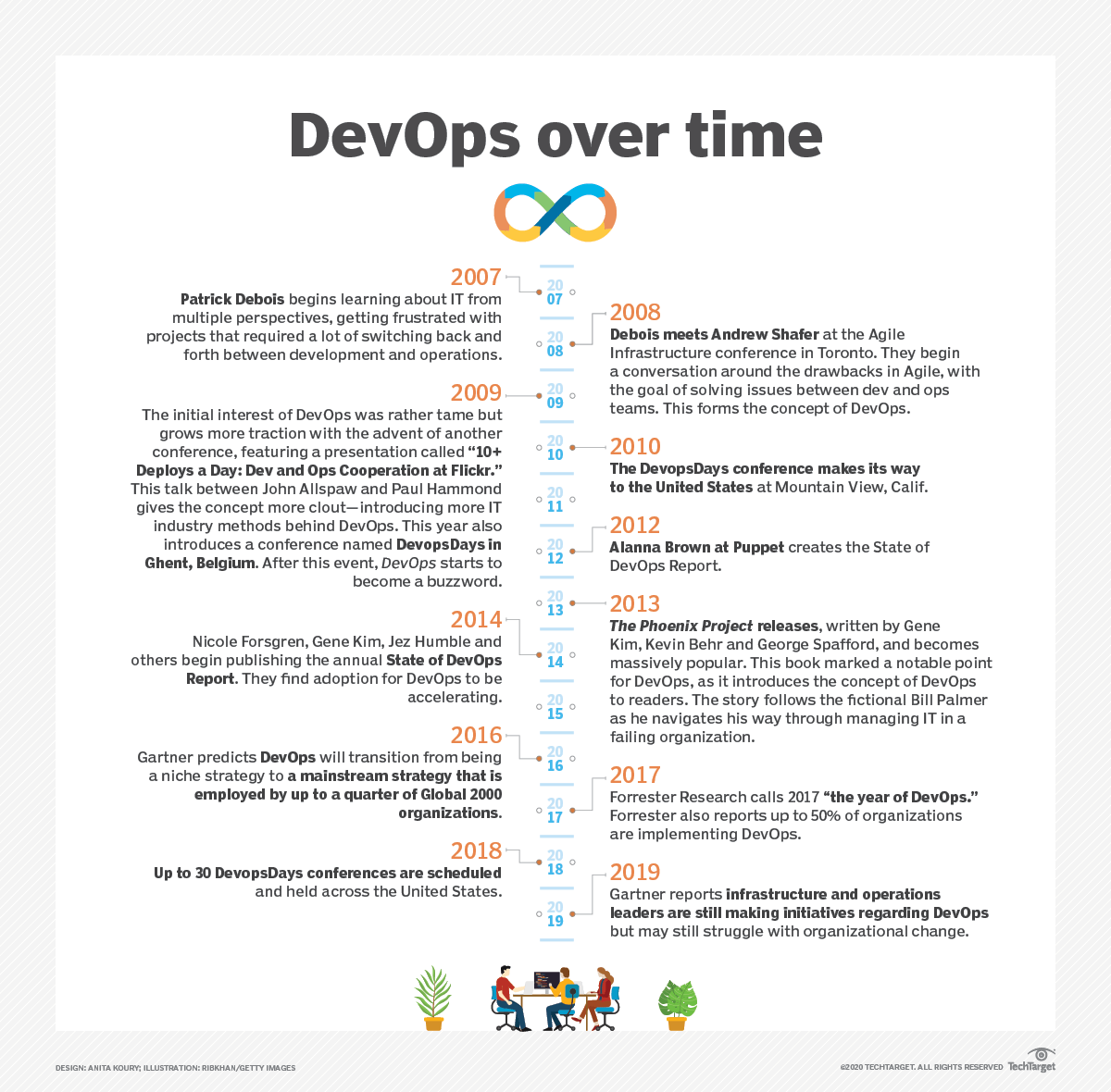
The history of DevOps: A visual timeline
DevOps is a shared philosophy in which development and operations teams work together. The practice promotes better communication and collaboration between those two teams, as well as other teams in an organization, such as security.
DevOps' rise in popularity grew with the publication of books like The Phoenix Project by authors Gene Kim, George Spafford and Kevin Behr. Published in 2013, the book is a narrative-style novel that follows a fictional American company going through a digital transformation. Below is a timeline of the history of DevOps and major moments that have helped develop the concept.
DevOps has grown since its initial conception in 2007-2008, and now large companies such as Amazon, Netflix, Target and Adobe are embracing the idea. In 2014, 16% of organizations participated in DevOps, growing little by little over the years to 27% in 2018.
With the growth of DevOps, vendors have begun to offer services aligned with the concept. Vendors in 2020 include Atlassian, CloudBees, GitHub, HashiCorp and Google.
Here's a timeline that shows the evolution of DevOps through the years. Click on the image to view it at full-size.