industrial control system (ICS)
What is an industrial control system (ICS)?
In industrial settings, industrial control system (ICS) is a term used to describe the integration of hardware and software with network connectivity to support production processes in manufacturing or critical infrastructure.
ICS is a general term for any system used to control and manage industrial processes, including manufacturing, production and distribution. As the brain of a factory or plant, an ICS facilitates human-machine interactions.
Most ICSes include different types of components -- devices, controls, networks, etc. -- that work together to achieve a specific objective. A manufacturing ICS may consist of electrical, mechanical and pneumatic components to control product handling and production, while a chemical plant's ICS may consist of electrical, mechanical and hydraulic components to transport material or energy.
What are the common types of industrial control systems?
The following are three of the most common types of ICS.
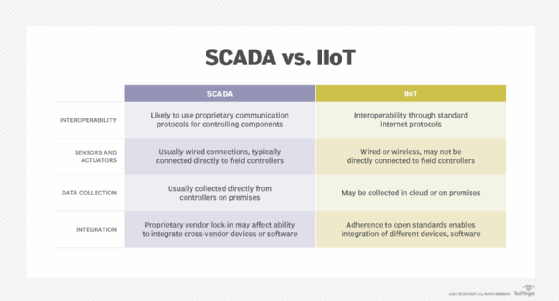
Supervisory control and data acquisition
Supervisory control and data acquisition (SCADA) provides a centralized control system that facilitates the long-distance monitoring and control of field sites in settings like electrical power distribution, water treatment and pipeline monitoring. SCADA systems include components like programmable logic controllers (PLCs) and human-machine interfaces (HMI).
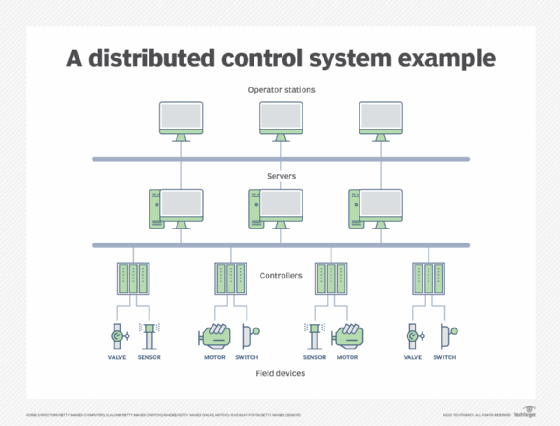
Distributed control systems
A distributed control system (DCS) is used to control multiple local production systems -- devices and controllers -- using a centralized supervisory control loop. The loop also enables plant managers to access production and operation data for analysis or decision-making. These systems are common in oil refineries, chemical manufacturing and water treatment facilities.
Industrial automation and control systems
An industrial automation and control system (IACS) can automatically control production levels based on real-time data. This data is automatically collected from an organization's sales or distribution channels. Like SCADA and DCS, an IACS combines hardware, software and communication systems that together help to convert data into actionable information. An IACS integrates a plant's devices, machines and equipment and also connects these elements with other parts of the organization, such as its compliance processes, supply chain, and research and development department.
Industrial control system components
Many ICS environments are a hybrid of DCS and SCADA. These systems typically include the following:
- Programmable automation controllers. PACs are programmable computers that incorporate higher-level instructions and execute embedded programs to control electromechanical processes and factory machinery.
- PLCs. PLCs are small computers used in DCS and SCADA to control the system's functions using its internal logic and to automate certain processes.
- HMIs. PLCs and other SCADA components are integrated with HMIs for centralized monitoring and control of the inputs and outputs of different processes. HMIs are usually graphical user interfaces that let human operators interact with hardware.
- Remote terminal units. RTUs are microprocessor-based field devices that connect hardware to a DCS or SCADA and send sensor information to the master terminal unit.
- Control servers. They communicate with lower-level control devices over the ICS network and host the DCS or PLC supervisory control software.
- Intelligent electronic devices. Used in SCADA and DCS to acquire data, IEDs communicate with other devices and implement local processing and control activities.
- Control loops. They consist of hardware such as PLCs and actuators, and they interpret signals from sensors and other devices, as well as transmit the information to the controller to execute a certain task or process.
- Sensors. Sensors measure certain variables and generate signals sent to the ICS controller to execute some task.
- Data historians. Data historians log all process information in a centralized database to facilitate analysis, process control, planning and decision-making.
Where are industrial control systems used
Industrial control systems are used in almost all industrial sectors, including the following:
- Manufacturing.
- Chemical processing or production.
- Oil processing.
- Telecommunications.
- Food and beverage production.
- Automotive.
- Pharmaceuticals.
ICSes also support a nation's critical infrastructure, such as its electrical grids, public transportation, and water treatment, energy and public communication systems.
All ICSes are built to electronically or automatically execute and manage their assigned tasks. The specific function of each ICS depends on its configuration, purpose and industrial application area.
Evolution of industrial control systems
Historically, most machinery and engineering components used in manufacturing and the operation of power plants, water and wastewater plants, transport industries and other critical infrastructures were "dumb." Those that were computerized typically used proprietary protocols. Also, the networks they belonged to were air-gapped and protected from the outside world.
This has changed, and components of today's ICSes are often connected directly or indirectly to the internet. This enables the various components to communicate with each other and with other systems not part of the local network. Early ICSes offered only localized control and rarely provided an overall view or control over an entire manufacturing system.
More recently, ICSes that offer centralized control or distributed control emerged. The former uses a centralized control room that provides an overview of the entire system. The latter harnesses computerized and autonomous controls distributed throughout the system to localize control functions near the machines, while enabling remote monitoring and supervisory control.
Today, ICSes are complex, powerful systems indispensable to plant operations in all kinds of industries. More and more are part of the internet of things (IoT), which improves their usability, efficiency, productivity and speed.
Industrial control systems, information technology and operational technology
Advances in smart sensor technology and wireless networking have made the blending of operational technology (OT) with information technology (IT) desirable and cost-effective. This IT/OT convergence enables industrial organizations to get better visibility into and control over their supply chain. It also enhances system functionality and boosts overall productivity. It offers benefits like increased speed, better responsiveness to changing conditions and improved reliability.
Despite these benefits, there is one serious drawback of IT/OT convergence: security risks.
Industrial control systems security
IT/OT convergence creates numerous opportunities for threat actors to attack and compromise ICSes. They can exploit vulnerabilities in one or more internet-connected devices to gain direct access to them and compromise one or more processes. They may also execute phishing attacks and ransomware attacks or move laterally within the network to establish a long-term presence in it, making it possible to steal data or spy on the organization.
Targeted attacks against ICSes, particularly critical infrastructure ICSes, pose a threat to most nations around the world. As remote telemetry units used to input change become more capable of local control and as IoT and industrial IoT grow, it becomes increasingly important to protect ICSes from security threats.
In the United States, the Department of Homeland Security offers these recommendations to protect ICSes:
- Use application whitelisting to protect infrastructure from potentially harmful programming.
- Implement configuration management and patch management controls to keep control systems secure.
- Reduce attack surface areas by segmenting networks into logical parts and restricting host-to-host communications paths.
- Require multifactor authentication, and enforce the principle of least privilege.
- Require remote access to be operator-controlled and time-limited.
- Monitor traffic in the control network and on ICS perimeters.
- Analyze access logs, and evaluate all anomalies.
- Ensure that golden records are retained so systems can be rolled back to their last known-good state.
Unique and common cybersecurity threats and challenges target industrial control systems. Learn about the top ones here and how to mitigate them by exploring the top 10 ICS cybersecurity threats and challenges.
