smartphone
What is a smartphone?
A smartphone is a cellular telephone with an integrated computer and other features not originally associated with telephones, such as an operating system (OS), web browsing and the ability to run software applications.
Smartphones are used by consumers and as part of a person's business or work. They provide access to many mobile applications and computing functions, and have become integral to everyday modern life.
Popular uses of smartphones
Common ways smartphones are used include the following:
- Email and messaging. Email and messaging applications can be loaded on a smartphone, letting users receive and send messages from their phone.
- Social media. Many consumers use smartphones to engage with friends, family and brands on social media. Social media platforms, such as Facebook, Instagram, Twitter and LinkedIn, have mobile apps that users download from a phone's app store. Smartphone apps make it possible for users to post personal updates and photos while on the go.
- Health and wellness. Another common use for smartphones is health and wellness tracking. For instance, the Health app for Apple iOS tracks sleep behavior, nutrition, body measurements, vital signs and mental health exercises.
- Connecting with other devices. Third-party wearable devices, such as smartwatches, can connect with a smartphone to monitor an individual's health statistics, such as heart rate and number of steps walked, and send that information to be aggregated on the phone.
- Mobile payment. Digital wallet features let users save credit card information on their phones to make mobile payments when buying items. Apps such as Apple Pay also enable users to pay other iOS users directly from their phones.
Smartphone use in the enterprise
BlackBerry devices were the first popular smartphone many organizations offered their employees for business use. They had a history of strong security. As smartphones added advanced productivity features and integrations with IT management tools, they gained popularity in the enterprise.
Many organizations support employees that want to use their smartphones for work. Enterprise mobility management tools help control how smartphones are used for business purposes. Most businesses have a bring-your-own-device policy to govern use for work-related activities. Apple and Google have improved the enterprise capabilities of their mobile operating systems, enabling IT to better support iPhones and Android phones in businesses.
Because of the smartphone's small form factor, they're typically used for quick tasks, such as sending an email. Tablets and 2-in-1 devices are other mobile devices that are used as alternatives to smartphones and PCs for conducting business.
Important smartphone features
One of the most important elements of a smartphone is its connection to an app store. These centralized portals let users search for and download software applications to run on their phones. A typical app store offers thousands of mobile apps for productivity, gaming, word processing, note-taking, organization, social media and more.
The following are some other key smartphone features:
- Internet access.
- A web browser.
- The ability to sync more than one email account to a device.
- Embedded memory.
- A hardware or software-based QWERTY keyboard.
- Wireless synchronization with other devices, such as laptop or desktop computers.
- The ability to download applications and run them independently.
- Support for third-party applications.
- The ability to run multiple applications concurrently.
- Touchscreen.
- Wi-Fi access.
- A digital camera, typically with video capability.
- Gaming.
- Unified messaging.
- Global positioning systems.
Smartphones also support accessories, including Bluetooth headphones, power charging cables and extra speakers. The outer casing of most smartphones is fragile, so users often buy screen protectors and cases for extra protection.
And, since smartphones run an OS and applications, vendors usually provide software updates. Individual mobile apps in an app store also provide updates that users can choose to install.
Benefits and limitations of smartphones
Portability is the most important benefit of smartphones. Users can perform many work-related and social activities on their phones, assuming they are properly configured. They can send and receive emails, set up meetings, work on reports, and other functions they might otherwise perform at their workplace.
During the COVID-19 pandemic, smartphones, with suitable connectivity to remote IT functions, greatly enhanced remote work. Smartphones are convenient and can be used just about anywhere a cellular signal is available. Newer 5G cell phone technology increases the data handling capabilities of smartphones.

There are several challenges associated with smartphones, including the following:
- Overuse. It's common to see people staring at their phones when walking on the street and in the middle of meetings.
- Social etiquette. It's increasingly considered rude to use a phone while others are talking.
- Battery life. On the technical side, battery life is a concern. Despite advances in battery technology, people often forget to recharge their phones.
- Health issues. When viewing smartphone display up close, that is, less than six inches away, energy emission from the display has been described as potentially damaging vision. Also, radio emissions from cell phones have been an ongoing health concern.
- Security. Smartphone security has always been a concern, and vendors have worked to protect their devices. With an increase in cyber attacks, smartphone users must make sure that their devices have strong security. Many IT organizations update their smartphones with company-approved security functions before the smartphone is assigned to an employee. Employees using their own smartphones may need software installed to conform to their employer's security requirements.
Smartphone vendors, manufacturers and prices
Vendors sell smartphones in different tiers and entry prices. Premium smartphone prices have started to rise -- costing $800-$1,000. Mid-range phones cost $500-$700, while budget phones fall under this price point. Original equipment manufacturers (OEMs) that make and sell smartphones commonly sell versions of a smartphone that meets all these price points.
Apple is the only vendor that builds the iPhone and its iOS operating system. The iPhone 14, 14 plus, 14 Pro and 14 Pro Max were released in September 2022. All models support memory ranging from 128 GB to 1 TB. Apple's A15 Bionic chip is used in the 14 and 14 Plus. The faster A16 Bionic chip powers the 14 Pro and 14 Pro Max models. Displays are either 6.1 or 6.7 inches.

