anonymous FTP (File Transfer Protocol)
What is anonymous FTP (File Transfer Protocol)?
Anonymous File Transfer Protocol (FTP) is a method that lets users access public files from a remote server or archive site without requiring them to identify themselves to the server or site. The user uses an FTP program or the FTP command interface and enters "anonymous" as their user ID. The password may be furnished by the FTP server or the user may provide their own.
Anonymous FTP is a way for remote users to use an FTP server even if they don't have an assigned user ID and password. It enables unprotected access of selected information about a remote system without entering a password. The information is usually publicly accessible, which means it can be read by anyone who logs into the server. However, the remote site determines what this information would be or how much would be available for general access. The person or organization that owns the information and the remote system must control their information and ensure that only appropriate information is made available for public access.
To access the information, the user logs onto the FTP host server using the user ID anonymous and any password. The user account will typically accept any string as a password, including the user's email address. After they log in, the user will have limited access rights to the files on the server. The server also imposes some operating restrictions so only certain operations are allowed on the anonymous FTP. These include the following:
- logging onto the FTP server;
- listing the contents of or files under a limited number of directories; and
- retrieving files and content from these directories.
To retrieve a file, the user can browse the archives and find what they need, but most users usually know the file pathname and information about the host it belongs to. The pathname specifies the directory and subdirectories that house the file, along with the file name. Anonymous users are usually not allowed to transfer files to the FTP server or archive site.
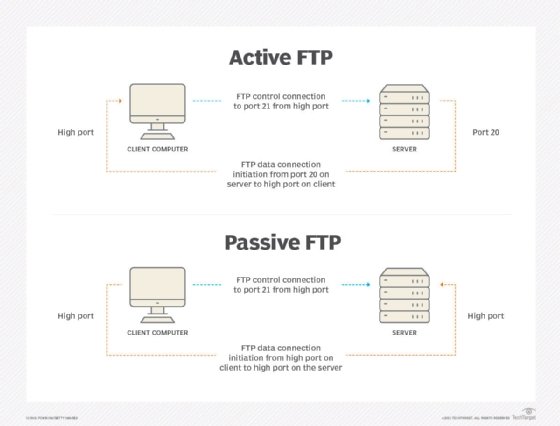
How do anonymous FTP sessions work?
An anonymous FTP session starts when a user logs into a remote server. To start the session, they will use the ftp command and the hostname/IP. The user could use either of the following commands to access the archive site via FTP:
ftp openfiles.samplecompany.com
ftp 128.103.129.6
This will invoke the FTP program and establish the user's connection to the remote host. At this point, they can see the contents of the server and retrieve the files they need. After they finish, they will exit the FTP program, which will close the connection and terminate the anonymous FTP session. Every response the FTP program gives is preceded by a number called a reply code. The user's password -- whatever it may be -- is never shown on the screen.
Here's how an anonymous FTP session works step by step.
- The user logs into the local host and invokes the FTP program.
- They open a connection to the host using either the host name or its IP address.
- After connecting to the remote host, they log in with the username "anonymous."
- They provide a password. This could be "guest," their email address, or anything else that the site requests.
- They issue the requisite FTP commands depending on what they want to do on the archive site (e.g., change directories or retrieve a file from a particular directory).
- The user exits the FTP program.
- The connection to the archive host closes and the anonymous FTP session is terminated.
Anonymous FTP advantages and disadvantages
Anonymous FTP doesn't require authentication, making it easy for users to log into an archive site and retrieve files from it. Some anonymous FTP sites support simultaneous transfer of multiple directories or files, speeding up transfers.
Contrary to popular belief, anonymous FTP is not completely anonymous, so users concerned about their privacy should be wary of using anonymous FTP-supporting archive sites. The drawback for the site owners is that they don't have complete control over who accesses the FTP server or its files. For this reason, they must be careful about files they choose to make public.
Finally, anonymous FTP archive sites, due to their public nature, are vulnerable to cyber attack. Moreover, a compromise of any one part of the site can compromise the entire site. To protect the site from exploitation and breaches, additional security controls are essential.
Common commands in anonymous FTP
Once the user initiates the anonymous FTP session, the on-screen output generally looks something like the following:
331 Guest login ok, send ident as password.
Password: [email protected]
230 Guest login ok, access restrictions apply.
ftp>
When they reach the ftp> prompt, they are logged into the archive site/remote server. At this point, they can use several commands.
The dir command lists the files in the current directory.
ftp> dir
This command usually produces different results on different operating systems.
A variation on the dir command is the outfilename command.
ftp> dir a* outfilename
This command will take the output of all files that begin with "a" inside the directory and put it into a file on the local system. The contents of the file can then be read outside the FTP environment.
Another common command is cd.
At the start of the FTP session, the user is in a top-level directory. To change the current directory and see the directories below it (e.g., /pub), the cd command is used.
ftp> cd pub
The command will give the following response:
250 CWD command successful.
The get and put commands are required for file transfers. To get a file from the remote computer to the local system, the command is as follows:
ftp> get filename
Similarly, the put command will transfer a file from the local system to the remote system as long the permissions are set up for a user's FTP session to write to a remote directory. The command syntax is as follows:
ftp> put filename
Variations of the get and put commands are mget and mput. These commands let users transfer multiple files to or from the remote server, rather than doing it manually one by one.
The following command will get all files beginning with "f" from the remote system:
ftp> mget f*
And use the following command to put all files beginning with "z" to the remote system:
ftp> mput *.z
Anonymous FTP best practices
Many sites support FTP but not all permit anonymous transfers. In such cases, users should not try to get files from the system unless they have explicit permission to do so. In case of access problems, they should first check with local support personnel before asking the archive administrator for help.
It's also good practice to restrict FTP access to non-prime hours to avoid inconveniencing the site's primary users. This practice is especially important for sites in a different geography or time zone.
Some archive sites that offer anonymous FTP limit the number of concurrent AFTP logins. New users trying to log in may see an error message. In such situations, it's advisable to wait for some time before attempting another connection and overloading the site further.
Check out 8 secure file transfer services for the enterprise, learn about 7 common file sharing security risks and explore top secure data transmission methods.
