What is social media?
Social media refers to websites and applications that focus on communication, community-based input, interaction, content-sharing and collaboration.
Over the past decade, social media has evolved beyond just a tool for connecting with friends and family. It now serves as a platform for news dissemination, entertainment, and even commerce, becoming a significant part of both personal lives and business operations.
People use social media to stay in touch and interact with various communities, follow trends, and stay informed. In the business world, social media serves as a key tool for marketing, product promotion, customer service, and engagement. Businesses use these platforms to communicate with customers and gather feedback.
Today, nearly all business-to-consumer websites have social components, such as comment fields or social sharing buttons, that make engagement easy. Various tools help companies track, measure, and analyze how their brand is perceived across social media platforms.
Mobile applications have significantly expanded the reach of social media, making these platforms accessible anytime, anywhere. Examples of popular platforms include X (formerly Twitter), Facebook, TikTok, Instagram and LinkedIn. Each platform serves its own unique purpose and audience.
What are the business applications of social media?
Businesses use social media to market products, promote their brand and engage with customers. Social platforms facilitate customer feedback and let customers share their positive or negative experiences. This helps businesses react quickly to customer concerns and maintain consumer confidence.
Social media is increasingly being used for crowdsourcing, a practice where companies use social networking platforms to gather ideas, services, or goods from a broader community such as employees, customers, and the public. This can be invaluable for product improvement or development.
Business to business (B2B) applications for social media include the following:
- Social media analytics. Companies gather data from social platforms and blogs to analyze customer sentiment analysis and make business decisions. This data-driven social media analytics approach enables them to adjust strategies in real time.
- Social media marketing (SMM). This increases brand exposure by creating shareable content that spreads organically across networks. SMM often includes social media optimization (SMO), which draws visitors to a website through strategic posts, updates and blogs.
- Social customer relationship management. Businesses use social CRM tools to foster stronger relationships with their audience. A company's social media pages, such as those on Facebook or Instagram, allow followers to connect, which enhances engagement and helps monitor customer sentiment in real-time.
- Recruiting. Social recruiting has become an integral part of many organizations' hiring strategies, leveraging platforms like LinkedIn to reach a broad candidate pool. It allows businesses to quickly identify and engage with potential hires.
- Enterprise social networking. Tools like Slack, Yammer and Microsoft Teams are widely used for internal communication, collaboration and project management, allowing employees to connect and share information. These platforms also enable businesses to gather valuable market research from external social networks.
What are the benefits of social media?
Social media provides several benefits, including the following:
- User visibility. Social platforms let people easily communicate and exchange ideas or content.
- Business and product marketing. Businesses can quickly promote their products or services to a global audience. Many companies now rely on social media to conduct market research and nurture their customer base. In some industries, like entertainment, the content created on social platforms is the product.
- Audience building. Platforms like Instagram, TikTok and YouTube help individuals -- especially entrepreneurs, artists, and creators -- build a following without needing traditional distributors. For instance, a musician can upload their music to a platform, immediately gaining visibility through their network and beyond.
What are the challenges of social media?
Despite its benefits, social media also poses challenges for individuals and businesses:
- Mental health issues. Overuse of social platforms can contribute to mental health concerns like anxiety, depression, and social media addiction. Research shows that constant exposure to curated content can lead to negative self-comparisons and exacerbate feelings of inadequacy.
- Polarization. Social algorithms often create filter bubbles, where users are exposed only to content that aligns with their existing views, leading to increased polarization and limiting exposure to diverse perspectives.
- Disinformation. Social media can be a breeding ground for misinformation and disinformation. The viral nature of these platforms allows false or misleading information to spread quickly, often with malicious intent.
Businesses face similar and unique social media challenges. These include:
- Offensive posts. Employees using enterprise social platforms can sometimes drift into discussions unrelated to work, leading to potentially offensive or divisive conversations.
- Security risks. Traditional data security and retention policies may not cover adequately the features available in collaboration tools, increasing security risks and compliance concerns.
- Productivity issues. The constant influx of social notifications can become a distraction and hamper employee productivity.
What are enterprise social media best practices?
It's essential for businesses to create a clear social media strategy and set measurable goals to build trust, increase brand awareness and engage with customers. Social media best practices include the following:
- Establishing social media policies. Businesses should create policies that guide employee behavior on social platforms, ensuring no legal or reputational risks arise from inappropriate posts.
- Focusing on the right platforms. Companies should prioritize platforms that best serve their audience. For example, LinkedIn and X are well-suited for B2B marketing.
- Creating engaging content. Rich media like videos, images, and infographics tend to perform better on social platforms. It's important to post content that resonates with users and encourages interaction.
- Using analytics tools. Tracking engagement and staying on top of trends helps businesses adjust their strategies and ensure their social media campaigns are successful.
- Promoting authentic conversations. Social media should reflect the brand's voice while remaining professional. Businesses should engage customers and employees, celebrating positive interactions.
- Checking analytics frequently. Consistent monitoring ensures businesses stay ahead of potential issues and can measure the success of campaigns.
What are the different types of social media?
The four main categories of social platforms are:
- Social networks. These focus on connecting individuals with shared interests. Examples include Facebook and LinkedIn.
- Media-sharing networks. These platforms center around sharing visual content like photos or videos. Examples include YouTube, Instagram and TikTok.
- Community-based networks. These encourage in-depth discussions on specific topics. Reddit is an example.
- Review networks. These focus on reviewing products or services. Examples include Yelp and TripAdvisor.
What are examples of social media?
Here are some examples of popular web-based social media platforms:
- Facebook: A widely-used social networking site where users can create profiles, share content, and communicate with friends and family.
- LinkedIn: A platform designed for professional networking where users can connect and share business-related information.
- Pinterest: A social curation platform where users can share and categorize images.
- Reddit: A discussion-based platform where users engage in conversations around specific topics.
- X: A microblogging platform where users post short updates or "tweets."
- Wikipedia: A collaborative platform where users contribute and edit content in an open-source encyclopedia.
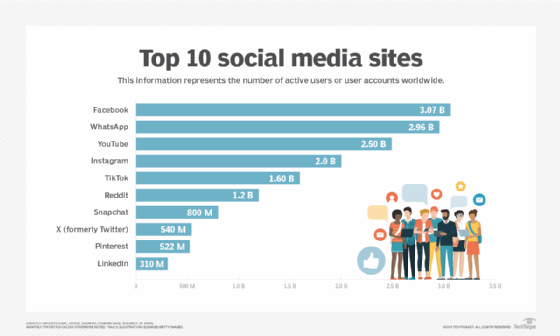
Social media has become an indispensable tool for both individuals and businesses. For organizations, a well-executed social media strategy can enhance brand visibility, foster customer relationships, and build a strong reputation. By understanding the unique functions of each platform and staying informed on best practices, businesses can effectively navigate the evolving social media landscape.
Social media has evolved into a critical part of modern culture worldwide. Learn about the history and evolution of social media.