digital marketing
What is digital marketing?
Digital marketing is the promotion and marketing of goods and services to consumers through digital channels and electronic technologies. These digital channels can include the internet, mobile devices, social media platforms, webinars, search engines, online customer communities and other digital platforms.
Digital marketing also includes a range of approaches and tactics to reach and persuade the target audience through digital media, including email marketing, social media marketing, search engine optimization (SEO), content marketing and online advertising.
The process can involve digital marketing tactics -- for example, creating an omnichannel presence, developing trust with consumers, using marketing automation tools and personalizing marketing content -- similar to those in traditional marketing. Organizations can combine both traditional and digital marketing techniques as a strategy.
With a digital marketing strategy, organizations are able to support larger marketing campaigns to improve brand awareness and recognition, generate leads, increase website traffic and, ultimately, drive sales and business growth. Digital marketing is effective because organizations can target broad and specific audiences with relevant campaigns and messaging.
Importance of digital marketing
The use of digital marketing has surged due to the widespread availability of digital platforms and plays an important role for businesses in the following ways:
- Digital marketing helps an organization appeal to a much larger audience than it could through traditional marketing methods, as the reach of the internet is worldwide. This marketing method also lets organizations target prospective customers who are most likely to buy their product or service. For example, a company can advertise holiday sales by emailing past customers or by sharing news of the deals on social media.
- Organizations have several different online methods they can use to reach out to customers, including emails, social media, mobile marketing apps, text messages, banner advertisements or affiliate marketing.
- Social media channels provide a way for individuals to interact and communicate with organizations. Likewise, marketers can collect insights from their target audience on these platforms and increase customer engagement by communicating with them. Digital marketing strategies can be quickly shifted as needed. The platform and format of communication can be changed if the target audience moves platforms, for example.
- Digital marketing lets organizations use a variety of tools and metrics to understand the behavior and preferences of customers, prospects and leads. From social media listening to predictive analytics and big data analytics, organizations can enlist a variety of resources to understand customer responses to their digital marketing efforts.
- Digital marketing is more cost-effective than traditional marketing -- as there are few upfront costs -- and it reaches a broader audience.
- An effective digital marketing strategy can create more opportunities for small and medium-sized businesses (SMBs) to compete with larger companies.
Types of digital marketing
Digital marketing applies to all industries and business types but requires a tailored approach to be effective. As such, digital marketing can appear in many forms, including the following:
- Email marketing. Organizations reach out to customers and prospects through email to promote current business practices such as sales or events.
- Social media marketing. Organizations use social media marketing through social networks and platforms, including Facebook, X (formerly known as Twitter), LinkedIn and Pinterest to connect and communicate with customers and prospective customers, notifying them of updates or deals, as well as just communicating and building social trust.

- Pay-per-click advertising. PPC advertising lets organizations advertise on different websites with paid ads. An example of such an advertisement is a banner ad. If enough data or cookies are collected about a user, these ads can be targeted by characteristics such as age, gender, location or general interests. The ad publisher is paid every time a user clicks on the ad.
- Content marketing. This digital marketing strategy tries to reach customers through content. Content refers to something an organization produces and publishes on a website with the intent to promote it through other marketing types, such as social media or email.
- Sponsored content. An organization pays another business to create and promote content that highlights the marketer's product or service.
- Affiliate marketing. An organization pays a commission to an influencer on a specific platform, such as YouTube or Instagram, to promote its product or service.
- Short Message Service marketing. Organizations might choose to use SMS messages to send promotions to customers. Political candidates running for office commonly send SMS messages as a part of their campaigning efforts.
- Video marketing. Video marketing involves using video content to promote products, services or brands across digital channels. It can be used across different platforms, including social media sites such as YouTube, Facebook, Instagram and TikTok, as well as on company websites. Video marketing can also take the form of product demonstrations, customer testimonials or live-streaming events. It can engage viewers, raise brand awareness and drive conversions by using appealing visuals and storytelling.
- Website marketing. This is when an organization uses its own website to showcase its brand and any offered products, services and deals in a clear way that will leave the viewer with a lasting impression.
