internet
What is the internet?
The internet, sometimes simply called the net, is a worldwide system of interconnected computer networks and electronic devices that communicate with each other using an established set of protocols.
The internet was conceived by the Advanced Research Projects Agency (ARPA) of the U.S. government in 1969. ARPA was later renamed the Defense Advanced Research Projects Agency (DARPA) in 1972. DARPA's first known packet-switching network was known as the Advanced Research Projects Agency Network (ARPANET). The original goal was to create a network that would let users of a research computer at one university talk to research computers at other universities. A side benefit of ARPANET's design was that because messages could be routed or rerouted in more than one direction, the network could continue to function even if parts of it were destroyed in the event of a military attack or other disaster.
Today, the internet is a public, cooperative and self-sustaining facility accessible to hundreds of millions of people worldwide. It's used by many as the primary source of information consumption and has fueled the creation and growth of its own social ecosystem through social media and content sharing. In addition, e-commerce, or online shopping, has become one of the largest uses of the internet. Millions of users shop for and sell products on the internet using popular e-commerce and marketing platforms, such as Amazon and Shopify.
History of the internet
In 1983, the ARPANET began using the Transmission Control Protocol/Internet Protocol (TCP/IP) open networking protocol suite and in 1985, the National Science Foundation Network designed the network to connect university computer science departments around the U.S.
Communications over the internet greatly improved in 1989 when the Hypertext Transfer Protocol (HTTP) was created, enabling different computer platforms to connect to the same internet sites. In 1993, the Mosaic web browser was created.
The internet continues to grow and evolve. Internet Protocol Version 6, for example, was designed to anticipate enormous future expansion in the number of available IP addresses. In a related development, the internet of things (IoT) is the burgeoning environment in which almost any entity or object can be given a unique identifier (UID) and the ability to transfer data automatically over the internet.

How the internet works
The process of transferring information over the internet from one device to another relies on packet switching. The internet is a packet-routing network that uses IP and TCP protocols for communication. When a person visits a website, their computer or mobile device sends a request to the server over one of these protocols.
The following examines how the process works:
- Every device attempting to access the internet is initially linked either physically through cables or wirelessly. For instance, a computer can establish a physical connection to a modem using an Ethernet cable or connect wirelessly through Wi-Fi or Bluetooth signals.
- Each computer connected to the internet is also assigned a unique IP address that enables the device to be recognized.
- When one device attempts to send a message to another device, the data is sent over the internet in the form of packets and each packet is assigned a port number that will connect it to its endpoint.
- A packet that has both a unique IP address and port number can be translated from alphabetic text into electronic signals by traveling through the layers of the Open Systems Interconnection (OSI) model from the top application layer to the bottom physical layer.
- The message is then sent over the internet where it's received by the internet service provider's (ISP) router.
- The router examines the destination address assigned to each packet and determines where to send it.
- Eventually, the packet reaches the client and travels in reverse from the bottom physical layer of the OSI model to the top application layer. During this process, the routing data -- the port number and IP address -- is stripped from the packet, thus enabling the data to be translated back into alphabetic text and completing the transmission process.
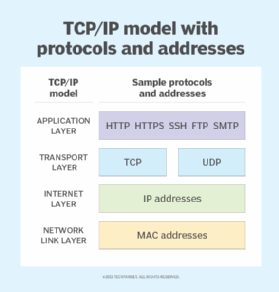
The main components of the internet
The internet is comprised of hardware, software and various protocols. The following are the primary components of the internet:
- Client or endpoint devices. These are the multitude of interconnected components or clients that access and contribute to the internet. These can include computers, smartphones, tablets, routers, web servers and IoT devices.
- Servers. Servers are the computers that provide services or share stored resources with the client devices. Their main job is to comply with client requests by providing the requested information or performing the requested tasks.
- Internet protocols. To retrieve the required data on the internet, a set of guidelines and procedures known as protocols must be adhered to as they guarantee accurate and effective data transmission. Common internet protocols include IP, TCP/IP, HTTP, HTTP Secure (HTTPS) and file transfer protocol. Other protocols, such as Session Initiation Protocol for voice-over IP, Post Office Protocol 3 (POP3) and Internet Message Access Protocol for email are also used.
- IP addresses. IP addresses are used to identify devices on the internet. These can include IPv4 addresses such as 192.168.1.1, which is the default IP address many router manufacturers use to access a router's interface. IPv4 addresses are shorter than IPv6 addresses, which are designed to handle the increasing number of connected devices.
- Routers. Routers forward data packets between computer networks. By using routing tables, routers determine the best routes or paths for data transfer between devices.
- Domain name system. DNS converts human-readable domain names, such as www.example.com, into machine-readable IP addresses. It also acts as a decentralized directory that helps users navigate the internet.
- Web browsers. Web browsers or search engines -- including Apple Safari, Google Chrome, Microsoft Edge and Mozilla Firefox -- let users access and engage with material on the internet and also decipher and present web pages to them.
- ISPs. ISPs are companies that provide users with internet connectivity. They operate the infrastructure, including the cables and routers needed to connect users to the global network.
- Social media platforms. Social media platforms, such as Facebook, X (formerly known as Twitter) and Instagram, let users connect, share content and communicate with people all over the world.
- Firewalls and security measures. Incoming and outgoing network traffic on the internet is monitored and controlled by different types of security firewalls and security measures. Firewalls safeguard networks and devices against unauthorized internet access, cyber threats and malicious activities.
