subnet mask
What is a subnet mask?
A subnet mask is a 32-bit binary number used in modern network addressing schemes to differentiate between a network's location and the specific location of a host or device on that network. A subnet mask is one part of a network address and is always used with an Internet Protocol address (IP address) to determine the precise destination for each network packet.
Subnetting is a vital concept in modern networking. Networks can be large and complex constructs. Pinging every packet to every device on a large modern network for the IP address can congest the network and impair network performance.
Network performance can be improved by creating subnetworks -- or subnets -- which are logical separations that use network routers to break the overall physical network into two or more logical smaller networks.
The term mask is used because the subnet mask is not part of a network address -- the IP address is. Instead, the binary digits used in a subnet mask perform a logical operation with the IP address to determine the correct subnet to direct a packet. Network traffic routed to one network subnet will not be duplicated to other subnets, reducing unneeded bandwidth use.
Proper network architecture and the use of subnets allow an enterprise to build more organized, efficient and better-performing networks.
IP address vs. subnet mask
Getting a network packet to a specific host destination requires two pieces of information: the IP address and subnet mask.
IP address
An IP address uniquely identifies every device on a network. A traditional IPv4 address class uses 32 binary bits and can identify more than four billion unique combinations. By comparison, current IPv6 addressing uses 128 binary bits, but IPv4 remains popular and is easier to understand.
IPv4 IP addresses are denoted as four sets of eight bits -- four octets -- with each octet ranging from 0 to 255 (corresponding to binary representations ranging from 00000000 to 11111111). A typical IP address found in a home network might be shown as 192.168.1.0. This is referred to as dotted decimal which is far easier for humans to read. IPv6 addressing uses a more sophisticated series of hexadecimal numbers separated by a colon such as 3FFE:23A7:00.
However, IP addressing has a few issues. The entire bit sequence is not used to refer to the specific device outright. Instead, every IP address is broken into two parts -- the network address and the host address. In most simple networks, the first three octets form the network address, and the last octet is the actual host device designation. For example, an IP address such as 192.168.30.110, the network address is 192.168.30, and the actual host or device address is .110.
Subnet mask
The subnet mask says, "Does this packet belong on this part of the network or not?" The IPv4 subnet mask accomplishes this job by adding a second 32-bit set of dotted decimal information. Each bit of the mask is logically ANDed to the digits of the IP address. Thus, a typical IPv4 subnet mask is designated 255.255.255.0. When the two octets are lined up, it's easier to see their relationship such as:
192.168.30.110 11000000.10101000.00011110.01101110 IPv4 address
255.255.255.0 11111111.11111111.11111111.00000000 Subnet mask
-------------------------------------------------------
192.168.30.0 11000000.10101000.00011110.00000000 Network address
So, when the subnet mask is applied to the IP address, the mask separates the network address from the host address, allowing a router to quickly determine where (which subnet) to forward the packet. If the router is the correct subnet, the packet is passed to that subnet where the intended host is deployed. If not, the router will use its routing tables to forward the packet to the correct router and subnet.
IP class vs. subnet mask
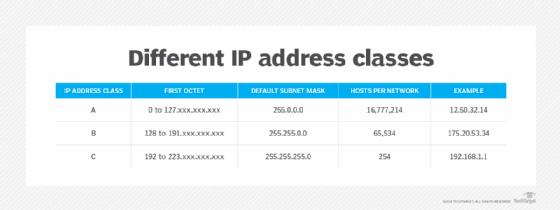
Network IP addressing is broken down into a series of broad-size ranges called classes. Each class uses a distinct range of IP addresses, along with a distinctive subnet mask. There are five standard IP address classes labeled A through E:
- Class A networks use an IP address with 0 to 127 as the first octet, and a default subnet mask of 255.0.0.0. These are typically some of the largest networks because the subnet mask allows for three octets worth of host addresses (and only one octet of network address).
- Class B networks use an IP address with 128 to 191 as the first octet, and a default subnet mask of 255.255.0.0. This allows midsize networks with two octets of the subnet mask to be available to handle host addresses (and two octets of network addresses).
- Class C networks use an IP address with 192 to 223 as the first octet, and a default subnet mask of 255.255.255.0. These are typically some of the smallest networks because only one octet of the subnet mask is available to handle host addressing (with three octets for the network address). Most small home or office networks use Class C addressing.
