What is social networking and how does it work?
Social networks are websites and apps that allow users and organizations to connect, communicate, share information and form relationships. People can connect with families, friends, others in the same area, and those with the same interests.
Social networks have evolved into one of the most important uses of the internet today and play a critical role in modern life, facilitating social interaction as well as business, education, and entertainment.
Popular social networking sites, such as Facebook, X (formerly Twitter), Instagram, LinkedIn and TikTok, help individuals maintain social connections, stay informed and access or share information. These platforms have become indispensable tools for marketers to reach their target audiences with tailored content and advertising.
Since the launch of the first social networking site, SixDegrees.com, in 1997, social network adoption has grown exponentially. By January 2023, more than 4.76 billion people worldwide were using social networks, according to DataReportal statistics. The number of social network users continues to grow, highlighting the increasing importance of these platforms in our daily lives.
How does social networking work?
Social networking refers to forming connections in person or online. In today's digital era, it primarily refers to online interactions on the internet. Social networking sites let people connect with others across the globe whom they might never have met in person. Users typically access social networking sites on their computers, tablets, or smartphones.
Most social networking sites rely on complex back-end systems that use databases, algorithms, and programming languages (e.g., Python, Ruby on Rails) to organize, store and retrieve data for seamless user experiences. For example, platforms like Tumblr leverage Google Analytics and Google Workspace to enhance daily operations.
What are social networks?
While social networks are diverse in their purposes, operations and other traits, most share several common characteristics:
- User-generated content. Social networks focus on the content users create. With user-generated content, people can post updates, photos or videos that others can view, like, share or comment on.
- Profiles. Users or organizations create profiles with personal information and content they've shared. Most profiles are linked to real names, but some platforms allow anonymity.
- Connections. Social networks let users form relationships by following, friending or connecting with other users. Algorithms often suggest new connections based on shared interests or mutual friends.
It's important to differentiate between social networks and social media. Social networking refers to fostering relationships and connections while social media emphasizes broadcasting content to a broader audience, similar to traditional mass media.
What is the purpose of social networking?
Social networking serves several key purposes:
- Sharing. Social networks allow geographically dispersed friends and families to stay connected by sharing updates, photos and videos.
- Learning. Users can receive real-time news, explore trending topics and keep up with community developments.
- Interacting. Online platforms break time and distance barriers through real-time communication via text, audio or video chat (e.g., WhatsApp, Instagram Live).
- Marketing. Businesses use social networks to build brand awareness, retain customers, and promote products or services.
What are the different types of social networking?
There are various categories of social networking sites, each with a unique focus:
- Social connections. These networks allow people to stay connected with friends, family and acquaintances. Examples include Facebook and Instagram.
- Professional connections. These platforms, such as LinkedIn and Microsoft Viva, facilitate networking among professionals and help businesses recruit talent.
- Multimedia sharing. Platforms like YouTube and TikTok focus on sharing videos and other media content.
- News or information. These platforms let users share and discuss news or how-to information. Examples include Reddit and Stack Overflow.
- Communication. Platforms like WhatsApp,Snapchat and WeChat enable one-to-one or group communication with a focus on chat and messaging.
- Education. Platforms like Google Classroom and LinkedIn Learning offer tools for remote learning and collaboration.
What are the advantages and disadvantages of social networking?
Social networking provides significant social benefits, yet it can also make people more vulnerable to the spread of misinformation, as well as privacy and security threats. Here is a summary of the pros and cons:
Benefits
- Brand awareness. Companies can use social networking to reach potential customers and promote their products or services.
- Global reach. Social networking erases physical boundaries, allowing for instant communication.
- Audience development. Businesses and individuals can grow global followings.
- More website traffic. Companies can use social networking to drive traffic to their websites through shared links and content.
Disadvantages
- Misinformation. False information can spread quickly, causing confusion and uncertainty or worse, leading people to act on incorrect or biased ideas or data.
- Impact of negative reviews. Users can be quick to criticize a company or its products and services, whether their complaints are fair or even real. A single negative review on a large platform can damage a company's reputation.
- Data privacy and security. Social networks are vulnerable to data breaches that can expose user information.
- Burdensome time requirements. Creating and managing social media content demands considerable time and effort, particularly for small businesses.
Social networks in business
Social networking provides businesses with unprecedented opportunities to engage with customers, gather feedback, and conduct market research. Globally, the average person spends over two hours daily on social media, making it a valuable tool for marketing and customer engagement.
Social networks have transformed into highly profitable businesses. Meta Platforms Inc. (formerly Facebook) has a market capitalization of nearly $300 billion, generating most of its revenue from targeted advertising. Businesses use social networks to target specific audiences with advertisements based on their browsing habits, likes and connections.
