
Getty Images/iStockphoto
Proof of work vs. proof of stake: What's the difference?
Proof of work and proof of stake use algorithms to validate cryptocurrency on a blockchain network. The main difference is how they choose and qualify users to add transactions.
Proof of work and proof of stake are both algorithms to keep the blockchain secure so users can add new cryptocurrency transactions. But there are a few differences between the two.
Cryptocurrency is decentralized and needs to be verified by computers to make the transactions visible. Both proof of work and proof of stake help users perform secure transactions by making it difficult and expensive for bad actors to commit fraud. They make participants prove they have supplied a resource to the blockchain such as energy, computing power or money.
The key difference between proof of work and proof of stake is how the blockchain algorithm qualifies and chooses users for adding transactions to the blockchain.
What is proof of work?
The proof of work consensus algorithm uses complex problems for miners to solve using high-powered computers. The problems are solved using trial and error. The first miner to complete the puzzle or cryptographic equation gets the authority to add new blocks to the blockchain for transactions. When the block is authenticated by a miner, the digital currency is then added to the blockchain. The miner also receives compensation with coins.
A proof-of-work system requires fast computers that use large amounts of energy resources. As the cryptocurrency network grows, the transaction times can slow down since it requires so much energy and power.
The blockchain network remains secure because it would require a bad actor to take over at least 51% of the network and its computing power. The blockchain can become forked, which means the community changes the blockchain's protocol and the chain splits into a second blockchain. To prevent duplicate transactions or spending, the history of the original also moves in a new direction. Miners can choose to move to the newer forked network or continue supporting the original. This makes it even more difficult for a bad actor to control 51% or more because they would have to split computing resources to both sides of the fork and support both blockchains to gain that amount of control.
Learn more about the history of blockchain technology here.
What is proof of stake?
Miners pledge an investment in digital currency before validating transactions with proof of stake. To validate blocks, miners need to put up stake with coins of their own. Miners also show how long they have been validating transactions. The choice for who validates each transaction is random using a weighted algorithm, which is weighted based on the amount of stake and the validation experience.
After a miner verifies a block, it is added to the chain, and the miner receives cryptocurrency for their fee along with their original stake. If the miner does not verify the block correctly, the miner's stake or coins can be lost. By making miners put up stake, they are less likely to steal coins or commit other fraud -- providing another layer of security.
The proof-of-stake system was designed to be an alternative to proof of work, addressing energy usage, environmental impact and scalability.
The main issue with proof of stake is the extensive investment upfront to buy a network stake. Those with the most money can have the most control because of the algorithm weight to choose the validator. If a blockchain forks, a validator receives a duplicate copy of their stake because there is no track record of performance. If the validator agrees to both sides of the fork, they could potentially double-spend their coins.
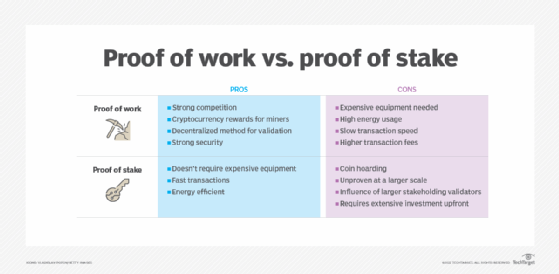
What is the difference between proof of work and proof of stake?
Along with the way miners' transactions are validated, there are two other significant differences between the two methods -- energy consumption and risk of attack.
Energy consumption
One of the biggest differences between proof of stake and proof of work is the amount of electricity used. A big complaint from cryptocurrency critics is the electricity use. Proof of work uses significantly more energy because of its authentication model that uses high-powered computers.
For example, the University of Cambridge estimates that Bitcoin -- which uses proof of work for mining -- consumes about .39% of the world's annual electricity. Bitcoin mining uses more electricity annually than the countries of Finland and Belgium.
The Ethereum network is in the process of transitioning to proof of stake. The Ethereum Foundation estimates this switch will use about 99.95% less energy.
The energy consumption is significantly less because proof of stake chooses validators randomly instead of miners completing complex puzzles. Transaction times are also quicker, which uses less energy.
Risk of attack
With proof of work, miners must compete to complete equations. Once a miner gets the blockchain block, the system relies on these miners to follow the rules and be trustworthy. However, if one group of miners gains more than 50% control, they can prevent transactions from being confirmed and can also spend coins twice -- fraud known as double-spending.
Learn about other types of cryptocurrency scams.
Proof of stake differs because it only allows miners to validate blocks if they have a security deposit or "stake." If attackers try dishonest processes, they lose their stake. There is no real benefit for cryptocurrency attackers to disrupt the blockchain because they can't double-spend coins or steal coins without losing their investment.








