The history and evolution of zero-trust security
Before zero-trust security, enterprise insiders were trusted and outsiders weren't. Learn about the history of zero trust and the public and private sector efforts to adopt it.
Zero trust is an approach to enterprise cybersecurity that presumes no connections to corporate networks and systems should be trusted. Instead, zero trust calls for users, devices and systems to be authenticated before first connecting and then be reverified at multiple points before accessing networks, systems and data.
The zero-trust security model is built on the belief that by eliminating implicit trust and implementing strong identity and access management (IAM) controls, organizations can ensure that only authorized individuals, devices and applications can access an organization's systems and data. Implementing zero trust greatly limits the risk of unauthorized access, insider threats and malicious attacks.
More and more organizations are adopting a zero-trust approach, according to "The State of Zero Trust Security 2022" report from IAM software vendor Okta. The report states 55% of respondents said they have a defined zero-trust initiative underway -- a significant jump from 24% in Okta's 2021 report.
From perimeter-based security to zero trust
Zero trust moves enterprise cybersecurity away from perimeter-based security -- an approach that uses firewalls and other technologies to create a perimeter around an organization's IT environment. A perimeter-based approach creates a castle-and-moat security model that extends trust to all users and devices within the perimeter, historically allowing extensive or even unlimited access to all systems within the castle.
Organizations have seen the disintegration of the perimeter over the past two decades, however. With the rise of the commercial internet, cloud computing, mobile communication, IoT and remote-work policies, the number of employees, business partners, devices and applications outside the traditional IT perimeter that need to access applications and systems within the perimeter and vice versa have grown exponentially.
At the same time, bad actors exploit organizations by launching attacks to blend in with the growing volume of traffic. Zero trust is intended to stop such attacks and limit the damage done by eliminating implicit trust and requiring authorized users, devices and systems to prove they are authorized before gaining access.
Zero trust relies on policies, such as the principle of least privilege; IT architecture designs, such as microsegmentation; and technologies including multifactor authentication, user and entity behavior analytics, and endpoint monitoring.
History of zero-trust security: Timeline
Pre-2004: Cracks in the perimeter-based approach
The perimeter-based approach had been the default security posture for decades, until enterprise adoption of cloud computing started to rip down the perimeter during the first two decades of the 21st century. This transition required enterprise security teams to rethink their defensive posture.
2004: Zero trust takes hold
Although the seeds of the zero trust concept existed in the 20th century, the framework really took root in ideas presented in 2004 by the Jericho Forum, an international security consortium. Now part of The Open Group Security Forum, Jericho Forum members saw potential problems with the perimeter defense approach and developed a new concept of security they called deperimeterization. The concept called for multiple levels of security controls, including encryption and data-level authentication.
In a 2004 presentation, Jericho Forum member Paul Simmonds, who is credited with coining the term deperimeterization, ran a banner stating, "So much for the corporate perimeter," noting that "Once upon a time, people were either staff of nonstaff," and "Once upon a time we made no external connections."
He noted in the presentation that "Maybe what we actually need is a new [data security] model." He defined deperimeterization as a concept that involves "a set of solutions within a framework that we can pick and mix from" and calling it defense in depth.
2010: The term 'zero trust' is born
Forrester Research analyst John Kindervag popularized the term zero trust when he presented the idea that an organization should not extend trust to anything inside or outside its perimeters.
2011: Google releases BeyondCorp
Google's BeyondCorp began as an internal initiative in 2009, in response to the Operation Aurora cyber attacks. The goal of BeyondCorp was to enable employees to work remotely without the use of a VPN.
In 2014, Google published an article detailing the initiative, giving the idea of zero trust a significant boost in recognition.
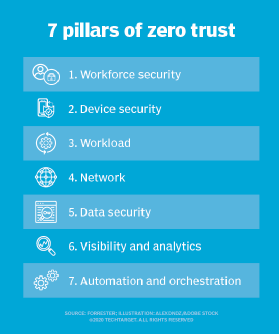
2018: The core pillars of zero trust introduced
Researchers and vendors continued to advance the zero-trust concept and the tools necessary to implement it throughout the past decade.
In 2018, Forrester introduced the concept of the Zero Trust eXtended Ecosystem, which established seven core pillars for zero trust.
