery services to direct users to malicious links that steal personal information. These scams take advantage of trust and urgency, making social media and messaging platforms a prime target for cybercriminals.
History of phishing
The history of the term phishing isn't entirely clear. One common explanation for the term is that phishing is a homophone of fishing. And it's named so because phishing scams use lures to catch unsuspecting victims, or fish.
Another explanation for the origin of phishing comes from a string of characters -- <>< -- that was often seen in AOL chat logs. Those characters were a common Hypertext Markup Language tag found in chat transcripts. Because it occurred so frequently in those logs, AOL admins couldn't productively search for it as a marker of potentially improper activity. Hackers would replace any reference to illegal activity -- including credit card information or account credentials theft -- with the string.
In the early 1990s, a group of individuals called the Warez Group created an algorithm that would generate credit card numbers. The numbers were created at random in an attempt to create fake AOL accounts that would spam other accounts. Some hackers tried to change their screen names to appear as AOL administrators. Using these screen names, they would then phish people via AOL Instant Messenger for their information.
In the early 2000s, phishing saw more changes in implementation. The Love Bug of 2000 is an example of this. Potential victims were sent an email with a message saying "ILOVEYOU," pointing to an attachment letter. That attachment contained a worm that would overwrite files on the victim's computer and copy itself to the user's contact list.
Also, in the early 2000s, different phishers began to register phishing websites. A phishing website is a domain similar in name and appearance to an official website. They're made to fool someone into believing the site is legitimate.
In 2013, a Lithuanian man named Evaldas Rimasauskas impersonated a legitimate Taiwanese hardware supplier called Quanta Computer. He created fake email accounts, invoices and company documents that closely mirrored the real suppliers. Over two years, he sent fraudulent payment requests to Facebook and Google employees, who unknowingly wired over $100 million to bank accounts Rimasauskas controlled.
In 2014, the infamous Sony Pictures cyberattack began with a spear phishing campaign where attackers sent emails to specific Sony employees. The messages looked legitimate but were designed to trick the victims into clicking malicious code or links or giving up their login credentials. Once the attackers gained access, they moved laterally through the network, stealing massive amounts of data.
Today, phishing schemes are varied and potentially more dangerous than before. With the integration of social media and login methods, such as Facebook Login, an attacker could potentially commit several data breaches on a victim using one phished password, making them vulnerable to ransomware attacks in the process.
More modern technologies are also being used. For example, in 2019, the CEO of an energy firm in the U.K. thought they were speaking on the phone with their boss. They were told to send funds to a specific supplier when in actuality it was a phishing scheme that used AI to mimic the voice of the chief executive.
In 2020, a hacker and accomplices undertook a spear phishing attack, creating a website that looked like Twitter's internal virtual network provider. The attackers impersonated help desk staff, calling Twitter employees and asking them to submit their credentials. Using those credentials, the attackers gained access to various high-profile accounts, such as those of Barack Obama, Elon Musk and Joe Biden.
In December 2024, organized criminals exploited phishing tactics to access approximately 100,000 U.K. taxpayer accounts, resulting in a £47 million theft from HM Revenue & Customs. The attackers used stolen identity data to impersonate taxpayers and redirect funds. While no individual taxpayers suffered financial loss, the breach highlighted vulnerabilities in identity verification processes.
Cybercriminals are increasingly using AI tools such as ChatGPT in sophisticated phishing scams. Learn how AI is making these attacks more dangerous and harder to detect and explore the role that cybersecurity teams should play in responding effectively to these attacks.







