Automated Clearing House fraud (ACH fraud)
What is Automated Clearing House fraud (ACH fraud)?
ACH fraud is the theft of funds through the US Department of the Treasury's Automated Clearing House financial transaction network. The ACH network acts as the central clearing facility for all electronic fund transfer (EFT) transactions in the United States, representing a crucial link in the national banking system.
The ACH is a program of the Treasury Department's Bureau of the Fiscal Service. This system, established in the mid-1970s facilitates online payments and electronic funds deposits for financial institutions.
In the U.S., financial institutions, government agencies, businesses, and the general public use the ACH as the primary system for EFTs such as direct deposit payments for payrolls. Electronic-only payment processors, including PayPal and Venmo, also use the ACH to facilitate payments.
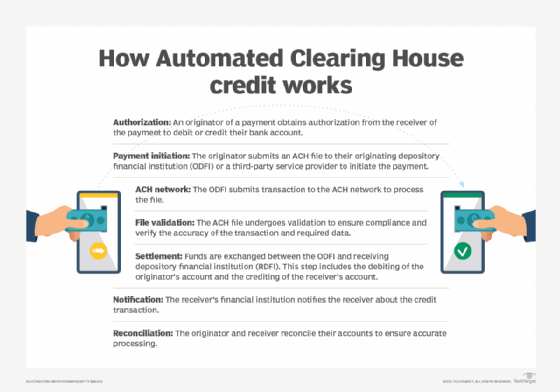
Steps used by the ACH to process and validate financial transactions generally include the following:
- Authorization. An originator of a payment obtains authorization from the receiver of the payment to debit or credit their bank account.
- Payment initiation. The originator submits an ACH file to their originating depository financial institution (ODFI) or a third-party service provider to initiate the payment.
- ACH network. The ODFI submits transaction to the ACH network to process the file.
- File validation. The ACH file undergoes validation to ensure compliance and verify the accuracy of the transaction and required data.
- Settlement. Funds are exchanged between the ODFI and receiving depository financial institution (RDFI). This step includes the debiting of the originator's account and the crediting of the receiver's account.
- Notification. The receiver's financial institution notifies the receiver about the credit transaction.
- Reconciliation. The originator and receiver reconcile their accounts to ensure accurate processing.
Cybercriminals have found ways to steal funds through the ACH network, perpetrating ACH fraud. If they can obtain a victim's bank account (checking or savings account) number and a bank routing number (printed on the bottom left corner of checks), they can take unauthorized actions such as the following:
- Transfer money from the victim's account to their own account.
- Buy goods or services using the funds in the victim's account.
- Steal a victim's debit card to make purchases.
Such criminal actions are lumped under the definition of ACH fraud.
Examples of ACH fraud
ACH transactions often involve some element of time delay, which provides criminals a small window to engage in ACH fraud.
Here are a few examples of ACH fraud:
- The criminal accesses a commercial customer's online credentials, generates an ACH file in the originator's name, and quickly withdraws funds (such as payroll money) before the victim discovers the fraud.
- The criminal accesses a retail customer's credentials and sets themself up as an automatic bill pay recipient.
- In an insider threat scenario, an employee of the target company or a bank modifies ACH files to steal money.
- ACH kiting: In a variation on check kiting -- a scam in which funds are juggled back and forth between bank accounts at separate banks -- a criminal moves funds between accounts or financial institutions and then withdraws all the funds before the theft can be detected by the victim (usually a large organization) or the banks.
- In a spear phishing scam, an employee with authorization for ACH transactions receives an email that leads him to an infected site, which, in turn, installs a keylogger to access authentication information. The thief can then impersonate the company's authorized representative and withdraw funds.
- The perpetrator uses Authorized Push Payments to trick account holders into making ACH transactions, resulting in a payment to the perpetrator's own bank account.
- The thief can submit an ACH transaction using a customer's credentials and then withdraw funds from that customer's account via ACH debit.
The impact of ACH fraud
While ACH fraud can impact anyone making EFTs (i.e., using the ACH network), the impact of such events on businesses and financial institutions is much larger than it is on individuals.
If a receiving bank is the victim of multiple incidents of ACH fraud, its fraud losses can add up quickly. This is because receiving institutions are held financially liable for chargebacks if they allow their customers to use the received funds before they are completely cleared.
The institution sending an ACH transaction can also suffer financially in the event of ACH fraud. If they allowed a transaction to leave a customer's account even though the customer did not authorize the transaction, which represents an unauthorized transaction, and they might be required to compensate the customer for the loss of funds.
In addition to financial losses, the institution might suffer reputational damage, which can affect its existing customer relationships. The bank might also find it harder to attract new business if it suffers a large-scale ACH fraud scam.
Companies that experience ACH fraud might have to pay regulatory fines due to compliance violations. Depending on the scale of the fraud, they might also find themselves on the wrong end of a legal battle with affected customers.
How can companies prevent ACH fraud?
The frequency and scale of ACH fraud scams are on the rise. Considering the potential impact of even a single such event, businesses and financial institutions must take steps to protect themselves from ACH fraud.
It's crucial to keep an eye on account balances and reconcile accounts frequently.
Other important practices that can help to prevent ACH fraud include:
- Use strong passwords and change them often.
- Restrict access to any computer used for ACH transactions.
- Ensure that firewalls and antivirus software are up to date.
- Implement multifactor authentication (MFA) to provide an additional layer of security to devices and to ensure that the person initiating an ACH transaction is who they claim to be (the customer or other authorized party).
- Encourage customers to create a list of allowed regular authorized transactions.
- Implement ACH filters so customers can allow ACH transactions only from the parties they authorize, thus protecting their funds from ACH fraud.
- Encrypt all sensitive data, including customer credentials.
Organizations can also block unauthorized transfers from a customer's account and use secure application programming interfaces (APIs) to detect fraud. Additionally, they can implement behavioral or biometric analytics systems that differentiate between expected and unexpected (e.g., fraudulent or malicious) account behaviors. Both technologies enable institutions to mitigate risk as soon as it arises (in near real time) and minimize instances of ACH fraud.
Increasingly, many institutions also implement fraud detection solutions, including those powered by artificial intelligence (AI) and machine learning that verify identities, screen payments, and monitor transaction data. These solutions provide added protection that helps mitigate ACH fraud risk and protects the institution and its customers from losses.
Learn about the future of cybersecurity and why companies should use AI for fraud management and detection. Read about 13 common types of cyber attacks and how to prevent them.
