power-on reset (PoR)
What is power-on reset (PoR)?
A power-on reset (PoR) is a circuit that provides a predictable, regulated voltage to a microprocessor or microcontroller with the initial application of power. The PoR system ensures that the microprocessor or microcontroller will start in the same condition every time that it's powered up.
When power is first applied to an electronic device, such as a central processing unit (CPU) or other sophisticated digital system, the countless transistors that make up any of the related digital devices assume unknown states. As a result, the digital circuitry can behave in unpredictable -- and often undesirable -- ways. A critical aspect of digital system design is the initialization process intended to bring a system from its raw and unpredictable state to a known and desirable state every time it's turned on before the user gets access.
How does power-on reset work?
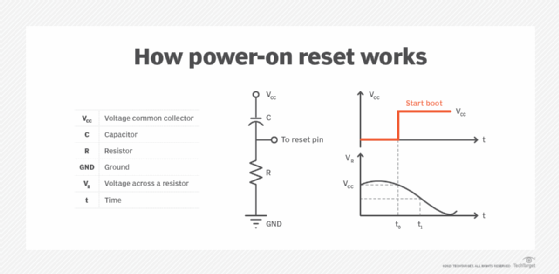
PoR typically is the first step in this initialization process. It ensures that stable and adequate supply voltages are available to the circuit. A PoR system can be a peripheral chip, sometimes called a voltage supervisor or reset integrated circuit.
The most basic PoR system includes a resistor and capacitor connected together with values set so that the capacitor takes a predictable and constant time to charge up when power is first applied. However, for computer use, additional components often are required, including a circuit called a Schmitt trigger.
Once the power-on reset circuit recognizes suitable and stable voltage levels to the system, it delivers a digital signal that enables the rest of the system initialization process to continue. For a computer, this starts the power-on self-test (POST) initialization cycle.
For a typical computer system, the PoR sequence starts as soon as the power button is pressed and system power is turned on. A typical sequence includes the following:
- The main power supply is enabled -- for servers with multiple power supplies, all supplies are enabled.
- Hot swap circuits for redundant power supplies are enabled.
- The main 12 volts direct current (VDC) rail is enabled.
- Additional DC outputs are enabled, such as 1.5/3.3/-12 VDC or 1.8/2.5/1.25 VDC outputs.
- Regulated CPU voltages are validated, such as 1.2 or 1.5 VDC.
- When all DC outputs are within 5%, a voltage monitor chip, which asserts the PoR signal, waits about 210 milliseconds (ms) and then asserts a Power Good signal that lets the POST or other initialization process begin.
The total amount of time needed from pressing the power button to a successful Power Good signal is usually less than 500 ms.
What are the benefits of PoR?
The principal benefit of PoR is system operational integrity at startup. A well-designed PoR circuit can ensure that, when power is applied to a computer, it starts up properly every time.
In doing this, PoR addresses two little-discussed realities of real-world physics:
- Reliable conditions. When a real power supply is activated, its output voltages might require several milliseconds to start, climb and then stabilize at levels that are safe and acceptable for sensitive electronic circuits. At the same time, digital circuits are highly dependent on known supply voltage levels to operate in a stable and reliable manner. If the supply voltages are wrong, unstable or changing, such as when starting up, digital circuits can behave unpredictably. For example, low voltage can result in a brownout condition, which can cause logic condition errors. Voltages that are too high can cause overvoltage conditions that can damage delicate chips. PoR prevents electronic devices from operating in unreliable conditions by holding initialization until operational voltage levels are known to be good.
- Suitable power levels. Digital devices power on in random states. A carefully choreographed POST sequence is required to test and initialize devices, clear and organize memory, establish critical interfaces, and perform other steps needed to prepare computer hardware to load an operating system (OS) and establish normal operation. PoR ensures this raw and unpredictable power-on state is never allowed to perform actual operation by forcing the system to wait for suitable power levels and successfully begin the initialization sequence.
PoR best practices
There are several best practices electronic designers working with PoR circuits should consider, such as the following:
- Adjustable threshold voltages. Some PoR or voltage supervisor chips allow the use of an adjustable threshold voltage that lets designers set the most desirable voltage level to monitor and on which to base PoR signals. Most circuit designs work best with fixed threshold voltages. However, prototype circuits potentially can benefit from adjustable thresholds for purposes of experimentation to optimize stability and performance.
- Manual resets tied to the PoR circuit. Many circuit designs make provisions for manual system resets through the PoR or voltage supervisor chip. These are typically small buttons that a user can press to force a system reset, such as a reboot, if the system should become erratic or unresponsive.
- Power-fail inputs. Some PoR or voltage supervisor chips provide additional inputs that allow the chip to monitor power supplies other than the main power supply, such as a backup power supply in mission-critical servers. This can help the chip detect potential failures in other power systems and take action, such as halting the system or triggering a system handoff, before a critical failure occurs.
- Watchdog timer inputs. Some PoR or voltage supervisor chips provide supplementary inputs that wait for signal activity on those watchdog inputs. These are often used to watch for critical signals or monitor the health of the physical hardware at critical points in the circuit. If a watchdog signal fails, the PoR chip can generate a reset signal.
Power-on reset vs. system reset: What's the difference?
A power-on reset is a circuit that watches voltage levels and holds circuit operation until voltage levels reach suitable levels. The PoR circuit can reset the system if voltage levels fall outside required levels or if other signals, such as a manual reset button or watchdog timer inputs in some PoR chips, trigger a reset state. PoR is generally called a hardware reset.
A system reset is a process or sequence that triggers a reset or reboot. A common example is the Ctrl-Alt-Del key sequence in the Windows OS. This might include a manual acknowledgement by the user before completing the reset. A system reset is typically called a software reset or soft reset because it can be triggered even when no hardware fault or trigger condition exists.
Find out how to extend the life span of your organization's PCs with a proper lifecycle management policy.