Difference between the World Wide Web and the internet
The key difference between the internet and the World Wide Web (WWW or web) is that the internet is a global connection of networks, while the web is a collection of information or websites that can be accessed using the internet. In other words, the internet is the infrastructure and the web is a service on top of it.
The web is the most widely used part of the internet. Its outstanding feature is hypertext, a method of instantly cross-referencing text. Used in blog posts, Hypertext Markup Language (HTML) web pages, social media posts and online shopping websites, hypertext appears in a different color than the rest of the text and is often also underlined. When a user clicks on one of these words or phrases, they're transferred to the related site or webpage. Buttons, images or portions of images are also used as hyperlinks.
The web provides access to billions of pages of information. Web browsing is done through a web browser, such as Chrome, Edge or Firefox. The appearance of a particular website can vary slightly, depending on the browser used. Newer versions of a particular browser can render more complex features, such as animation, virtual reality, sound and music files.
What are the key features of the internet?
The internet has certain features that make it a powerful and versatile tool for communication, information sharing and diverse online activities. Some key features of the internet include the following:
- Worldwide availability. The internet is a global resource that's accessible to everyone. Today, most people can use the internet even if they live in the most remote and deserted parts of the world.
- Compatibility with other media types. Due to the standardized protocols and formats that it offers, the internet facilitates compatibility with various media types. This enables seamless integration and interaction across diverse multimedia such as photos, videos and audio files.
- Easy accessibility. Web browsers such as Chrome or Firefox are used to access the internet. For end users and developers, these programs are simple to use, comprehend and easy to develop.
- Affordability. The expenses associated with developing and maintaining internet services are low. However, the costs vary depending on the type of services and providers being used.
Uses of the internet
In general, the internet can be used to communicate across large or small distances, share information from any place in the world, and access information or answers to almost any question in moments.
Some specific examples of how the internet is used include the following:
- Social media and content sharing.
- Email and other forms of communication, such as Internet Relay Chat, internet telephony, instant messaging and video conferencing.
- Education and self-improvement through access to online degree programs, courses and workshops.
- Searching for jobs -- both employers and applicants use the internet to post open positions, apply for jobs and recruit individuals found on social networking sites such as LinkedIn.
- Entertainment such as streaming TV shows, movies, videos and music.
- Remote working using online collaboration platforms and messaging apps.
Security and the internet
Large amounts of information, both public and private, are collected across the internet, opening users up to the risk of data breaches and other security threats such as malware infections, ransomware attacks and phishing attempts. Hackers and crackers can break into networks and systems and steal login information or bank and credit card account records.
Internet security refers to a set of techniques and methods targeted at safeguarding online activities and transactions. Users can take the following steps to protect their online privacy:
- Install antivirus and antimalware software on devices and endpoints.
- Create difficult, varied passwords that are impossible to guess.
- Use a virtual private network or, at least, a private browsing mode, such as Google Chrome's Incognito window.
- Use secure protocols, such as HTTPS, instead of HTTP for online transactions.
- Make all social media accounts private.
- Deactivate autofill.
- Turn off the device's Global Positioning System (GPS).
- Update cookies so an alert is sent anytime a cookie is installed.
- Log out of accounts instead of just closing the tab or window.
- Use caution with spam emails and never open or download content from unknown sources.
- Use caution when accessing public Wi-Fi or hotspots.
- Regularly back up important data both offsite and on the cloud.
Additionally, there's an element of the internet called the dark web. The dark web is hidden and inaccessible through standard browsers. Instead, it uses the Tor and I2P browsers which let users remain completely anonymous. While this anonymity can be a great way to protect an online user's security and free speech, or for the government to keep classified data hidden, the dark web also creates an environment that facilitates cybercrime, the transfer of illegal goods and terrorism.
Social impact of the internet
The internet has both positive and negative social effects. On one side, people argue that the internet has increased the risk of isolation, alienation and withdrawal from society, pointing to increases in an emotional response called FOMO, or the fear of missing out. Also, there are major differences in terms of access to the internet, bandwidth, efficiency and cost. This digital divide results in unequal access to information and opportunities among individuals based on their backgrounds and other socio-economic factors.
On the other side, people believe the internet increases civic engagement, sociability and the intensity of relationships.
Whether the effects are good or bad, the internet has changed the way society interacts and connects. People are constructing social relationships based on individual interests, projects and values. Communities are being formed by like-minded individuals not only offline and in person, but through the internet and the multitude of online environments it creates and offers. Social networking sites -- like Facebook and LinkedIn -- have become the preferred platforms for both businesses and individuals looking to perform all kinds of tasks and communicate with others.
Benefits of the internet
The internet offers numerous advantages that have transformed people's lives in the following ways:
- Provides access to endless information, knowledge and education.
- Increases users' ability to communicate, connect and share.
- Allows users to work remotely, collaborate and access a global workforce.
- Gives businesses or individuals an avenue to sell and make money.
- Provides access to an unlimited supply of entertainment sources, such as movies, music, videos and games.
- Amplifies the influence of a message, enabling charities and other organizations to reach a wider audience and increase the amount of donations.
- Provides access to the IoT, which enables home appliances and devices to connect to and be controlled from a computer or smartphone.
- Provides access to health-related information and resources, letting people make informed decisions regarding their well-being.
- Allows users to save data and easily share files with cloud storage on cloud computing platforms.
- Enables users to monitor and control personal accounts instantly, such as bank accounts or credit card bills.
Without network protocols, it's impossible to access or communicate through the internet. Explore the most common network protocols and learn how they operate.
