What is tailgating (piggybacking)?
Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while avoiding detection by an electronic or human access control (or alarm) system.
In general, when tailgating attacks succeed, it's due to a combination of two factors: 1) human carelessness on the part of the followed party, and 2) ingenuity and confidence on the part of the following party. Tailgating is a significant security risk for organizations and their property, equipment, data and personnel.
Understanding tailgating
Tailgating is one of the simplest forms of a social engineering attack, in which threat actors take advantage of human habits or weaknesses to perpetrate a malicious incident, such as a scam, theft or a cyberattack.
By simply following an authorized person (AP); an unauthorized party (UP) can easily get around security mechanisms, such as retina scanners, fingerprint scanners, and even human security guards, and gain access to restricted physical areas.
Often, unauthorized persons are able to do so by taking take advantage of cognitive biases that affect human decision-making. One such "human bug" is the tendency to be courteous; another is the tendency to trust other people; a third is simple habit. Due to these human quirks, many APs tend to hold the door for UPs, who then might exploit such polite gestures to access locations they might not have been able to access otherwise.
How tailgating happens
Tailgating attacks can happen in many ways, including the following:
- The simplest method is someone following someone else through a door.
- Tailgating can also occur when an authorized person enters an area without closing the door behind them. This can leave a small window of time available for an unauthorized person to enter the premises.
- Another method is when an AP keeps a door propped open for some reason. For instance, a painter might leave it open to get rid of paint fumes, or an IT vendor might be troubleshooting a server or router in the server room while leaving the room's door open.
- A more sophisticated type of attack occurs when threat actors disguise themselves, either as authorized personnel with access to a particular area (e.g., a manager) or seemingly harmless persons (e.g., a delivery person) to trick people into granting them access to that area.

Where does tailgating happen?
Tailgating is a common problem in multitenant buildings with high traffic (many people accessing the building and its premises). High traffic makes it difficult to identify and track unauthorized personnel, and to keep them out.
Tailgating also happens more often in companies where employees lack good cybersecurity hygiene or don't follow cybersecurity best practices. This might be due to the following:
- Carelessness.
- Lack of awareness about cyber risks.
- Inadequate cybersecurity training, particularly training about how humans are often the "weak link" in cybersecurity.
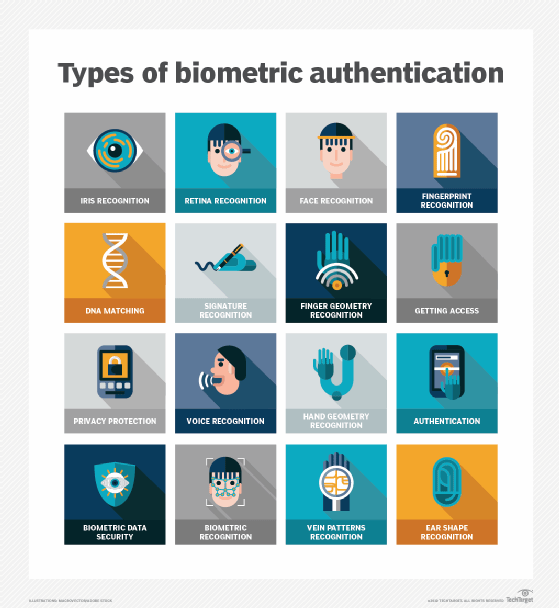
Tailgating can also happen in firms lacking biometric access control systems. Without such electronic systems in place, almost anybody can enter secure areas by simply walking in. It's also difficult to identify blind spots in a facility or plan strategies to address them.
Dangers of tailgating
Tailgating is considered a "low-tech" attack tactic because it rarely involves sophisticated equipment. Nonetheless, it is a serious physical and cybersecurity concern for enterprises because it increases the risk of a malicious person compromising or harming the firm in some way. For example, an intruder might do the following:
- Exfiltrate sensitive information to cause a data breach.
- Steal valuable equipment such as unattended laptops.
- Insert spyware into enterprise devices.
- Install malware or ransomware on computers.
- Turn off critical systems such as servers.
- Access the server room and create a backdoor to the entire enterprise network.
- Install cameras to remotely keep an eye on company operations and engage in corporate or cyberespionage.
- Steal money or business secrets like blueprints, intellectual property (IP), client lists or financial information.
- Destroy or damage the firm's physical property (vandalism).
Tailgaters can include disgruntled former employees, thieves, vandals or mischief makers. Basically, anyone who has an issue with the company or hopes to profit off it can be a tailgater. Whether tailgating persons are innocent or malicious, they can potentially disrupt the business, cause damage or create unexpected costs. They might also create further safety issues for company personnel due to fires or stampedes. Tailgating also can lead to physical violence.
