What is a Consensus Algorithm?
What is a consensus algorithm?
A consensus algorithm is a process in computer science used to achieve agreement on a single data value among distributed processes or systems. These algorithms are designed to achieve reliability in a network involving multiple users or nodes. Solving this issue -- known as the consensus problem -- is important in distributed computing and multi-agent systems such as those seen in cryptocurrency blockchain networks.
How consensus algorithms work
Consensus algorithms are vital in large-scale, fault-tolerant systems because they enable a set of distributed/replicated machines or servers to work as a coherent group and agree on system state, even in the presence of failures or outages. To achieve this, the algorithm sets a threshold, or the number of member machines that must reach consensus or agreement.
As they solve a consensus problem, consensus algorithms assume some processes and systems will be unavailable and that only a portion of the nodes will respond. They also assume some communications will be lost during transmission. However, a response is required from the available nodes. For example, an algorithm may require that at least 51% of nodes respond to achieve consensus or agreement on a data value or network state.
This ensures consensus is achieved with minimal resources, even if the other resources are unavailable or even faulty. The mechanism also maintains the integrity of decisions taken by the agreeing nodes in the fault-tolerant system.

Applications of consensus algorithms in blockchain
Consensus algorithms have many real-world applications in decentralized or distributed computer networks. One of the most common applications is blockchain.
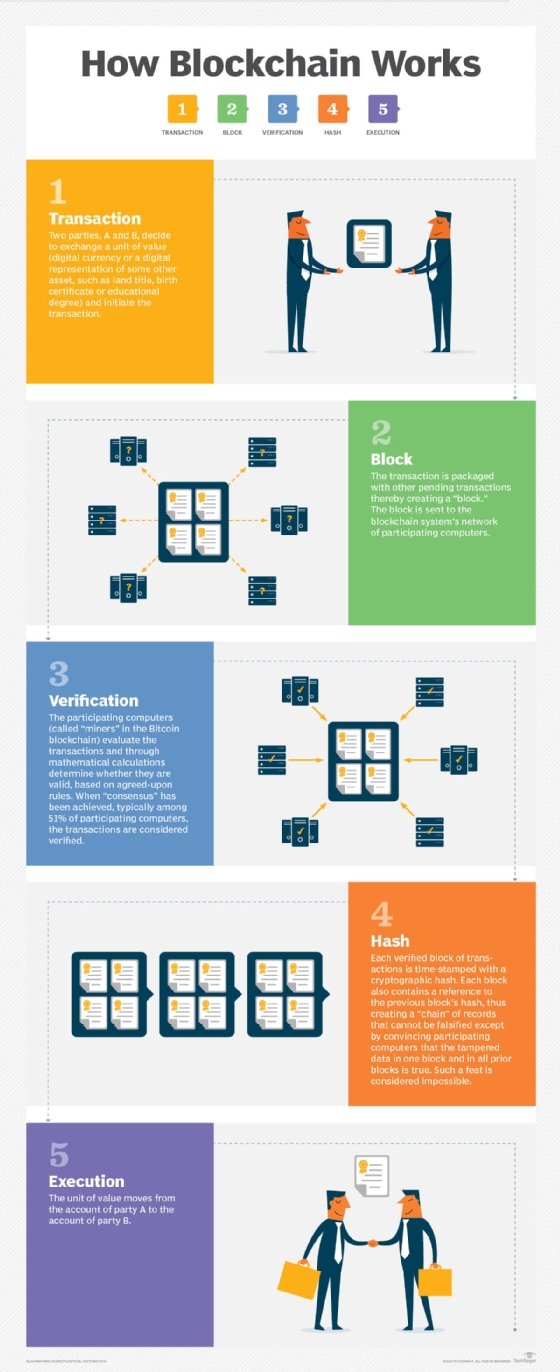
Blockchain is the distributed ledger most associated with bitcoin cryptocurrency. This decentralized database is collectively managed by distributed computers or nodes on a distributed peer-to-peer network. Each peer or node maintains a copy of the ledger to prevent a single point of failure. Any updates or validations on the network reflect in all copies simultaneously. This guarantees the fidelity and security of data records and generates trust in the system -- without the need for a centralized trusted third party.
Blockchain networks rely on consensus algorithms to reach agreement among various distributed nodes. A consensus mechanism such as proof of work (PoW) or proof of stake (PoS) secures the network and prevents unauthorized users from validating bad transactions. The mechanism also enables agreement on the network even when no single node is in charge.
Other applications of consensus algorithms
Based on an underlying mechanism, consensus algorithms decide whether to commit a distributed transaction to a database. They're also commonly used to synchronize data across a decentralized network and ensure consistency and transparency in transactions. Consensus algorithms are also used to assign a node the status of leader.
Consensus algorithms synchronize state machine replicas and ensure consistency among them. They're often used to achieve trust and security across a decentralized computer network, such as blockchain, and are very useful for recordkeeping.
In addition to blockchain and cryptocurrencies, these algorithms support many real-world computing and digital systems, including:
- replication of state machines,
- Google's PageRank,
- load balancing,
- smart power grids,
- clock synchronization and
- control of unmanned aerial vehicles like drones.
Types of consensus algorithms
Let's explore the many types of consensus algorithms.
