memory dump
What is a memory dump?
A memory dump is the process of taking all information content in RAM and writing it to a storage drive as a memory dump file (*.DMP format).
Why is a memory dump important and who uses it?
Developers commonly use memory dumps (also called core dumps) to gather diagnostic information at the time of a crash to help them troubleshoot issues and learn more about the Event. Information gathered from the memory dump can help developers fix errors in operating systems and other programs of all kinds.
From a forensic perspective, a memory dump, whether a mini-dump (portion of memory) or a complete memory dump, is invaluable as it provides data on the most recent state of the system and its activities before a system crash.
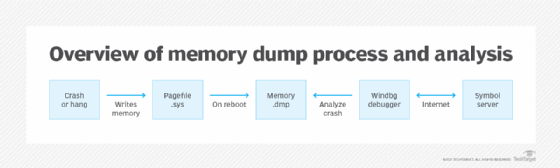
Data from a memory dump can include details on memory contents and system states, which can be used to diagnose the immediate problem and possibly additional issues (e.g., security breaches or malware) that might have been unknown before the crash occurred. Typically, the system will be unavailable after a memory dump, but can return to operation after a restart.
Some computer errors are unrecoverable because they require a reboot to regain functionality, but the information stored in RAM at the time of a crash contains the code that produced the error. Memory dumps save data that might otherwise be lost to RAM's volatile nature or overwriting.
What is the blue screen of death?
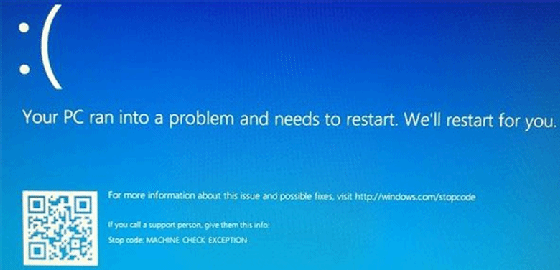
One of the most disturbing events related to computer operations is a crash that results in the display of a blue screen with (hopefully) details on restarting the system. This is called the blue screen of death (BSOD) error display that is generated by Microsoft operating systems.
The errors display some basic suggestions, information and a faulting module while the percentage of the memory written to storage counts up. Following reboot, the memory dump can be sent to Microsoft for analysis to help the company fix the issue in updates and learn how their products are being used.
What risks can occur from memory dumps?
Because memory dumps can include anything in the computer's active RAM, some users have privacy concerns. Furthermore, because the dump files are stored on a drive, they might also present security risks.
If savvy hackers get their hands on a memory dump, they can potentially find cleartext passwords or decryption keys that normally would not be easily accessible. Operating systems from Microsoft and other vendors allow for memory dumps that contain less information, and some make it possible to turn off memory dumps.
Learn how to troubleshoot the most common issues with Windows 11.