- Class D networks are typically reserved for multicasting.
- Class E networks are typically reserved for use by the Internet Engineering Task Force.
CIDR and subnets
The traditional IP address classes, ranges and subnet masking system is called classful addressing, which relies on fixed ranges for network and host addresses.
While classful addressing is relatively straightforward, it can also be inefficient. For example, a Class C network can only support 254 host devices, and a Class B network can support over 65 thousand hosts. If a business needed more than 254 devices on a subnet, a different address class would be needed -- but the next class up would likely add and waste a tremendous number of addresses.
Networking technology now supports a classless addressing scheme called Classless Inter-Domain Routing (CIDR). CIDR allows network administrators to divide an IP address space into subnets of varying sizes rather than fixed subnet sizes. The technique uses variable-length subnet masking to set the desired ratio between the number of network address bits and the number of host address bits.
IPv4 CIDR addresses are designated with an IP address followed by a slash and the number of bits allocated to the network address.
For example, an IPv4 CIDR address such as 192.168.1.1/24 says that the first 24 bits of the IP address represent the network address and the remaining bits are for the host address. This example is identical to the traditional Class C network scheme.
However, an IPv4 CIDR address such as 192.168.1.1/22 would allocate the first 22 bits of the IP address as the network address, leaving the last 10 bits as the host address. In this example, 10 bits as the host address would allow 2^10 or 1,022 hosts per network address. This means there would be fewer networks, but more hosts per network -- but administrators can set ratios far more flexibly than traditional classful addressing.
CIDR also supports IPv6 addressing, appending a slash and bit number to the end of the IPv6 address to stipulate the number of bits allocated for the network address. For example, an IPv6 IP address with a /32 at the end would mean that the first 32 bits of the address would be the network address, and the remaining bits would comprise the host address.
As Internet addressing becomes more congested and challenging, CIDR addressing provides a way to optimize the use of finite network and host addressing space for internet service providers, businesses and private home users.
Benefits of subnetting
The use of subnets in network addressing provides several compelling advantages including:
- Organization. Subnets are a core part of network organization, enabling businesses to design and build networks that align closely with their operational requirements and make efficient use of IP address space. For example, a business with multiple locations might benefit from a design that isolates the whole business network into a subnet for each location. Similarly, a large enterprise might create a subnet for each major department or division.
- Security. Subnets isolate network traffic by ensuring that only traffic intended for one set of hosts does not repeat or broadcast to all hosts throughout the entire network. This reduces the attack potential for eavesdropping and other forms of disrupting, seeing or stealing valuable network traffic. Not only does an attacker need access to the right network, but they also need to be on the right subnet. Think about a thief who not only needs to be in the right building but also needs to be in the right room.
- Performance. TCP/IP networks operate through contention -- looking for free time on the network wire to transmit traffic packets. Subnets effectively reduce the size of a logical network which limits the number of devices that can use the subnet at any one time. This lowers congestion on each subnet and allows more efficient use of network resources to improve overall performance.
Subnet mask calculators
Subnetting is a vital part of network design and configuration. Selecting the proper subnet mask to establish desired network characteristics can be challenging -- especially when using current CIDR designations with larger and more complex IPv6 addresses. A great deal of network troubleshooting can be attributed to poor or erroneous subnet configurations.
Network architects and administrators can utilize a wide variety of readily available subnet mask calculators capable of assisting with aspects of subnet planning, including the following:
- Convert between IPv4 and IPv6 addresses.
- Determine the number of host addresses available for a given subnet.
- Determine the number of network addresses available for a given subnet.
- Convert from dotted decimal to hexadecimal.
Examples of subnet mask tools include (but are not limited to) the following:
It's important to consider the strengths and intended purposes of each calculator and find the tool that best suits specific needs. It's also a good practice to cross-check results between calculators to avoid unintended errors in tool results.
Key takeaways
Subnets are a means of organizing a modern TCP/IP network which can benefit efficient network performance and security.
- An IP address represents both a network address and a host address.
- A subnet mask separates the network address from the host address.
- Modern classless CIDR addressing uses flexible subnetting -- replacing older classful addressing schemes -- in both IPv4 and IPv6 networks.
- Many subnet mask calculators can assist with network design and subnet planning.