1. Proof of Work
The PoW algorithm is one of the oldest types of consensus algorithms. First introduced in 1993 -- and reintroduced in 2008 by Bitcoin founder Satoshi Nakamoto -- the central idea of PoW is to have nodes solve complex mathematical puzzles and make as many guesses as possible in the fastest possible time.
In cryptocurrency blockchains based on the PoW algorithm, miners or validators -- also known as participant nodes -- must prove that the work they've done and submitted gives them the right to add new transactions to the blockchain. They must solve a complex mathematical problem by finding a cryptographic hash of a particular block.
This is done by taking data from a block header as an input, and continuously running this data through a cryptographic hash function. Every time this is done, small changes are made to the input data by including an arbitrary number called a nonce. This is the blockchain version of guesswork to find a solution.
Ultimately, when the miner finds the solution that leads to consensus, they're rewarded in cryptocurrency. However, all these actions require multiple iterations that consume a considerable amount of computational power. That's why PoW is considered an inefficient consensus mechanism.
Nonetheless, the PoW algorithm continues to be popular because it maintains network security and is fairly resistant to cyber attacks like DDoS attacks. It's also the oldest consensus algorithm and is known to work well on blockchains.
2. Delayed Proof of Work
Delayed Proof of Work (dPoW) is a modified version of the PoW consensus algorithm. In this consensus method, the blockchain network takes periodic snapshots of itself which are then written into a block on the network as part of a notarization process. This process helps to create a backup of the entire system on the blockchain.
Strictly speaking, dPoW is not a consensus algorithm because it's not used to achieve consensus on new blocks. Rather, it's a security mechanism that makes blockchains resistant to a 51% attack in which a single entity can control the majority of the hash rate on a blockchain network and cause serious network disruptions. This is possible because the dPoW resets the network's consensus rules whenever a block is notarized, making it impossible for notarized blocks to be reorganized.
3. Proof of Stake
Proof of Stake (PoS) is considered an alternative to PoW. Unlike PoW, PoS requires little specialized hardware or software resources to mine cryptocurrencies since it doesn't involve solving complex computational problems. Rather, crypto validators lock up or stake some of their coins in a wallet. They then validate blocks if they discover a block that can be added to the blockchain.
Validators get a reward -- or their stake increases -- proportionate to their bets based on the blocks added to the blockchain. Since the algorithm is incentive-based, it consumes less computational energy than PoW.
Despite this advantage, the PoS algorithm has a serious drawback. The mining capacity of a validator depends on the number of tokens they have, so a miner who starts with more coins gets more control over the consensus mechanism. Additionally, a few miners can purchase many coins, further diluting the mechanism and reducing the system's decentralization property.
4. Delegated Proof of Stake
Delegated Proof of Stake (DPoS) is considered a more efficient and democratic version of PoS. This algorithm is based on a voting system in which delegates or witnesses vote for their favorite validators to achieve consensus during the generation and validation of blocks. Besides validating transactions, delegates also help maintain the integrity, reliability and transparency of the blockchain network.
The voting power of each delegate is proportional to the number of coins held. They receive rewards for their work with transaction fees, which are shared with their respective electors.
The DPoS algorithm's voting system, and therefore the consensus mechanism, depends on the reputation of the delegates. It's a more scalable mechanism than PoW or PoS since it can process more transactions per second and provide faster confirmation times.
5. Proof of Authority
The Proof of Authority (PoA) consensus algorithm is a more efficient and scalable alternative to the power-hungry and less scalable PoW algorithm. Furthermore, in PoA, block validators stake their reputation and identities rather than coins, making the system more secure than PoS.
Essentially, a PoA-based blockchain network is secured by a limited number of validating nodes. These nodes are trusted parties that are arbitrarily chosen and pre-approved to verify blocks and transactions. These participants act as system moderators and help create a more scalable mechanism than PoW.
Since the real identities of these moderator nodes are known and trusted, PoA is highly suitable for logistical applications such as supply chains or trade networks. It enables users to avail themselves of all the benefits of blockchain technology while maintaining privacy and securing their transactions.
6. Proof of Burn
Proof of Burn (PoB) is being tested as a viable and sustainable alternative to PoW and PoS algorithms. PoB is like PoW, but it consumes much less computational energy. This is because its block validation process on the blockchain doesn't require computational resources or hardware. Instead, miners "burn" or invest coins in the blockchain to achieve consensus.
Coins are sent to an address from where they can't be retrieved, rendering them inaccessible and useless. This demonstrates the miners' commitment to the network and gives them the right to mine new coins and validate new transactions on the network. The more coins a miner burns, the more mining power they have, which increases their chances of becoming the next block validator.
Burning coins in PoB reduces the supply of coins and increases their value. It also improves the security of the network through an investment of burned coins.
7. Hybrid PoW/PoS consensus
A hybrid PoW/PoS mechanism counterbalances the weaknesses of PoW and PoS algorithms. It starts by having PoW miners create new blocks to add to a blockchain. After the blocks are created, PoS miners vote to confirm or reject them. During the process, they stake a portion of their tokens as in the PoS algorithm.
But unlike PoS, the total vote count isn't examined in this hybrid algorithm. Instead, five votes are randomly chosen to determine the efficacy of the new block. If three out of five votes are affirmative, consensus is reached, and the block is added to the blockchain. The reward system is proportionately distributed as 60% to PoW miners and 30% to PoS miners, with the remaining 10% allocated to improve the system.
See also machine learning algorithm, sorting algorithm, Ethereum, Hyperledger