- Native marketing. This type of marketing blends advertising into its surrounding content. Advertisements of this type should have the same look and feel as the platform so users aren't immediately put off by the ad. Ads should be labeled clearly so as to not mislead consumers.
- Marketing automation. Marketing automation software has become increasingly important to digital marketing, as companies try to reach a broader swath of potential customers and link customer behavior with potential new purchases. For example, organizations use marketing automation to measure visitor behavior on their websites, and then target visitors to potentially sell products and services.
Digital marketer roles, and the KPIs they measure
Digital marketing encompasses a wide range of roles and responsibilities. Some common digital marketing roles and the key performance indicators (KPIs) they measure include the following:
SEO specialist
An SEO specialist focuses on optimizing websites and content to improve search engine rankings. To increase organic traffic, they conduct keyword research, build backlinks, optimize on-page elements and analyze website performance.
KPIs measured include the following:
- Organic traffic.
- Keyword rankings.
- Backlinks.
- Click-through rate (CTR) from search results.
- Bounce rate and time on page.
Content marketing specialist
A content marketing specialist is responsible for producing and overseeing content for numerous digital platforms. They plan content strategy, manage content production, ensure brand coherence and assess content effectiveness.
KPIs measured include the following:
- Website traffic.
- Time on page.
- Conversion rate.
- Bounce rate.
- Lead generation from content.
Social media manager
A social media manager oversees and executes social media strategies across various platforms. They produce and curate content, interact with viewers, perform sentiment analysis, track social media data and optimize social media strategies.
KPIs measured include the following:
- Follower growth.
- Reach.
- Shares.
- CTR.
- Engagement rate.
- Sentiment analysis.
- Conversions from social media.
Email marketing specialist
An email marketing specialist creates and executes email marketing campaigns. They also create email templates, divide the audience into groups, evaluate the success of digital marketing campaigns and generate compelling email content.
KPIs measured include the following:
- Open rate.
- CTR.
- Conversion rate.
- Unsubscribe rate.
- Revenue generated from email campaigns.
Copywriter
A copywriter generates persuasive and engaging writing for digital marketing efforts. They produce engaging content for websites, advertisements, emails, social media posts and other marketing materials.
KPIs measured include the following:
- Number of content pieces written in a specific time frame.
- Sales revenue.
- Conversion rates.
- CTR.
- Social media shares.
- Brand consistency.
Digital marketing project manager
Digital marketing project managers are responsible for overseeing the entirety of marketing initiatives. They streamline an organization's marketing workflows, procedures and systems using project management tools and techniques.
KPIs measured include the following:
- Overall campaign performance.
- Return on investment (ROI).
- Cost per lead.
- Project timeline adherence.
- Customer acquisition cost.
Marketing automation manager
Marketing automation managers help select and manage the automation software used by the marketing teams. If marketing operations are done separately, a marketing automation manager groups them into their respective campaigns to track their performance.
KPIs measured include the following:
- ROI.
- Deliverability.
- Open rate.
- Click rate.
- Unsubscribes.
- Conversion rate.
Inbound marketing vs. digital marketing
Inbound marketing is a strategy that focuses on attracting customers using company-created web content. The goal of inbound marketing is for customers to come to the organization rather than having marketers compete for customers' attention.
Examples of inbound marketing content and tactics include the following:
- Blog posts.
- Photos.
- Infographics.
- Videos.
- Podcasts.
- Presentations.
- E-books.
- White papers.
- E-newsletters.
- Webinars.
- SEO.
- Social media marketing.
The difference between inbound and digital marketing is that digital marketing doesn't differentiate between inbound and outbound methods and can be useful for both techniques. Digital marketing is used as an umbrella term for all marketing that encompasses digital outreach, and typically includes strategies such as company-created content on blogs and social media that inbound marketing also uses. Inbound marketing targets customers through online marketing and platforms, such as social media or search engines, and is intended to create content that shows up in these places to drive organic traffic to an organization's website.
While outbound marketing can potentially reach a wider audience, it also runs the risk of sending uninterested consumers a barrage of unwanted material. Inbound marketing is designed to reach interested prospects through audience segmentation, such as demographics. However, by its nature, it might reach a much narrower group of potential customers.