Multiple OEMs produce smartphones that run the Android OS -- smartphones that use the Android OS are typically referred to as Android devices. Google offers the Google Pixel series, which includes the Pixel 6a, 7 and 7 Pro. Samsung offers several smartphone product lines, including the Galaxy S, A and Z series.
Other smartphone vendors include the following:
- Asus, with the ROG and Zenfone product lines.
- Huawei, with the P, Mate, Nova and Y Series lines.
- Lenovo, which includes Motorola.
- OnePlus, with OnePlus and OnePlus Nord phones.
- Oppo, with its Find, Reno and A Series lines.
- Vivo, with its X, V, Y and T Series.
- Xiaomi, with the Xiaomi and K20 Pro lines.
Smartphone designs and trends
The latest smartphone design trends include the following:
- Redesigns that make more room for the display.
- Offering two or three versions of a phone to provide different entry points.
- Removing as much of the bezel as possible.
- Moving away from the notch style that puts the camera, speaker and other sensors on a top section of the phone.
- Moving the camera inside the body to be pushed up by a mechanical motor.
- Moving the camera to a hole-punch in the display.
- Moving the earpiece speaker grill to areas such as a top slot of the phone.
- Phasing out headphone jacks.
- Adding features such as under-screen fingerprint readers, face unlock, 90-120 hertz (Hz) refresh rates, IP68 water resistance ratings, glass backs for wireless charging, reverse wireless charging, fast charging, virtual assistants, night mode for cameras and dual SIM card support.
Smartphone displays
Smartphones commonly use liquid crystal display (LCD) screens in their displays. However, organic light-emitting diode (OLED) displays are becoming more common and preferred by manufacturers.
An LCD is a flat panel display that uses liquid crystals as its primary form of control. LCDs are lit with a backlight as pixels are switched on and off electronically while using the liquid crystals to rotate polarized light. Polarizing glass filters are placed in front and behind the pixels, and the front filter is situated at 90 degrees.
Other display technologies are becoming more popular in smartphone displays, but LCDs still have a place in the market. They are common in budget to mid-tier smartphones as OLED-equipped models cost more.
Many flagship smartphones use OLED displays, because they're more flexible to implement. OLEDs use a single glass or plastic panel, compared to LCDs which use two. In addition, OLED displays don't need a backlight; this makes the phones thinner and provides deeper blacks because each pixel in an OLED display is individually lit.
If a display in an LCD screen is mostly black with only a small portion lit, the whole back panel is still lit, which causes light leakage on the front of the display. An OLED screen avoids this issue. OLED displays also have better contrast and viewing angles, and use less power.
With a plastic panel, an OLED display can be bent and folded over itself. This can be seen in smartphones such as the Samsung Galaxy Fold, in which the entire device folds. It's also used in the iPhone X, which will bend the bottom of the display over itself so the display's ribbon cable can reach in towards the phone, eliminating the need for a bottom bezel. Folding devices must have plastic front screens that bend. However, this means the display will likely scratch more easily.
Smartphone displays have started taking up more space on the front of a device, with some smartphones having edge-to-edge displays. For example, the iPhone 14 Pro has an 87% screen-to-body ratio, and the Samsung Galaxy Note 10 Plus has a 91% ratio.
In 2019, the Chinese company Xiaomi announced a phone with a screen-to-body ratio of 180.6%. The Mi Mix Alpha's OLED screen was intended to bend around nearly the entire phone, having a small non-screen band reach around the back for the 108-megapixel camera and 12-megapixel telephoto lens. The phone would be turned around so the user can take a selfie, using the back of the display to see themselves. The Mi Mix Alpha turned out to be too difficult to mass produce, and Xiaomi canceled its plans for it.
Smartphone displays usually have refresh rates of 60 Hz, 90 Hz or 120 Hz. Some manufacturers have increased the display's refresh rate as high as 240 Hz. The higher refresh rate makes for a smoother experience because there's less time between each frame. However, this also consumes more battery life.
Smartphone cameras
The cameras on smartphones commonly include a normal camera lens, a telephoto lens and a wide-angle lens. A telephoto lens lets users take photos of faraway subjects, while a wide-angle lens lets them take photos at a wide field of view with a short focal length. On the front-facing screen, there's usually a selfie camera and, in some cases, a wide-angle lens.
Some phones, like the iPhone 14 Pro, have three rear-facing cameras, while others, like the Pixel 6a have one camera -- relying primarily on computational photography. Computational photography is the use of computer processing in cameras to make a better-looking image beyond what the lens and sensor could traditionally pick up in one shot. All smartphones use some level of computational photography because they don't operate like shutter-based cameras.
Computational photography is used in smartphones because there is less space for a large lens to enhance pictures. Smartphones also have more processing power compared with digital cameras. That means they can automate many settings and provide additional photo editing tools. These provide a better photo-taking experience for the user.
Using image-processing algorithms, computational photography can improve images through methods such as reducing motion blur, adding simulated depth of field and even deleting unwanted images. Other settings and tools let users improve color, contrast and light range.
