x86-64
What is x86-64?
x86-64 (also called x86_64, x64, or amd64) is the 64-bit CPU architecture that is used in Intel and AMD processors. It is an extension to the 32-bit x86 (i386) architecture.
The x86-64 architecture is used in most CPUs for home computers and servers in use today. It is incompatible with the ARM64 architecture, which is in use in smartphones, Apple computers and some servers.
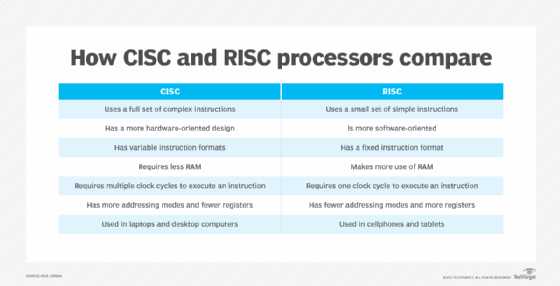
x86-64 is designed with a complex instruction set computing (CISC) approach. CISC seeks to have many different instructions and to perform complex procedures in only a single instruction.
History of x86
The x86 architecture was released by Intel in 1978. It was first released as a 16-bit architecture. It was called "x86" because the last two digits in the names of early processors that used it ended in "86." In 1985 it was expanded to be a 32-bit architecture, and x86 is now commonly associated with the 32-bit form. Since it only supported 32-bit address mapping natively, it was limited to 4 gigabytes (GB) of directly accessible memory. This limitation was becoming a major bottleneck in the late 1990s, especially for workstations and servers.
AMD developed the x86-64 architecture design and instruction set in 1999. The first commercially available CPU capable of using it was released in 2003. It was designed as a simple 64-bit extension to the existing x86 instruction set. This let it keep full compatibility with existing operating systems and software without any changes or performance impact. Since this version was developed by AMD, it is called amd64 in some technical sources.
About this time, Intel had released a competing 64-bit architecture called Itanium (IA-64) which was incompatible with x86. It could use emulation to run x86 programs, but this emulation was very slow. Itanium was not widely adopted. Intel released an x86-64 CPU in 2004 and eventually dropped Itanium.
Intel and AMD currently have cross licensing deals between x86 and x86-64. This lets them use the other's patented technologies.
Windows 11 and recent versions of Windows 10 have dropped support for 32-bit processors.
How x86-64 works
The x86-64 instruction set is a 64-bit architecture. This means that the CPU's registers, instructions, memory addresses and operands (numbers to be worked with) are all 64-bits long.
A 64-bit CPU could theoretically access up to 16 exabytes of memory address space. Since this is far more than is needed by any system, most current implementations usually limit the physical memory addresses to 48-bits, or 256 terabytes of RAM.
The system virtual memory is similarly limited to 48-bits in many implementations. Newer Intel and AMD processors (Ice Lake or newer) support Level-5 paging, which raises this to 57-bits, or 128 petabytes.
To keep 64-bit memory addresses coherent and to support the limited addressing space, the most significant 16 bits must be the same. This results in two chunks of usable memory space. The lower half goes from 0000000000000000 to 00007FFFFFFFFFFF and the upper half from FFFF800000000000 to FFFFFFFFFFFFFFFF. This is known as canonical addressing. Many operating systems reserve the higher half for protected system or kernel memory and the lower half for user or program use.
The x86-64 architecture also includes a no-execute bit in the memory page table. This lets the system set a memory region as read only. If a program were to try and execute program code from a no-execute region, it would raise an exception. This can help to prevent buffer overrun attacks.
Most x86-64 CPUs include optional advanced instructions to optimize for certain tasks. Some examples of these are sever-sent event and Advanced Vector Extensions for vector operations and Advanced Encryption Standard"for cryptographic operations.

X86-64 vs. ARM64
The ARM64 architecture, also known as AArch64, is used by Arm processors. It is the 64-bit version that extended the older 32-bit arm architecture (AArch32). ARM64 is a reduced instruction set computing design. RISC design seeks to have a few instructions that only do one thing at a time. This greatly reduces the complexity of the chip compared to CISC designs, such as x86-64.
Historically, ARM64 CPUs have been optimized for power and space efficiency, while x86-64 CPUs are optimized for performance.
Modern ARM64 and x86-64 implementations have largely converged in performance and are limited by similar factors. They are mainly performance limited by elements such as memory cache and branch prediction. This means that CPU performance is more influenced by implementation specifics than architecture. Factors such as transistor node size, cache size and power targets should be considered when selecting a processor architecture for a specific application.
X86s and backwards compatibility
The x86-64 architecture is backwards compatible all the way back to original 16-bit processors. This mode is still used when the computer boots and is then not used again at all during normal operation. Intel has recently proposed the x86s architecture, which removes these legacy modes, resulting in a simpler design.
The terms CPU and microprocessor are used interchangeably, and while they both execute similar computer tasks, their functions differ slightly. Learn how CPUs and microprocessors differ. Also, see how see how CPUs, GPUs and DPUs differ from one another.