Also in 2018, the NIST released SP 800-207, Zero Trust Architecture, which offered guidelines on the core components of zero trust. The documentation was updated in 2020.
2019: ZTNA arrives
In 2019, Gartner introduced the term zero-trust network access (ZTNA) to describe products and services that deliver the zero-trust concept to the network. Gartner also introduced a networking model called Secure Access Service Edge (SASE). ZTNA and SASE both add to the available defense layers now considered part of the zero-trust framework.
2021: Zero trust gains major traction
In Microsoft's 2021 "Zero Trust Adoption Report," 96% of 1,200 security decision-makers who responded said zero trust is critical to their organizations' success. They cited the need for increased security and compliance agility, as well as the need to increase the speed of threat detection and remediation as top drivers for adopting zero trust. The expansion of hybrid work and remote work options that occurred during the COVID-19 pandemic also drove greater adoption of zero trust, according to the report.
2021: White House releases zero-trust strategy
While zero-trust strategies were starting to take hold in the private sector, the federal government introduced efforts to move zero trust security efforts forward in federal government agencies.
May 2021. President Joe Biden issued an Executive Order on Improving the Nation's Cybersecurity aimed at strengthening the overall U.S. cybersecurity posture and, in particular, the country's critical infrastructure cyber defenses. The document also called for the federal government to advance toward zero-trust architecture and laid out specific steps to reach that target.
September 2021. The U.S. Office of Management and Budget (OMB) released a draft strategy for moving the federal government toward zero trust. Some analysts believe the federal government's involvement will put it ahead of the private sector on zero-trust implementations rather than being five years behind.
At the same time, the Cybersecurity and Infrastructure Security Agency (CISA) released its Cloud Security Technical Reference Architecture and Zero Trust Maturity Model for public comment. When announcing the release, CISA explained that as the federal government continues to expand past the traditional network perimeter, it is imperative that agencies implement data protection measures around cloud security and zero trust. CISA's reference architecture is designed to guide agencies' secure migration to the cloud by explaining considerations for shared services, cloud migration and cloud security posture management. CISA's Zero Trust Maturity Model helps agencies develop their zero-trust strategies and implementation plans, and presents ways in which CISA services can support zero-trust options across agencies.
U.S. government agencies followed up the announcements with direct action.
January 2022. OMB released details of its strategy for advancing the federal government's zero-trust journey.
26, 2022. OMB Acting Director Shalanda D. Young in a memorandum alerted executive department and agency heads that the federal zero-trust architecture strategy requires agencies to meet specific cybersecurity standards and objectives by the end of fiscal year 2024 "in order to reinforce the Government's defenses against increasingly sophisticated and persistent threat campaigns." Federal agencies have until the end of September 2024 to meet five zero-trust goals: identity, devices, networks, applications and data.
June 2022. CISA published the second version of its Cloud Security Technical Reference Architecture, which was co-authored by two other federal agencies. CISA noted in an executive summary that the document is intended to support federal entities as they adopt and implement zero-trust architectures.
Such actions, as well as similar efforts to move toward zero trust by other government entities around the world, have put government organizations ahead of private sector entities, according to Okta's "The State of Zero Trust Security 2022." The report found that 72% of government organizations surveyed had a defined zero-trust security initiative or had plans to start one in the coming months, compared to 55% of global nongovernment organizations.
The future of zero trust
In just a decade, zero trust has moved from a concept discussed to shore up security to a widely deployed approach to increase securing organizations around the globe. The 2021 Microsoft report confirms that point, noting that 76% of organizations have at least started implementing a zero-trust strategy, while 35% believe they have fully implemented it.
The percentages of organizations moving toward zero trust will continue to grow. Because zero trust isn't a single product that can be bought from one vendor, many organizations have taken steps that move them toward zero trust. Even if they don't realize it, some are much farther along than they realize.
Yet, security experts agree that most organizations across all sectors have more work to do. Because zero trust involves layers of policies and technologies, advances will be needed in the tools that can be used, along with ways to refine how organizations deploy and use them.
Federal government guidance has prompted state and local governments, as well as universities and critical infrastructure companies, to move to a verify then trust principle.
To help move zero trust forward, some analyst firms and organizations have created zero-trust roadmaps that contain steps for implementation. Many organizations are looking for that kind of guidance to help them understand where they are in the zero-trust process and move them to a full verify-then-trust security posture.







