most significant bit (MSB)
What is most significant bit (MSB)?
The most significant bit (MSB) is the bit in a multiple-bit binary number with the largest value. This is usually the bit farthest to the left, or the bit transmitted first in a sequence. For example, in the binary number 1000, the MSB is 1, and in the binary number 0111, the MSB is 0.

When the MSB in a sequence is farthest to the left (or first), the least significant bit (LSB) is usually the one farthest to the right (or last). For example, the decimal number 157 is equal to the binary number 10011101 (or hexadecimal value 9D).
The 1 at the left side of the binary number is the MSB because it has a place value of 128, the highest value in the byte, and the 1 at the right side of the binary number is the LSB, which has a place value of 1, the lowest value in the byte.
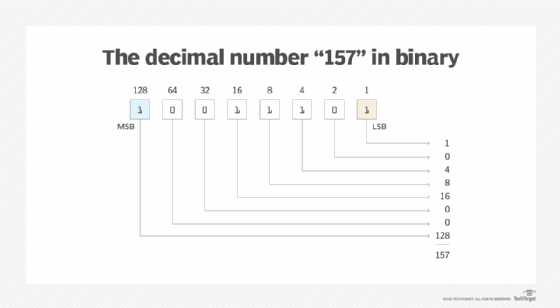
Both MSB and LSB can play a role when transmitting and storing data. For example, if the bits are sent serially over the network -- one bit at a time -- they are typically transmitted in one of two ways: MSB first or LSB first. A bit is designated as most significant because it has the greatest place value in the binary number, so the least significant bit lies at the other end. This is important information to have when receiving or retrieving data because it tells a program how to interpret the binary data.
The concept of MSB and LSB can also apply to bytes. The most significant byte is the byte in a multiple-byte word with the largest value. As with bits, the most significant byte is normally the byte farthest to the left or the byte transmitted first in a sequence. In this case, the byte sequence is said to be big-endian because the order starts with the "big end" (the most significant byte). If the order were reversed so the MSB is farthest to the right (or last) and the LSB is farthest to the left (or first), the sequence is said to be little-endian.
Consider an example. The decimal number 36,765 can be stored as a two-byte binary number: 10001111 10011101. This is equivalent to the hexadecimal value 8F9D, in which 8F represents the first byte and 9D represents the second byte.
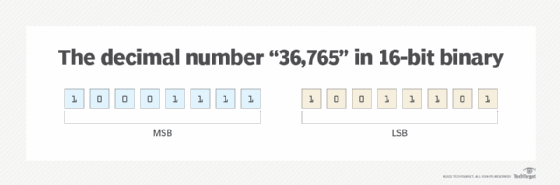
The first byte in the binary sequence is considered the most significant because it has the largest value. The hexadecimal number reflects this by listing the MSB first (8F), followed by the LSB (9D). The hexadecimal value, like the binary sequence, is considered big-endian format. However, if the hexadecimal value is listed as 9D8F, the order is little-endian because the LSB is listed first.
Under certain circumstances, byte sequences might be neither little-endian nor big-endian. In encrypted data, for example, the byte significance can be scrambled, in which case the MSB or LSB can appear anywhere in the sequence.