Many organizations are also developing internal social networks for employees to foster engagement and collaboration. These networks are becoming crucial for teams working remotely or across geographically dispersed locations.
Examples of social networking platforms
Virtually all established organizations advertise on social networking these days. Here are four examples of social networking websites:
- Yelp. A social network where users review restaurants, salons and other businesses based on their personal experiences.
- Pinterest. A bookmarking platform where users can curate and organize photos and links on specific topics of interest.
- Rover. A social network for pet owners, enabling them to connect with pet sitters and dog walkers.
- Airbnb. A social network for travelers, allowing users to book stays in unique properties worldwide.
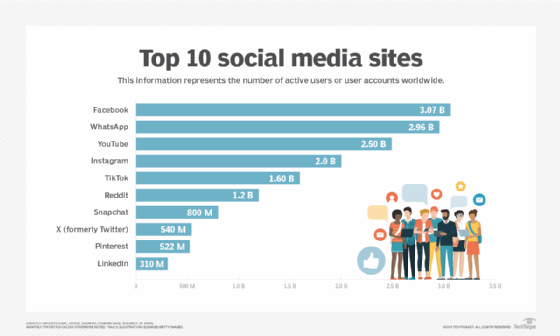
What are the top 10 social networking sites?
While there are countless social networking platforms, the most popular as of 2024 include the following:
- Facebook (Meta) -- 3.07 billion users. Facebook users create profiles, share information, send messages and post status updates on their walls.
- WhatsApp -- 2.96 billion global users. This free instant messaging app lets users send text messages, make video and voice calls, and share documents.
- YouTube -- 2.5 billion monthly active users. This popular video-sharing website enables users to share, upload and post videos and vlogs.
- Instagram -- 2 billion monthly active users. This free social media platform supports sharing long- and short-form videos and photos. It is primarily designed for iOS and Android smartphone users, but a desktop version is available.
- TikTok -- 1.6 billion users. This app is used for sharing and making personalized short videos. TikTok caters to a younger audience and is well known for being a lively, fun-to-use platform.
- Reddit -- 1.2 billion users. Reddit offers forums and subforums (called subreddits) on many topics, including sports, breaking news and technology. Users can comment on each other's posts and share news and content.
- Snapchat -- 800 million daily active users. Users send pictures or videos called snaps to friends. These snaps vanish after they have been viewed.
- X -- 540 million users. This platform lets users share their thoughts and opinions by posting short messages, known as tweets, limited (with some exceptions) to 280 characters.
- Pinterest -- 522 million monthly active users. The site supports saving and organizing links to favorite online resources and destinations through tagging.
- LinkedIn -- 310 million users. This site is oriented to professional networking. It connects users with employers, employees and other professionals.
Controversies in social networks
While used and enjoyed daily by much of the world's population, social networks are also potentially dangerous. Social media addition is becoming common. People can begin to feel a sense of anxiety if they don't check their social media accounts, or they might compulsively refresh them. Social networking posts are also highly curated; people often only post the good things that happen to them. This can cause a warped view of reality where the viewer thinks that others have better lives than they do. This leads to a fear of missing out (FOMO) on social events.
Cyberbullying occurs when someone makes social media posts with the intention of harming someone else. This can take the form of publicly posting the private information of someone or sending abusive messages. Tragically, cyberbullying has led to the suicide of some individuals. It is now a major concern in public schools. Doxing occurs when someone publicly posts someone else's personally identifiable information, such as an address or phone number.
Privacy is a major concern for many social network users. Anything posted can become marketing data companies use for targeted advertising. Private information, such as a person's location or even embarrassing details, can become public. Law enforcement officials can request the use of this information. Additionally, some social networks have confusing privacy settings, causing people to accidentally make information public. Since they store a lot of personal information, social networks are also susceptible to data breaches.
Censorship is another hot topic. Social networks are private companies, so content individuals post isn't necessarily protected by governmental free speech laws, but instead is protected at the discretion of the site's terms of service or administrators. Operators must know and monitor what is allowed on their sites. This can be challenging when it comes to divisive political issues, hate speech and calls to violence. Some say that the sites have a moral responsibility to take a hard stand against all negative speech, while others say that all speech should be allowed and that any content removal is censorship.
Misinformation can spread easily on social networks. Users are encouraged to share the latest news or discuss new topics. This can amplify rumors or hearsay. Users, organizations and even governments can intentionally share false information, sometimes while pretending to be someone else. This has caused some social networks to begin adding fact-check alerts to some posts that might contain misinformation.
Learn ways to spot disinformation on social media and essential social media guidelines for employees. Explore the history and evolution of social media.