What is brain hacking?
Brain hacking, or neurohacking, is the application of techniques or technologies to affect an individual's mental state, cognitive processes or level of function. Such efforts can be intentionally applied by the individual as a tool for personal development or by another person in an attempt to induce a behavior in that individual.
Brain hacking yourself
Some uses of the term brain hacking tend to be positive in nature. In this context, a brain hacker is someone who uses available resources in a novel way to improve their performance that wasn't thought to be possible.
As an approach for personal development, brain hacking seeks to enhance cognitive function and optimize efficacy and happiness. Brain-centered approaches to this end include meditation, metacognitive therapy, attention training and memory training.
Continuing to learn and challenge the brain is essential; initiatives like learning a new language or studying a new discipline improve the brain's ability to function. Research indicates that, to maximize the effect of brain hacking, learning experiences must be somewhat difficult and require effort. A more holistic approach to brain hacking includes various recommendations for health and well-being, such as a nutritious and varied diet, exercise, involvement in a community and time spent outdoors in nature.
Another area of brain hacking is the use of chemicals to stimulate the mind. These are formally called nootropics. Prescription stimulants, such as Adderall, are used to treat certain conditions. Other approaches include supplements promoted for brain health. Consumers are advised to be aware that claimed nootropics sold online often have not been proven safe or effective but might have anecdotal evidence supporting their use.
Most people engage in some form of brain hacking without knowing it. These can be simple motivation "hacks" or memory aids, such as a person placing their wallet on their shoes so they don't forget it. Or they recognize they usually feel tired and unmotivated in the afternoon, so they do their most important work in the morning.
Caffeine is a known nootropic and is almost universally used in coffee or tea. L-Theanine, found in green tea, increases alertness. Drinking those beverages might be hacking the brain without the user even knowing it.
Brain hacking others
In more recent use, the term hacking might be more often associated with illicit access and unauthorized use of something. In this use, the term brain hacking refers to someone intentionally using the quirks of the human mind against another person's interests.
A simple, innocuous use of brain hacking in this sense might be magic tricks. A magician intentionally uses misdirection and optical illusions to trick the brain into thinking one thing is happening while something else is going on.
Not all brain hacking is so innocent. External parties, such as marketers and product designers, use it to influence individual behavior. Social engineering, which exploits individual vulnerabilities to conduct security breaches, can also be considered a type of brain hacking. When the intention is to manipulate the target's behavior without their knowledge or consent, brain hacking is sometimes referred to as brain hijacking.
Marketers and product designers adopt principles from neuroscience, behavioral psychology and sociology to develop compulsive elements for user interfaces, mobile apps, social media, games and marketing content. This is called neuromarketing. While designing marketing materials, organizations might use brain scans, eye trackers or skin response to determine how effective the approach is.
Gamification can place addictive game-like elements into other apps. This can "hijack" the brain into thinking something is more pleasurable than it otherwise should be. An example of this is adding login streaks, or random rewards with slot machine or gacha-style elements to reward small behaviors.
Illicit and addictive drugs also "hack" the brain. They can affect the chemical balance and tap directly into pleasure and reward systems to make someone desire them.
Brain hacking technology
An emerging use of brain hacking is the direct application of computers and technology to the human brain. Augmented intelligence uses technology to increase a user's capability. Currently, this is simply using computers and the internet to store and access information quickly. It is expected that as AI and augmented reality become more capable, more of what a person perceives will be filtered through computers.
Things that were once considered science fiction are beginning to look possible. brain computer interfaces for applications in occupational therapy or gaming are in human trials. This also might allow for more direct human augmentation, or biohacking.
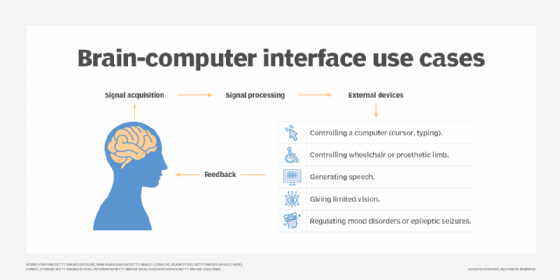
Ethics of brain hacking
A person's mind is their most valuable and personal asset -- their very self. So, intentionally manipulating it can have unforeseen ramifications.
Just as it is in other IT fields such as AI and data collection, consent is considered the first step in ethical brain hacking. A person trying to better themselves might ask for it, but many techniques might unethically manipulate a person through addictive mechanisms.
Many of the technologies to enhance the brain are experimental. The long-term effects are unknown and might cause problems later. Others might have no real effect and mainly act as placebos.
For techniques that are safe and effective, one issue is that they might not be equally available. For example, if a technique is only available to certain people, such as wealthy individuals, could this create a gap in performance and give them unfair advantages?