Some features in digital photography are based on both hardware and software. For example, in image stabilization, the camera's lens will move to compensate for small movements and shakes. The software side of image stabilization cross-references the picture with data from the gyroscope to enable broad movement stabilization. Smartphone cameras also take video, which makes use of image stabilization. Videos can commonly be taken at 720p at 30 frames per second (FPS), and up to 4K at 60 FPS.
Some smartphones like the Pixel 7 and 7 Pro also use machine learning to implement features like a depth estimation technique. It's used to estimate the depth of elements in an image.
Some front-facing cameras are being pushed up to the top of a screen with a notch or cutout at the edge of the phone. The notch will commonly hold the front-facing camera, speaker and other sensors that are used for features like face unlock. The common trend in smartphones is to eliminate bezels and the notch to leave as much room for the display as possible. To do this, smartphone companies have implemented new designs. Some smartphones, such as the Samsung Galaxy Note 10, will have a centered hole-punch cutout for a single front-facing camera. The Galaxy S23 has a hole-punch cutout for its camera and the S23+ has one for its cameras; both are in the upper right corner of the display.
Some smartphones, such as the Asus Zenfone 6, include a feature to flip the rear camera around to become the front-facing camera. A mechanical motor is sometimes implemented to eliminate the font notch, such as in the OnePlus 7 Pro. The mechanical motor inside the phone pushes the camera up through the top of the phone.
In 2019, the company Oppo announced an under-the-display, hidden selfie camera inside the body of the phone. The phone uses a custom transparent material with a redesigned pixel structure that allows light to enter through the camera portion of the display.
IOS and Android Software
If a user is basing their smartphone purchase on software, the two prominent ones are iOS and Android. Both OSes operate well. IOS is consistent across all iPhones, with changes only taking place in software updates. With Android devices, OEMs put a skin around the OS or customize the OS experience.
IOS 16 includes the following features:
- Updated lock screen.
- Updated setup for Focus function.
- More powerful Focus filters.
- Enhanced message editing.
- Enhanced search features.
Features in the Android 13 include the following:
- Themed app icons.
- New media controls.
- Different languages assigned to different apps.
- Enhanced security.
- Photo picker that shares selected photos and videos with specific apps.
- Updated notification permissions.
Cellphone vs. smartphone
A cellphone is simply a telephone that doesn't need a landline connection. Users can make and receive phone calls, and some cellphones also offer text messaging.
A smartphone has more advanced features, including web browsing, software applications and a mobile OS. Smartphones also offer capabilities such as biometrics support, video chatting and virtual assistants.
Smartphone history
The first smartphone was IBM's Simon, which was presented as a concept device -- rather than a consumer device -- at the 1992 COMDEX computer trade show. It could send emails and faxes, as well as keep a calendar of events, as opposed to simply making calls and sending messages.
Consumer smartphones evolved from personal digital assistants (PDAs) around 2000 when devices such as the PalmPilot began to include wireless connectivity. Several manufacturers, including Hewlett Packard and Nokia, released devices in 1996 that were combinations of PDAs and mobile phones, which were then called cellphones. They included early OSes and web browsing capabilities. BlackBerry released its first smartphone in 2002. They became popular with consumers and in the enterprise. Many of these early smartphones featured physical keyboards.
In 2007, LG released the Prada and Apple released the iPhone, the first smartphones to feature a touchscreen. HTC released its Dream smartphone a year later, which was the first to include Google's Android OS.
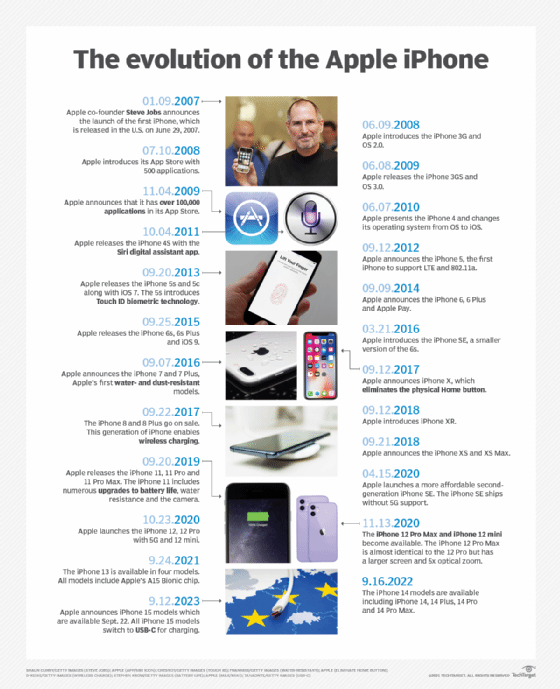
Other significant smartphone advancements include Sony's 2015 release of the Xperia Z5 Premium phone with a 4K resolution screen. Networking advancements in Wi-Fi and Long-Term Evolution have also progressed over the years, improving smartphone connectivity for faster use. In 2019, folding smartphones entered the market, such as Samsung's Galaxy Fold.
Ensuring the security of work-related data and communication on smartphones is a huge challenge. Learn more about mobile device security with this guide.