Inbound marketing is also an important tool in retaining existing customers. Creating more regular communications with customers and enabling organizations to engage with customers by providing informative, educational content and promotions helps keep customer attention.
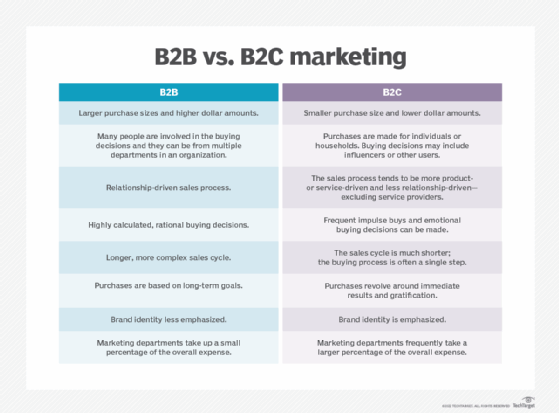
B2B vs. B2C digital marketing
Business-to-business (B2B) digital marketing is focused on online lead generation with the goal of an organization finding another business to purchase its products or services. This type of marketing is typically focused on more professional, business-centered channels such as LinkedIn.
Business-to-consumer (B2C) digital marketing is focused on attracting individuals and having them become customers. It also pays more attention to creating an accelerated buyer's journey for customers. B2C digital marketing is typically focused on more social-centered channels, such as YouTube, Facebook and influencer marketing channels.
B2B clients typically have a longer decision-making process, as it requires more than one person's input. B2C customers, on the other hand, only need their own input -- and can also make purchasing decisions based on emotion or mood. B2C customers might also respond better to social media marketing or short-term deals and offers that appear in email digital marketing.
Digital marketing benefits
Benefits of digital marketing include the following:
- Global and local reach. Individuals can see the same ad in different time zones or across the globe. Digital marketing also improves local ad visibility, so organizations can customize their locally targeted ads.
- Targeting specific audiences. Customers and prospective customers can stay connected to brands through email or social media platforms, where organizations can then communicate with them or test offers to gain insights.
- Cost-effectiveness. Digital marketing is less expensive than traditional forms of marketing, such as TV spots. It costs almost nothing to promote through email campaigns, for example.
- Customized channels. Digital marketing channels can be marketed differently, depending on the organization and the platform it's on. Marketing teams within an organization can find their best and strongest forms of marketing and modify them as needed.
- Personalization. Data collected about customers can be used to market more relevant products and services to them, and automated digital marketing platforms can help do this in real-time.
- Improved conversion rates. Digital marketing can increase conversion rates by using accurate targeting, tailored messages and improved user experiences. Businesses can considerably increase their capacity to turn leads into devoted customers by skillfully delivering targeted messages to the right audience at the right time.
- Improved competition. SMBs using an effective digital marketing strategy can compete with larger businesses due to the increased reach.
- Measurability. Digital marketing offers a number of measurable data points for an organization to analyze. If a specific digital marketing campaign isn't creating as much of a reach, or is not converting as many potential customers, an organization can use these data points to quickly change its marketing strategy.
Digital marketing challenges
Digital marketing does have the following challenges, however:
- Time-consuming. Organizations must continually create content and optimize their marketing campaigns, which takes time.
- Competitive. This can occur when prospective customers are inundated with too many competing ads. Marketers must make their brand stand out, which can be challenging.
- Data privacy. If an organization is using an individual's data to target them for advertising, it should understand how to handle that data and follow data privacy laws. Data privacy regulations consistently change in different locations over time. As an organization grows in its outreach efforts, it must also ensure its compliance with any local laws.
- Technology. Digital marketers must ensure websites are set up for mobile users sothe customer journey can quickly lead a prospective customer from learning about an organization to making a purchase.
- Complexity. Digital marketing has become more complex because of the various new communication channels that have emerged, but also in terms of the analysis required to make sense of customers, prospects and their preferences.
When budgets are tight, it's crucial to get the most out of every dollar spent on digital marketing. Dive into our tips that are designed to optimize your digital marketing efforts, even with a restricted budget.







