vector
What is a vector?
A vector is a quantity or phenomenon that has two independent properties: magnitude and direction. The term also denotes the mathematical or geometrical representation of such a quantity.
Examples of vectors in nature are velocity, momentum, force, electromagnetic fields and weight. A quantity or phenomenon that exhibits magnitude only, with no specific direction, is called a scalar. Examples of scalars include speed, mass, electrical resistance and hard drive storage capacity.
What are vector attributes?
Vectors are typically represented by an arrow with a beginning, or tail, and an end, or head, that is usually represented by an arrowhead. Vectors delineate the movement from point A to point B and can be defined as an entity with a designation, such as vector a.
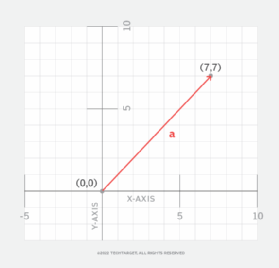
In mathematics, the Cartesian coordinate system depicts vectors using a number pair as shown in Figure 1. In this example, the vector is a directed line segment defined as (0,0), (7,7) using its numbered pairs. Vectors and scalars can be used in mathematical processes and vector operations, such as vector addition, vector subtraction and vector multiplication.
Vectors in computer graphics
Vectors can be depicted graphically in two or three dimensions. The magnitude of the vector is shown as the length of a line segment. The direction of the vector is shown by the orientation of the line segment and by an arrowhead at one end.
When creating images in vector graphics, the graphics file is a sequence of vector statements describing a series of points that connect to form the image. Examples of vector graphics software include Adobe Illustrator and CorelDraw.
Benefits of vector graphics
Vector graphics are used for many types of graphic images. This technology has gained popularity among graphic illustrators for the following reasons:
- Flexibility and scalability. A designer can size an image in virtually any orientation and locate it anywhere on the screen.
- Application and website development. Application and website developers like vector graphics because of scalability and the ability to create images on a variety of devices.
- Animation. Vector graphics facilitates movement of images via animation.
- Engineering design systems. Computer-aided design applications use vector graphics because of scalability and the ability to easily work with complex mathematical, scientific and engineering formulas.
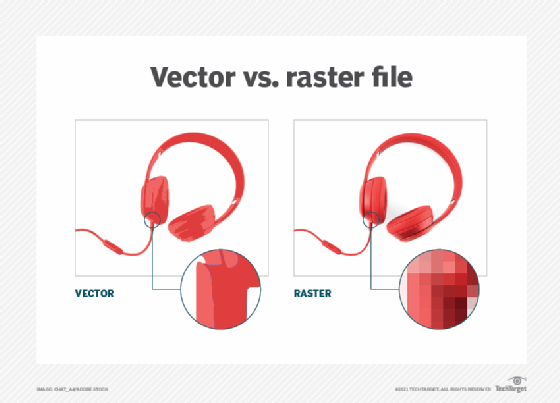
Vector vs. raster graphics
Raster graphics map individual bits -- each of which has its own qualities, such as color -- into an image via components called pixels, or picture elements. Raster images typically have a fixed number of pixels and are less scalable than vector images. As an image gets larger, individual pixels can become visible, resulting in the image being not as sharp or high quality as an equivalent vector image.
With raster images, computers must store each pixel, rather than a series of vector points. This often results in raster files being larger than vector graphics files. Adobe Illustrator and Adobe Photoshop are examples of software that is used to convert raster images into vector graphics files and vice versa.
Vectors in cybersecurity
In cybersecurity, the pathway that a threat actor or hacker uses to deliver their payload, such as a virus or ransomware, to a system or network is called an attack vector. This is how hackers exploit vulnerabilities in a system or network.
An attack vector can also be human, in the case of social engineering, where the perpetrator uses clever communication techniques to mislead users into giving out valuable information such as passwords. Typical attack vectors include malware, email attachments, instant messages and pop-up windows.
Cyber threat detection and mitigation systems include firewalls, intrusion detection systems, intrusion prevention systems and antivirus software. Numerous products and services are available to prevent threat actors from using attack vectors and to address threats.
Learn about the top ransomware attack vectors and how to avoid them.
