agnostic
What is agnostic?
Agnostic, in an information technology (IT) context, refers to something that is generalized so that it is interoperable among various systems. The term can refer to software and hardware, as well as business processes or practices.
The word agnostic comes from the Greek a-, meaning without, and gnōsis, meaning knowledge. In IT, that translates to the ability of something to function without "knowing" or requiring anything from the underlying details of the system it is working within. As with interoperability, agnosticism is typically enabled either by compliance with widely used standards or added elements -- such as coding -- that will enable one system to function in various environments.
Agnostic design advantages and disadvantages
Designing systems to be agnostic has several advantages and disadvantages for both vendors and their customers.
Advantages
Wider audience and customer base. Most people and organizations already have computers or servers and an understanding of how to operate and maintain them. If a product is designed in a vendor- agnostic way, it can be purchased and used by any customer no matter what type of system they already have. Because this is beneficial for customers, the approach can help vendors gain market share.
Easier adoption. Customers can more quickly integrate a product built with an agnostic approach into their existing systems. This can reduce roll-out time and require less training for end users.
Greater longevity. Hardware or software built to be agnostic does not rely on other systems or components that vendors may overhaul or phase out over time. The lifespan of these agnostic products is generally longer than products with dependencies for part or all of their functionality.
Disadvantages
More complex. Agnostic products typically require extra functions to support a spectrum of different hardware or software. These could be anything from simple case code for websites to maintaining separate codebases and compilers for different operating systems. Added complexity leads to higher creation and maintenance cost.
Lower performance. To make a product platform agnostic at a reasonable cost, it is often designed for the least common denominator -- the simplest set of common functionalities between the possible platforms. This often means that it lacks platform-specific optimizations that could benefit the product's efficiency and capabilities. Additionally, the customizations to support several platforms may add redundancy or bloat, further impacting performance.
Harder to create and maintain. The added complexity leads to longer development time, which in turn leads to longer time to market and greater costs. The product will also often need to be updated for each underlying platform's updates and changes.
Examples of agnosticism in IT
In IT, examples of applying agnosticism are abundant:
- Platform-agnostic software runs on any combination of operating system and underlying processor architecture. Such applications are sometimes called cross-platform. Examples include software that can be run on Windows, macOS and Linux.
- Device-agnostic software operates across various types of devices, including desktop computers, laptops, tablet PCs and smartphones. Most web apps are designed to be device agnostic and may implement responsive design to achieve this.
- Database-agnostic software functions with any vendor's database management system. Typical database-agnostic products include business analytics and ERP software. For example, such software could run on MySQL or the Microsoft SQL database.
- Protocol-agnostic software is independent of, or can be used with, several communication protocols. It negotiates or can be configured with a protocol to its peer and begins communication. Multiprotocol Label Switching and Generalized Multiprotocol Label Switching are examples of protocol-agnostic networking standards.
- Business process-agnostic software functions in different business environments. One example is a business process-agnostic business service that encapsulates logic associated with a specific business entity such as "invoice" or "claim."
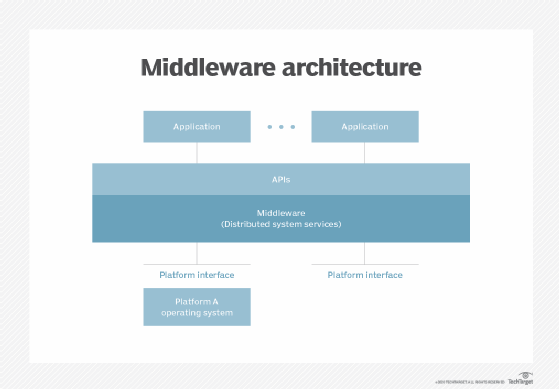
- Vendor-agnostic middleware can mediate between software from multiple vendors rather than between two specific applications.
- Hardware-agnostic licensing is a per-device or per-user model rather than a model where each license is tied to a specific device or virtual machine.
- Language-agnostic programming choses the programming language according to its suitability to the task rather than the programming team's preference or skills.
- Cloud-agnostic software is designed to run on any popular public cloud vendor systems and to be easily moved between them based on cost or the customer's preference. For example, most cloud-agnostic software can run on AWS, Google Cloud or Microsoft Azure.
See also: portability, backward compatible, open, open source.