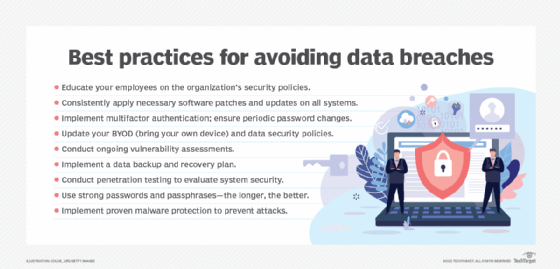
How to avoid tailgating
Organizations can protect their premises from unauthorized personnel and prevent tailgating by implementing certain effective security measures. These include the following:
Electronic access doors
Installing access controls for entrances and restricted areas with swiftly closing doors is vital to prevent tailgating. Additionally, revolving doors provide tailgating detection and ensure that an individual is alone, preventing others from entering behind them without going through a proper access mechanism.
Laser sensors or mantraps
Photosensors, laser sensors and mantraps can limit entry to a single person at a time, preventing someone from following an authorized person and entering an area they are not authorized to enter.
Biometric scanners
Biometric scanners and turnstiles allow only one person to enter an area at a time, preventing tailgaters from walking with or behind an authorized person. Also, biometric systems store specific individuals' data (e.g., fingerprints, palm prints, retinal scans, etc.) to facilitate access to specific areas, so individuals whose information is not stored in the security system are automatically kept out of those areas.
Smart cards
Smart cards are usually customized for use by a single person, which helps to control access to a room, office or building. When implemented with electronic access control mechanisms, smart cards can prevent tailgating in entrances and restricted areas.
Photo ID
Employees must be required to wear photo IDs and visitors must be provided temporary badges and required to wear them as long as they are within the organization's premises. All IDs must be clearly visible. With these ID methods in place, anyone not wearing one becomes conspicuous, making it easier to recognize and detain them, and prevent them from entering secure premises.
Video surveillance
Surveillance devices such as CCTVs provide a means to keep an eye on the premises 24/7. If the devices are clearly visible, they act as a deterrent to those looking to tailgate their way into an office or server room. Now, AI-enabled video surveillance systems are available to provide uninterrupted views of secure areas plus real-time insights that enable security staff to identify unauthorized or malicious parties and take fast remedial action.
Multifactor authentication (MFA)
MFA on access doors requires users to provide more than one credential to access an area. In this way, even if an unauthorized individual manages to compromise one credential, they will still not be able to gain access. One example of MFA is requiring individuals to provide both an access card and a thumb print. Another is requiring entrants to enter numbers on a keypad and provide a retina print. MFA is particularly useful to keep unauthorized persons from accessing secure areas like server rooms or file rooms.
Human security guards
Security guards provide a physical means to safeguard premises. These guards should be trained to ask unfamiliar personnel or personnel not wearing ID cards who they are and why they are on the premises. They also should be authorized to detain these persons in a holding room until management can determine what further action (e.g., a police report) is needed against them.
The importance of employee education in preventing tailgating
The above security measures are all crucial to curtail tailgating. However, their presence can create a false sense of security among staff, leading to carelessness or ignorance of employees' role in preventing tailgating. That's why it is vital to educate them on the following:
- The dangers of tailgating.
- How to recognize tailgating attempts.
- What they can do to resist tailgating and to keep tailgaters out.
It's also important to create a strong cyber awareness culture throughout the organization and to make employees aware of their responsibilities to protect the company's assets from unauthorized parties. Employees should also be taught to follow these security best practices:
- Never hold the door for anyone.
- Always keep doors closed, especially those to secure or restricted areas like server rooms.
- Stop people from following them into special access zones or restricted areas, especially if they are not wearing employee or visitor badges.
- Ensure that any outsiders, such as repairmen or delivery persons, are legitimate and wearing appropriate visitor badges.
- Direct unfamiliar people, people without badges or people who appear "lost" to the reception desk.
- Never allow former employees to access the company premises if they don't have the permission of authorized personnel (e.g., IT team) or are not wearing proper ID badges.
- Report suspicious activity to security guards.
- Inform security guards or the IT team if an electronic door is not functioning properly.
Tailgating vs. piggybacking
Tailgating is not the same as piggybacking, a type of breach in which the unauthorized individual tricks or convinces the authorized individual into letting them into a secure area. Thus, piggybacking usually involves an AP's knowledge, consent or permission. Also, the AP providing access to the UP usually assumes that the UP has a legitimate reason for requesting access.
That said, both tailgating and piggybacking are forms of in-person social engineering attacks in which threat actors try to gain access to an area that would be off-limits to them, usually for nefarious or malicious purposes. Both can be very damaging for an organization in a multitude of ways.
Organizations should know the key signs of common security incidents and how to respond to keep systems and data safe. Read about the types of security incidents and how to prevent them.
