volatile memory
What is volatile memory?
Volatile memory is a type of memory that maintains its data only while the device is powered. If the power is interrupted for any reason, the data is lost. Volatile memory is used extensively in computers -- ranging from servers to laptops -- as well as in other devices, such as printers, LCD displays, routers, cell phones, wearables and medical equipment.
In a computer, volatile memory is typically used for the system's random access memory (RAM), both the main memory and the processor's L1, L2 and L3 cache. It is distinguished from nonvolatile storage --such as solid-state drives (SSDs), hard disk drives (HDDs) or optical disks -- by the fact that nonvolatile devices retain their data even when their power is cut off.
A computer's volatile memory is sometimes referred to as primary storage, as opposed to secondary storage, which is typically made up of nonvolatile storage devices. However, the meanings of primary and secondary storage have evolved over the years, and the terms are now often used when describing tiered storage, although the original usage still persists.
Volatile memory is used for a computer's RAM because it is much faster to read from and write to than today's nonvolatile memory devices. Even the latest storage class memory (SCM) devices such as Intel Optane can't match the performance of the current RAM modules, especially the processor cache. However, the data in RAM stays there only while the computer is running; when the computer is shut off, RAM loses its data.
For this reason, RAM is typically used along with nonvolatile memory, which does not lose its data when the computer's power is turned off or the storage device is disconnected from a power source. Nonvolatile memory also does not need to have its memory content periodically refreshed like some volatile memory. In addition, nonvolatile storage is cheaper and can hold much more data. Even so, today's computers require the fastest memory and cache possible, which means sticking with volatile memory until a better technology comes along.
Most of today's computers use dynamic RAM (DRAM) for the main memory and static RAM (SRAM) for processor cache. DRAM supports greater densities than SRAM, and it is cheaper. However, DRAM also requires more power and does not perform as well as SRAM. One of the biggest challenges with DRAM is that the capacitors used for storing the data tend to leak electrons and lose their charge. This means that DRAM memory devices need to be refreshed periodically to retain their data, which can affect access speeds and increase power usage.
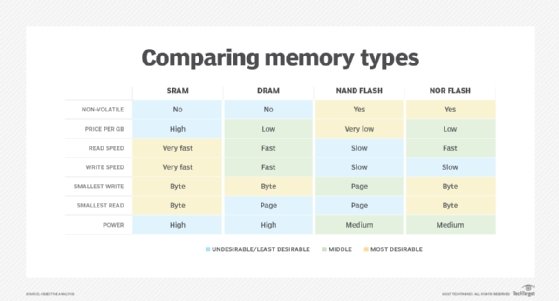
Because of the differences between DRAM and SRAM, DRAM is better suited for main memory and SRAM is better suited for processor cache. SRAM requires more space to store the same amount of data as DRAM. The cache is smaller than the main memory, so SRAM's lower density is not as much of an issue, nor is the higher price tag.
The cache also requires the best possible performance, which again makes SRAM a more natural fit. On the other hand, DRAM can store more data in a given space and it is cheaper, so it is more appropriate for the main memory, which needs to hold much more data but doesn't have the same performance requirements as the cache.
See also: NVMe, NVRAM, MRAM, computer hardware, storage medium
